Hi All,
Recently one of our clients who have a server setup with a Sophos XG210 at their HQ have opened up a new branch that only has desktops and no servers. Machines are connected to a domain and a few of the users from head office have moved to the new branch. We have installed a XG106 and have setup an IPSEC S2S connection using the Sophos guide.
After speaking to Sophos support they have advised that we do not need to setup the routes as mentioned in https://support.sophos.com/support/s/article/KB-000035830?language=en_US
We have been since experiencing an issue where things are fine for a few days and then randomly one of the users is unable to access the main DC at HQ, browsing to network shares just hangs, to get around this we can change the IP address on the machine to a new static and things are then fine again but a few days later it will either happen to the same person or a different person. The strange thing is that the same user can still access the terminal server located at HQ and the other servers, they just lose access to the main DC. Also if we connect to the SSL remote VPN everything works fine.
The setup is:
Site 1: HQ: XG210, Lan 192.168.100.1, Network 192.168.100.0/24, Main DC (192.168.100.5) located at this office
Site 2: Branch: XG106: Lan 192.168.102.1, Network: 192.168.102.0/24 No Servers at this location only domain joined PC's
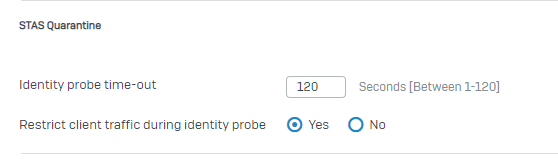
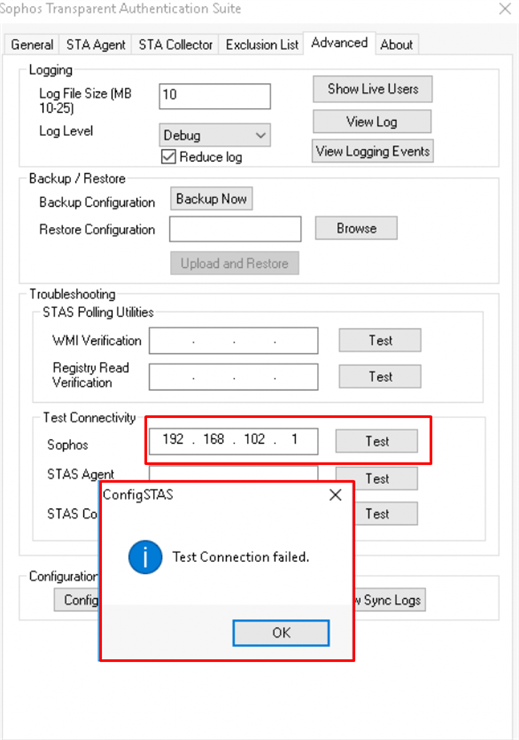
- Forgot to mention that we have STAS setup aswell.
Thank you in advance to anyone who has any ideas.
This thread was automatically locked due to age.