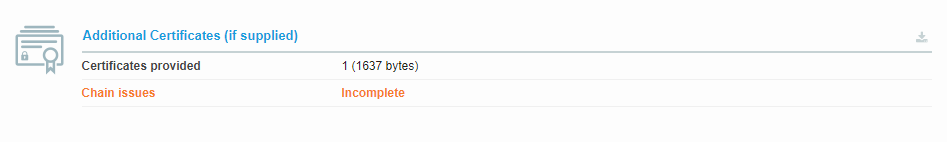
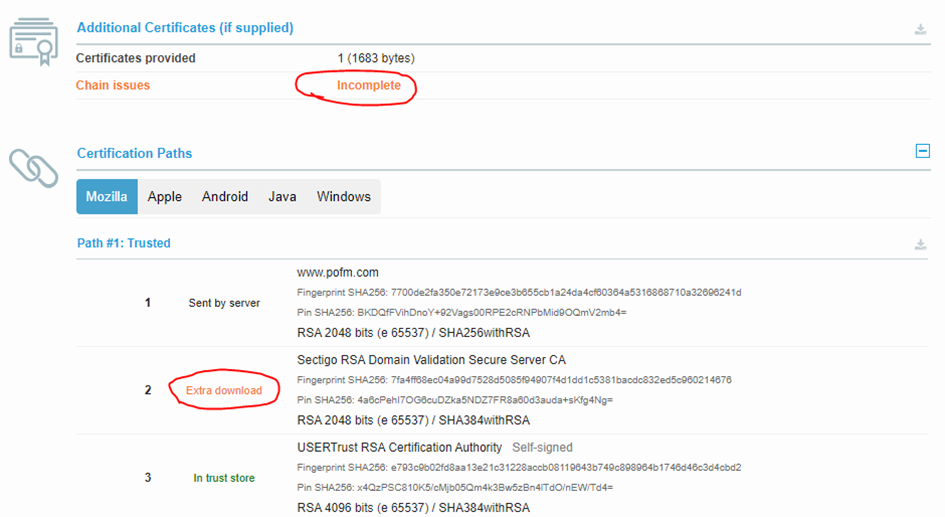
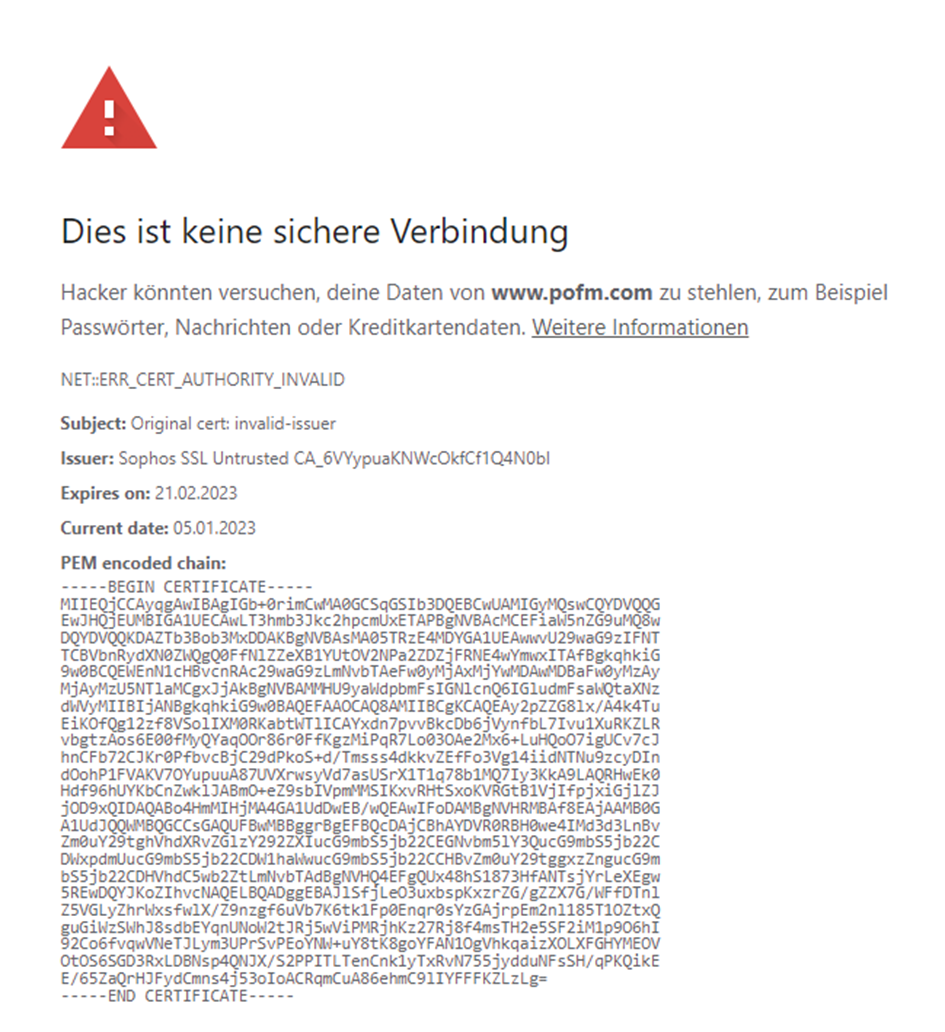
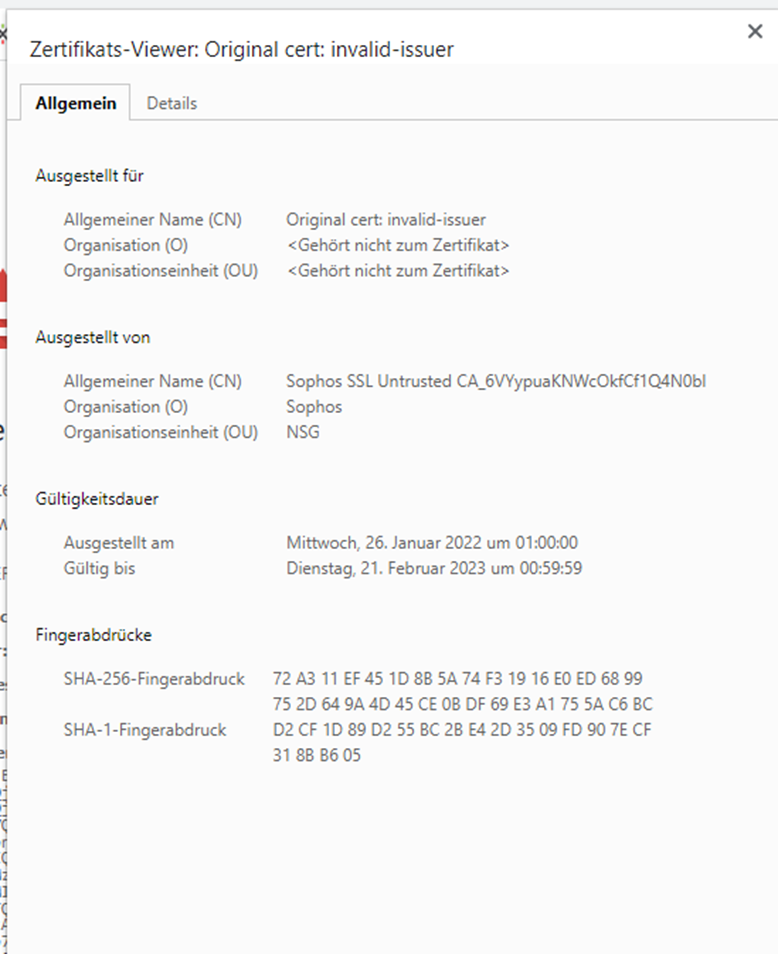
Release Post: Sophos Firewall v19.5 is Now Available
Old v19.0 MR1 thread: Sophos Firewall: v19.0 MR1: Feedback and experiences
EAP Sub thread: SFOS v19.5 Early Access Program (Read Only)
EAP 19.5 Thread: Sophos Firewall: v19.5 EAP1: Feedback and experiences
This thread was automatically locked due to age.