Good evening!
I have Remote SSL VPN setup, and I can connect to it no problem. The network address for these clients are 192.168.3.0/24. Below are my three policies for allowing traffic from the VPN zone to the WAN, LAN, and DMZ zones.
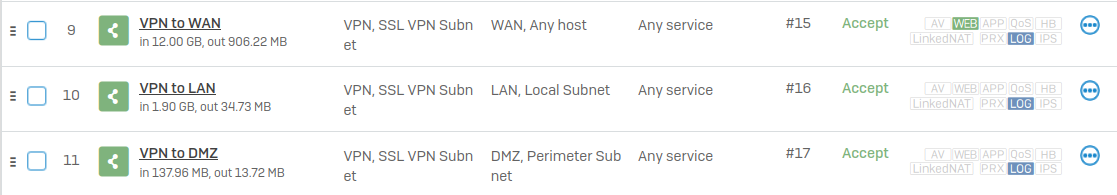
Here are my gateways:
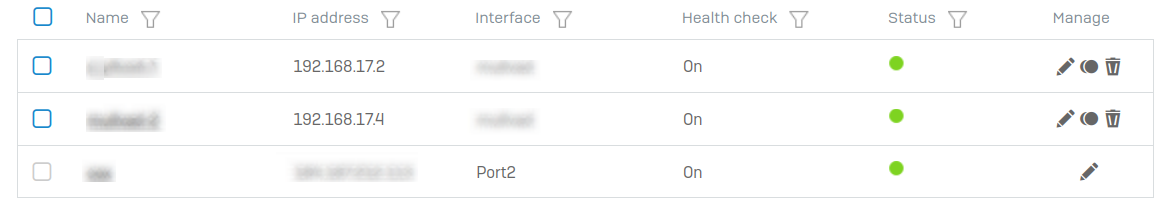
The top two gateways are on a separate VLAN (6). They are connections to a VPN provider in different locales. Let's call them VPN1 and VPN2. The third gateway is my ISP gateway, let's call that ISP1.
Below is my SD-WAN configuration. Everything works great, except for #6. That's the rule where I want to route traffic from the SSL VPN to VPN1 and VPN2.
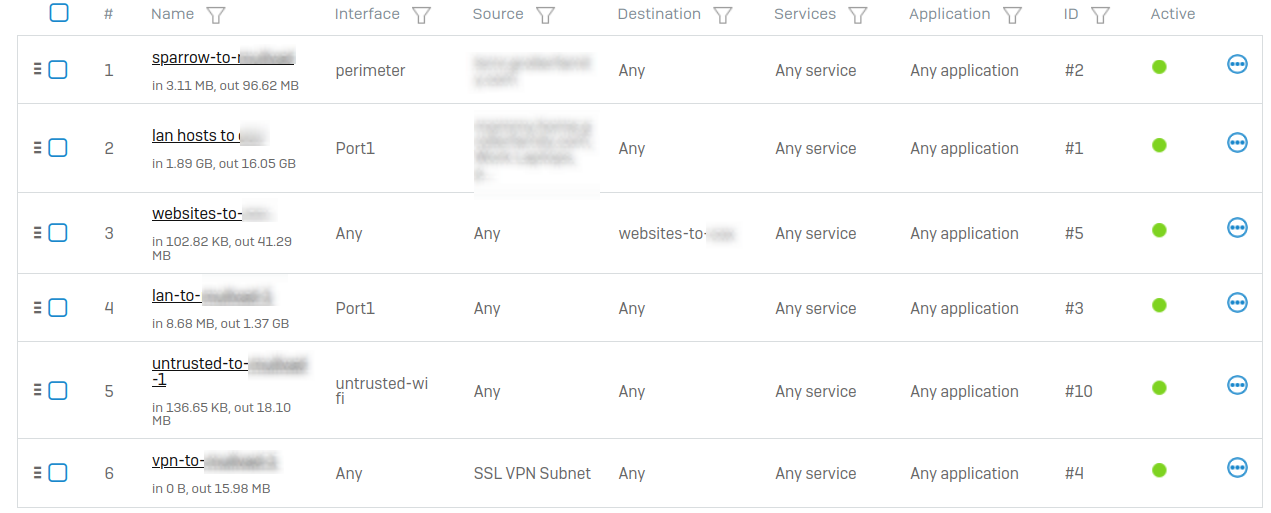
Here's that rule in detail:
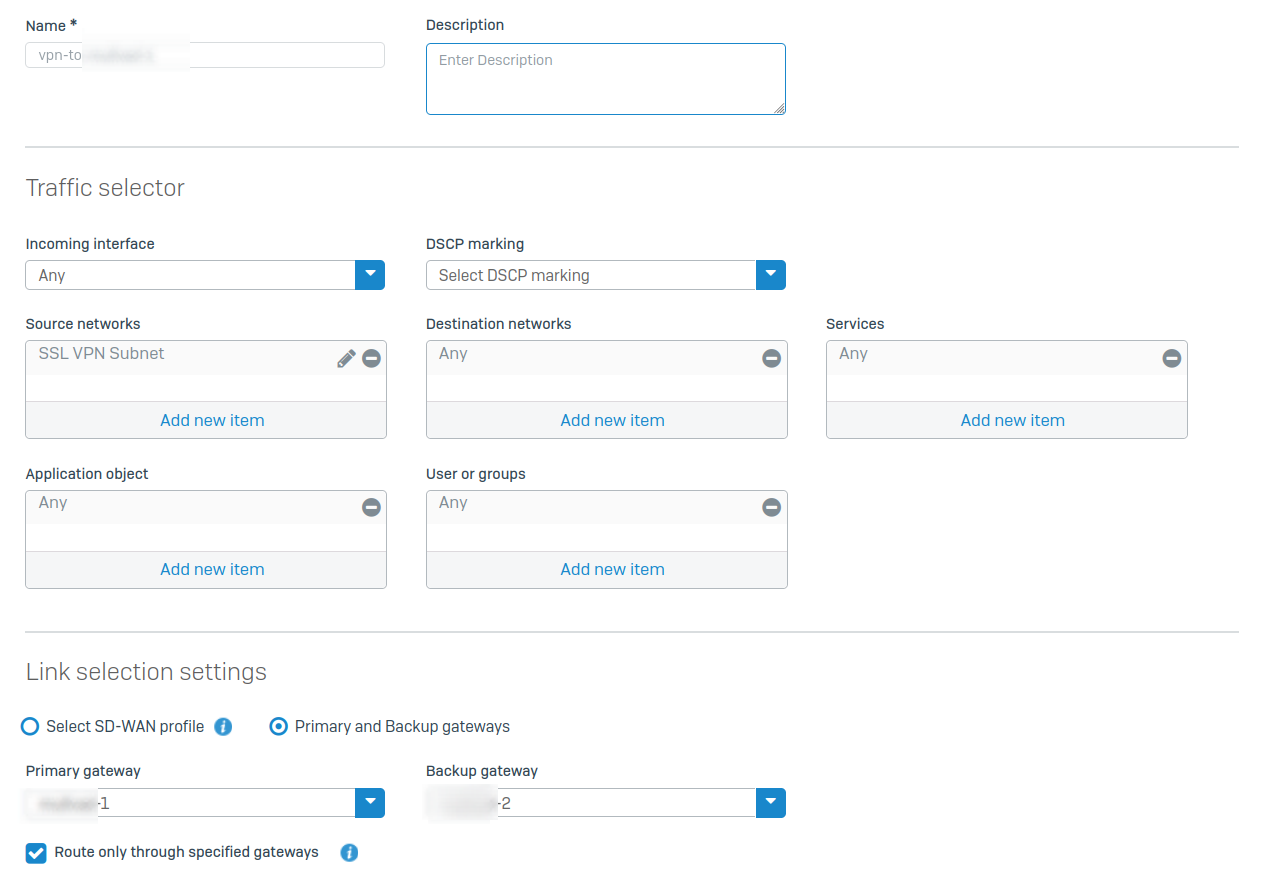
When I attempt to access any web page while connected to the SSL VPN, it hangs for a REALLY long time and eventually times out. If I change "Primary Gateway" to ISP1, then everything works fine. So, I know the rule is matching... but something about routing traffic to VPN1 and VPN2 is failing.
I've spun my wheels a lot on this and could use some ideas.
This thread was automatically locked due to age.


