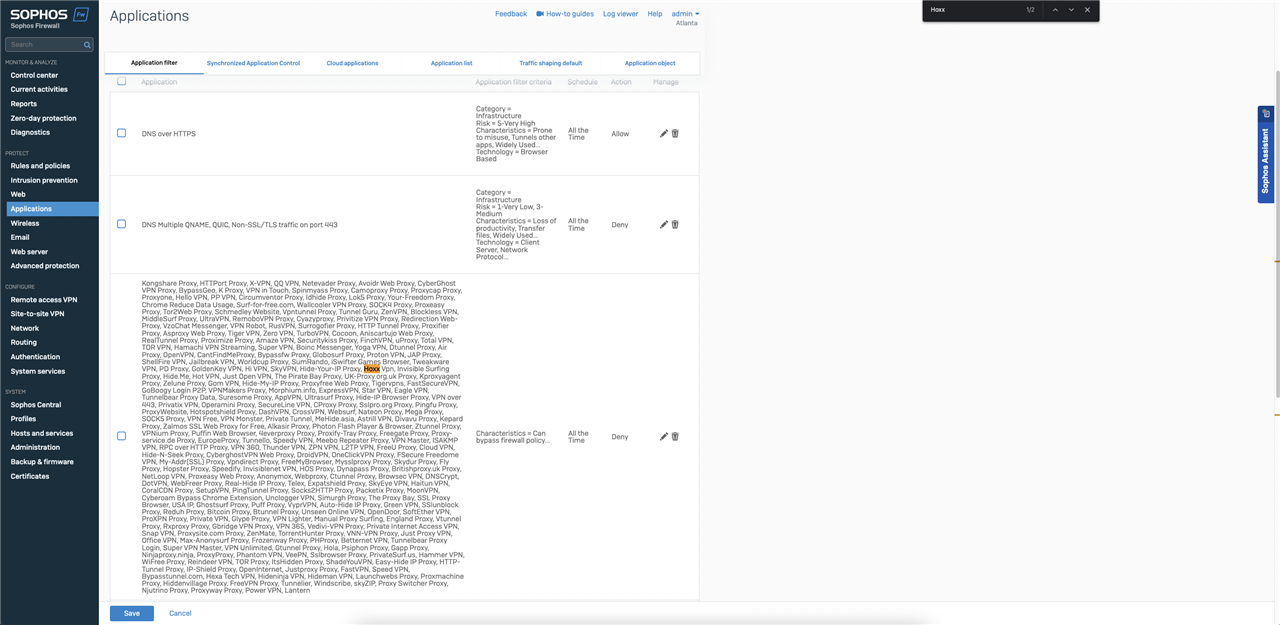
Hi guys,
I am unable to block the Hoxx VPN extension on firefox. I followed the Application filter recommended settings for better application detection (https://soph.so/WtpQzU). The application uses port 80/443 for VPN servers. Sophos XGS is unable to block the VPN.
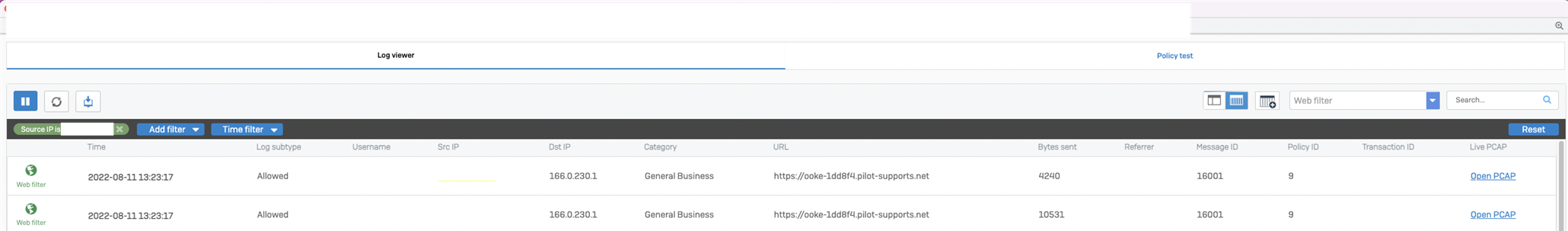
Web Filter:

This thread was automatically locked due to age.