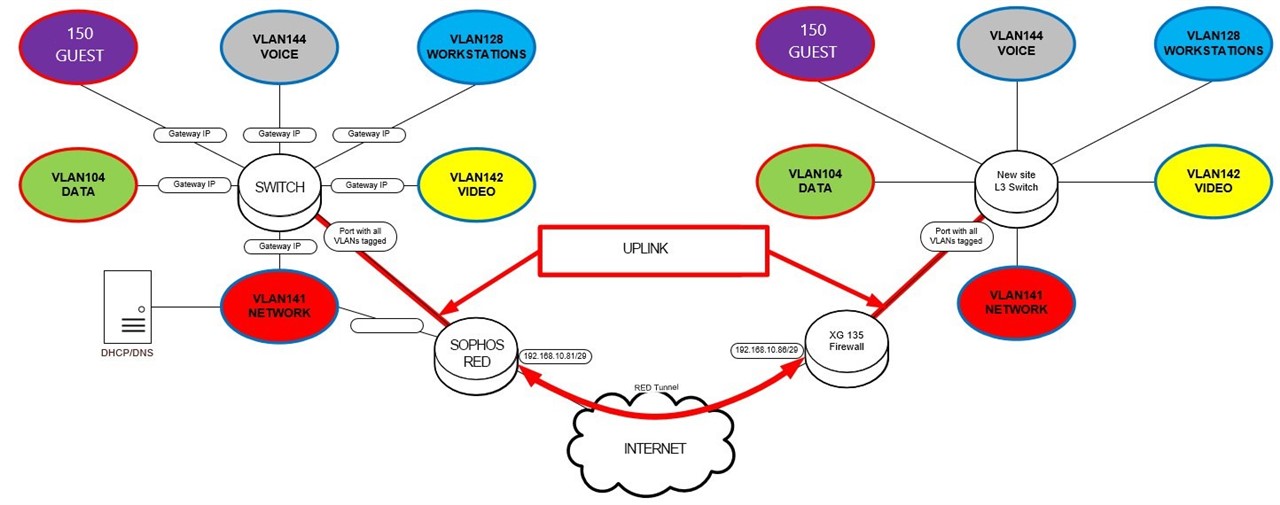
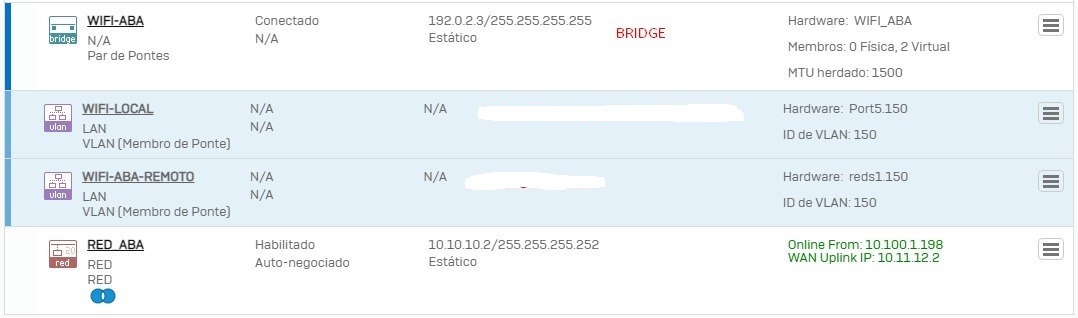
Hello, I have the following scenario, I need to transport some VLANs that are on my core switch L3, behind the RED (Appliance), I have already tried to put the Firewall interface marked with the VLANs that I need, in Sophos I grouped the VLANs in a bridge, station behind RED gets ip from guest VLAN but does not browse.
I know it's not a good practice, but I need the Hotspot of my guest network, also in the branches.
This thread was automatically locked due to age.


