Hello all
We have 2 different NVR devices integrated to the Sophos XG firewall Lan zone via regular network switch.
Is this type of integration without any VLAN definitions and different Ports is preferable ?
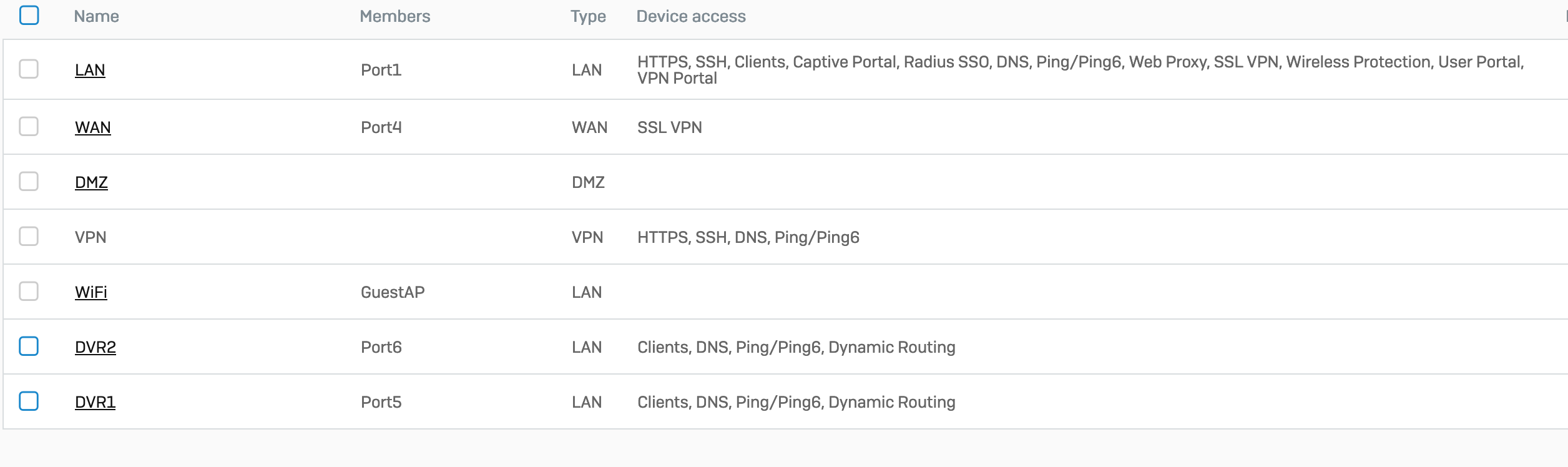
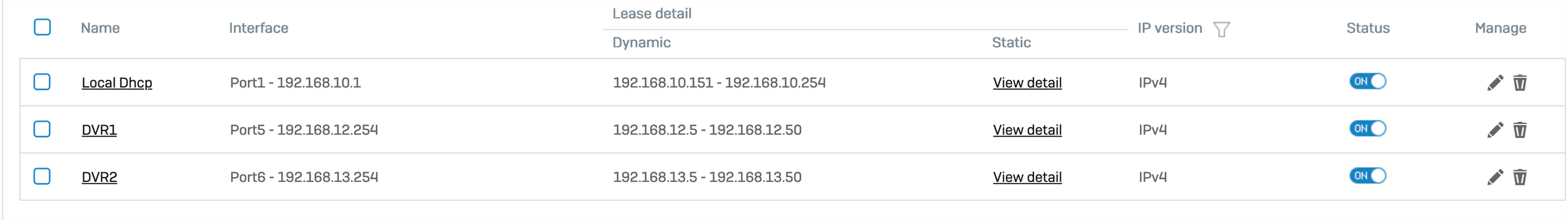
This screens are latest situation of the integration without VLAN and Manageble Switch.
Port1: Default Lan network for overall connection.
Port4: Wan connection
Port5: Direct cable connection from NVR device without any switch.
Port6: Direct cable connection from NVR device without any switch.
I tried to exclude the data flow created by NVR device from the main Lan system (port1) because of intense traffic flow of the NVR device.
As seen on the screens is there there any gap or misconfigured settings seen ?
For example IPv4/netmask settings, exception of alias or bridge definitons..

There is special Port definitions applied in this rule.
As seen in the screen there is large amount of data count flowing through the rule. Is this data -coming from the NVR- create heavy workload to the device ?

All in all
Is this approch correct way to do the job for seperating the networks ?
Thanks all.
This thread was automatically locked due to age.


