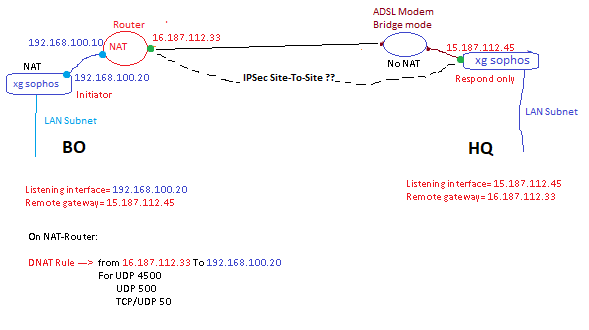
Hi all,
I have this topology (look at picture please), and i need to configure vpn ipsec site to site between HQ and BO
HQ XG is connected to ADSL Bridge mode, but BO XG is connected to Fiber ONT (router mode)
The two site have already static public ip
what is the best way to configure correctly this IPSec VPN
Thanks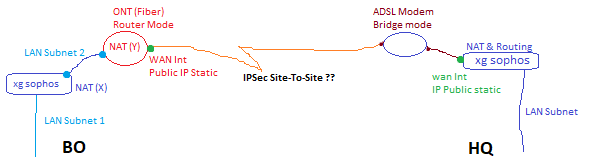
This thread was automatically locked due to age.