Hello,
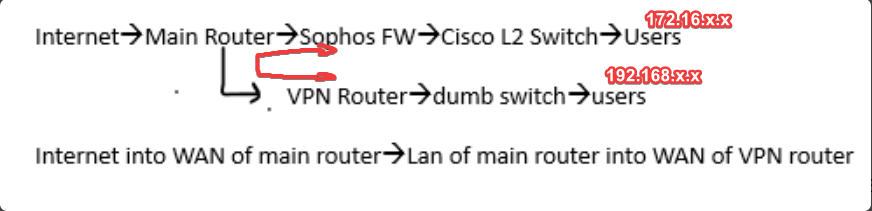
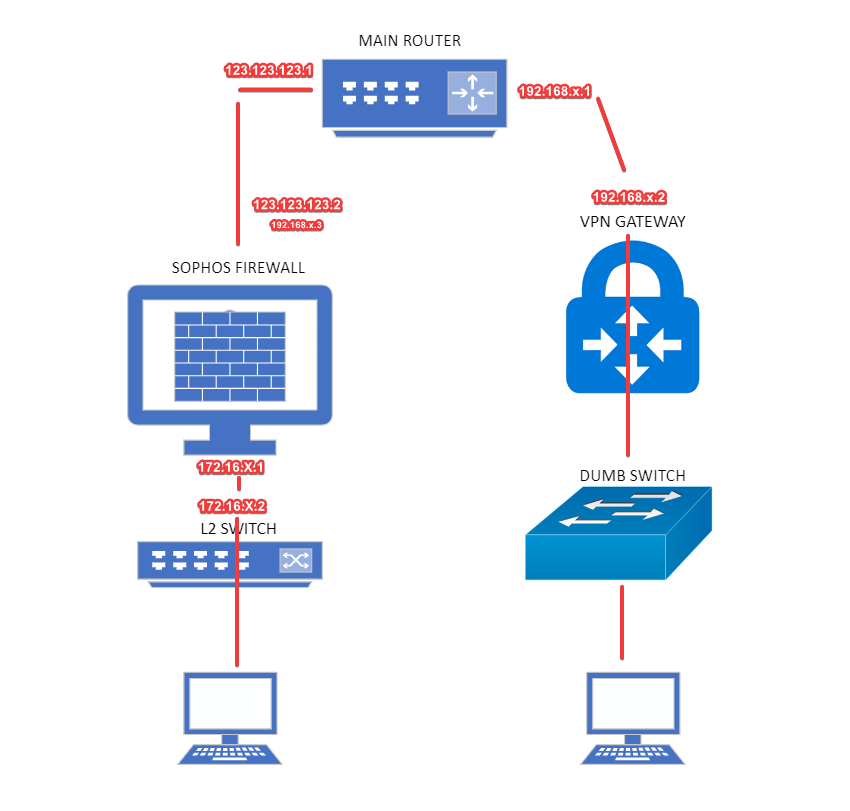
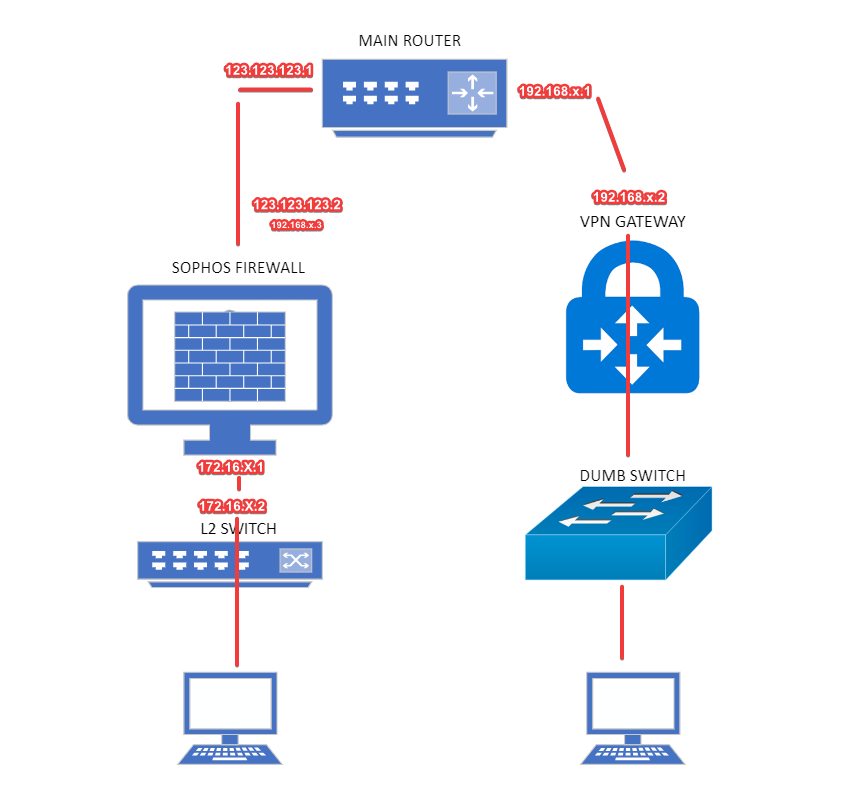
My main network is 172.16.x.x and I have a VPN network using 192.168.x.x. The two networks don't 'talk' to one another but I would like to change that through the use of a VLAN.
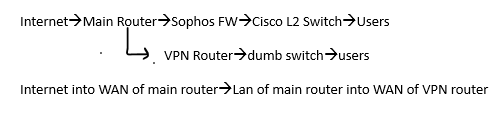
First off, is that even possible to where I can access either network from the same PC? For example, I'm logged into my 172.16 network through my main router through ethernet connection. I cannot access my VPN 192.168 network unless I connect to it wirelessly (I have a VPN router with DHCP turned on that manages this network). This VPN router does connect to my main router that accesses internet. The LAN of main router connects to the WAN of VPN router.
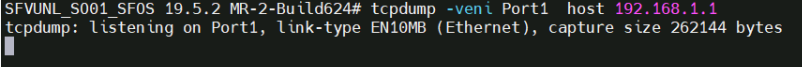
So I'm using Sophos Firewall that protects my main network (172.16) but the VPN 192.168 network bypasses the firewall as it connects directly to main router. My main router connects to Sophos FW and then Sophos FW connects to a Cisco L2 switch to which everything else is connected.
Since L2 switch and main router can't do what I want concerning VLAN (I think I need a L3 switch to set up VLAN), maybe the Sophos FW can. So my theory is that if I connect my VPN router to a port on Sophos FW that is using VLAN, I should be able to connect to this network from any PC on main network. So essentially, my main PC with IP address of 172.16.x.x talks directly to another device on VPN network that has a 192.168.x.x IP address.
Is this even possible? I purposely set up the each network with the different IP ranges to avoid confusion between the two.
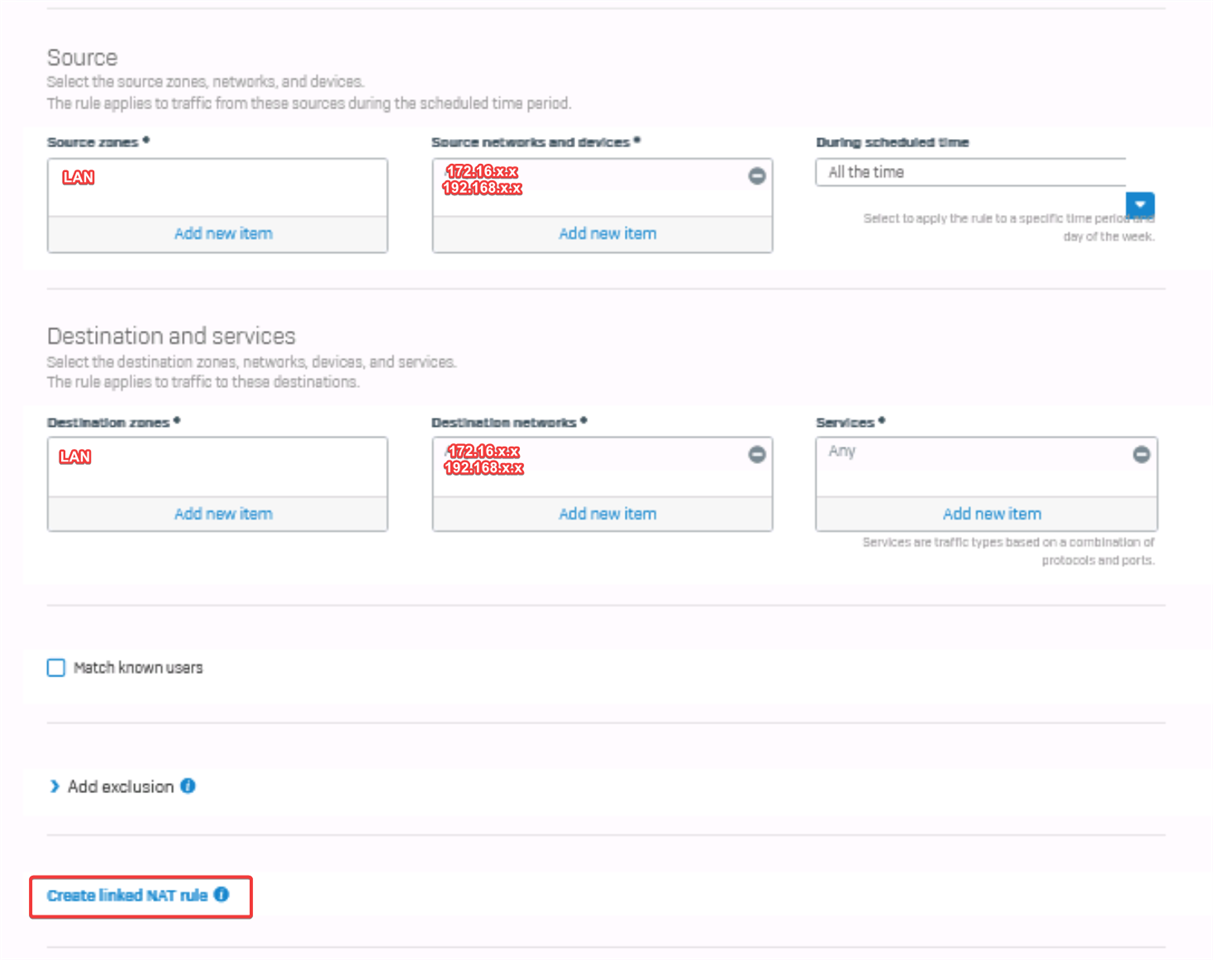
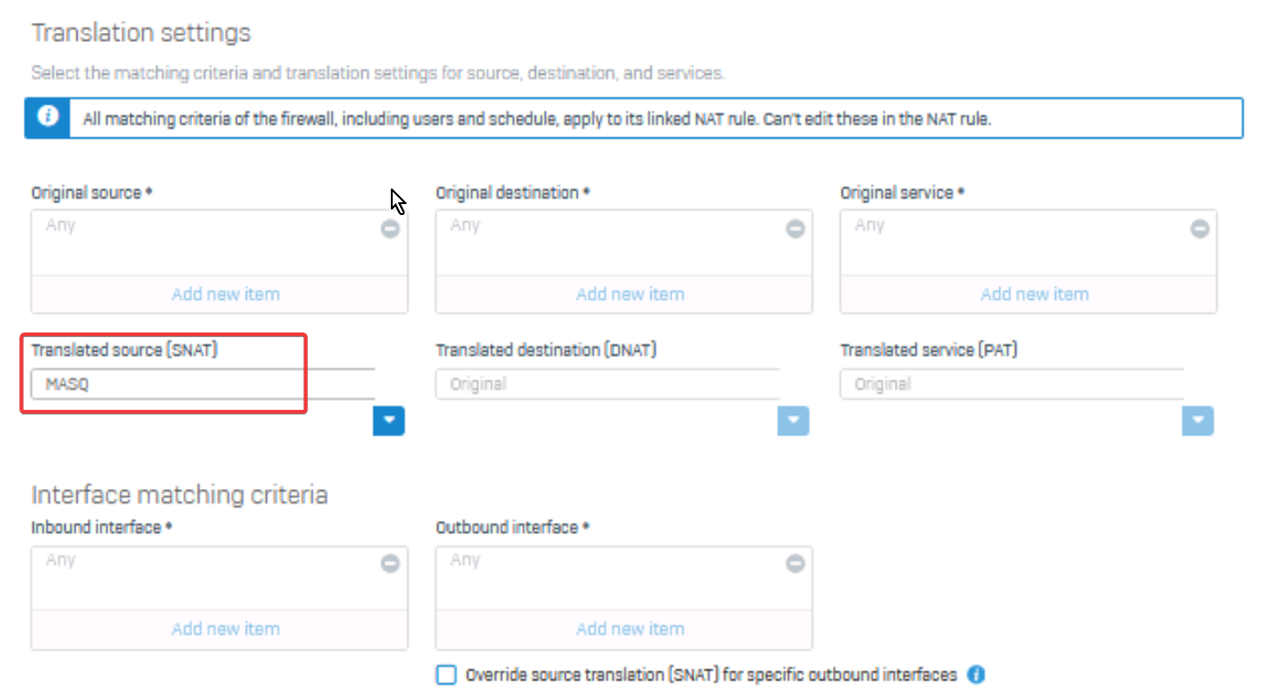
If possible to do this, would need to know specifically how to set up VLAN, Firewall rules and any NAT config to make this work.
Thanks for any help provided.
This thread was automatically locked due to age.