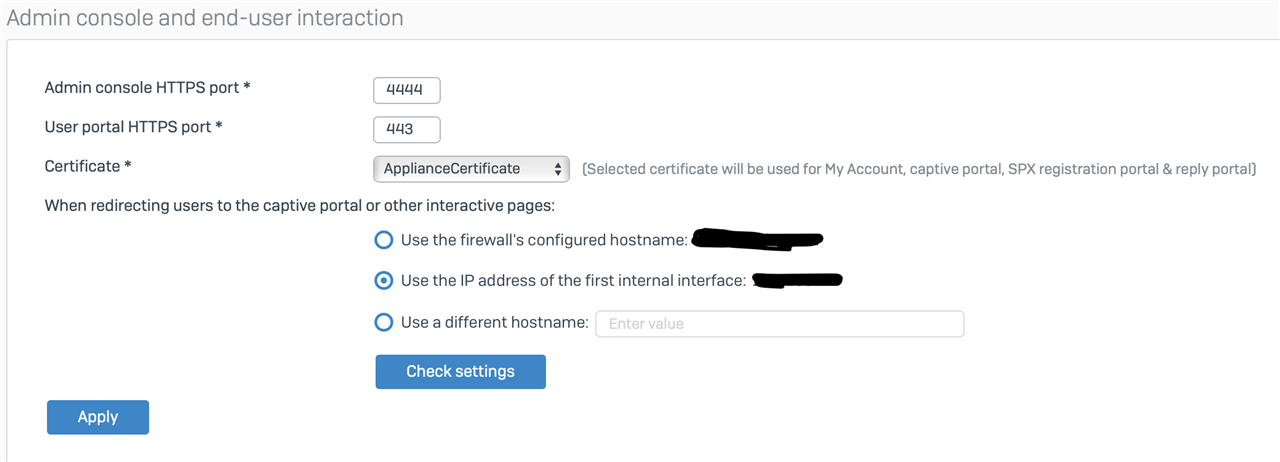
Error messages and interaction pages from the XG have to refer to a specific address (XG's first configured IP, hostname lookup, etc), which works fine for hosts behind the firewall, but for VPN clients it causes problems.
For example, let's say your firewall's first configured interface is 192.168.1.1. So any IPS warnings that appear come from 192.168.1.1 which works fine from within the firewall: you are able to retrieve the warning page. (You may have certificate trust issues, but that's a different matter.)
BUT if you're on the VPN, you may actually have a 192.168.1.1 as your LOCAL (i.e. local at the remote end where you are) gateway/firewall which your client machine can't differentiate from the far end's (internal) 192.168.1.1, so the warning will always fail since the local 192.168.1.1 (to the remote VPN client) of course will not serve up the warning HTML. You can't fix this from the remote (VPN SSL Client) end, since it will actually need to communicate with that LOCAL (at the remote end) 192.168.1.1 to get anywhere. At least I think that's the case.
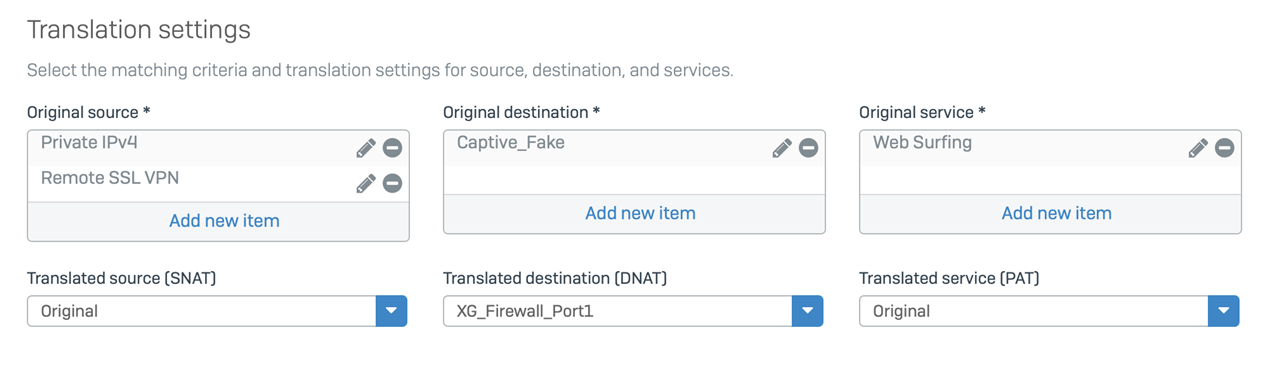
So what's the proper way to handle this? I'm imagining a NAT rule that covers traffic from 192.168.1.1 (XG) to the VPN zone and does a MASQ? I'm afraid to try it right now, since I'm remote and using the VPN and can't afford to screw it up. At the same time, it's very difficult to test when you're onsite since 192.168.1.1 goes to the correct place.
In particular, I'm afraid that a close-but-no-cigar NAT rule would NAT all traffic to the VPN. Or maybe I've got it backwards. And does the warning HTML come from 192.168.1.1 or does it just use that IP as some kind of referral address?
I guess another way around it is to pick a LAN IP range that you think no one else will ever have at the remote end. (Probably avoiding 192.168.1.0 and 192.168.0.0 are a good idea for most consumer "routers", but you can't anticipate everyone else in the world's LAN addresses.)
This thread was automatically locked due to age.