Hi all,
Shall we start this new thread with the looks and feels of XG v18 MR-3?
community.sophos.com/.../xg-firewall-v18-mr3
This thread was automatically locked due to age.
Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Hi all,
Shall we start this new thread with the looks and feels of XG v18 MR-3?
community.sophos.com/.../xg-firewall-v18-mr3
Hi, good start.
installed and running okay.
Bug that was supposed to be fixed in this version.IMAP scanning has not been fixed, still the same issue that imap rejects the CA that is acceptable by smtp/s scanning.
ian
XG115W - v20.0.3 MR-3 - Home
XG on VM 8 - v21 GA
If a post solves your question please use the 'Verify Answer' button.
Hi All,
good start as well,
1. had a customer who has been having issues with Client IPSec VPNs disconnecting throughout the day, no longer happening since upgrade!
2. My home unit now reacts better and is a lot smoother as well.
the only bad point is that another customer is still having issues with a S2S IKE v2 VPN disconnecting throughout the day, even after upgrade, and when there is no traffic on the connection.
Between the XG210 and a Draytek 2862 - both on latest firmware - if anyone has any ideas I would love to hear them (as I have now resorted to using support, which could be months before it is even looked at)
XG & UTM Architect (Systems: XG v18 & UTM 9.7 - Virtual, HW & SW)
Curious enough to take it apart, skilled enough to put it back together, Clever enough to hide the extra parts when I'm Done!
Hi All, here is the config which is set. The UTM is not problem at all but the XG just will not stay pinned up.
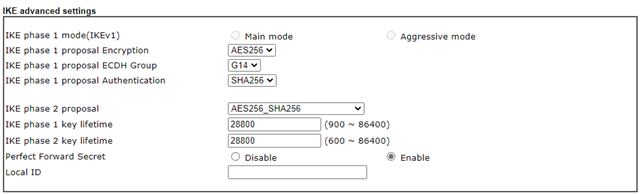
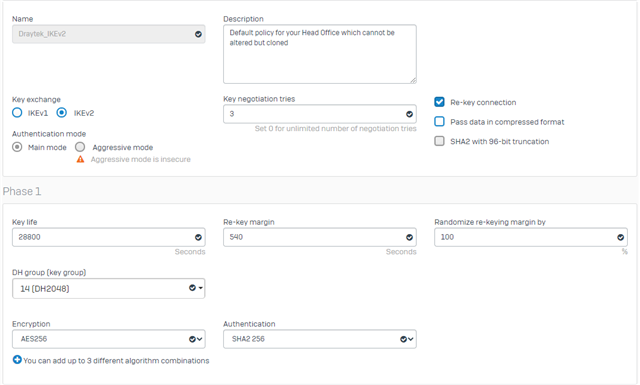
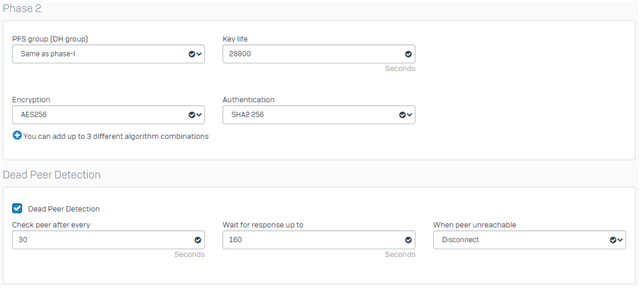
here is the Draytek 2862 config, I have tried both IKEv1 and IKEv2 both have the same problem.
also the IKE phase 2 key lifetime is set at 28800 as support asked me to change it
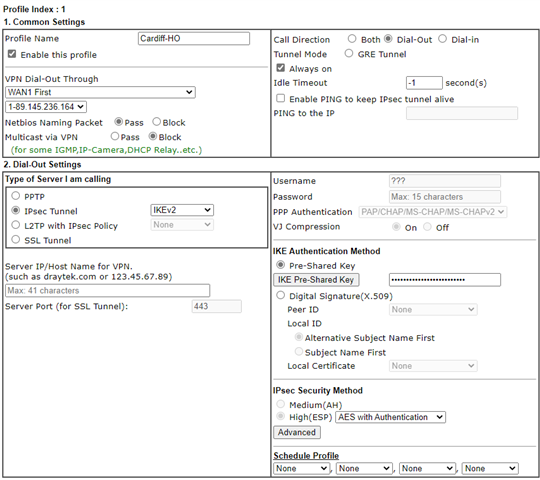
Here is the XG v18 MR3 policy
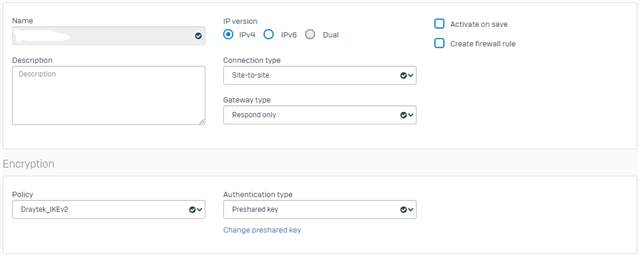
support are looking at it, but there is not much in the way of a fix only one comment, and trying to wait for them to get back is becoming tedious.
any help appreciated.
XG & UTM Architect (Systems: XG v18 & UTM 9.7 - Virtual, HW & SW)
Curious enough to take it apart, skilled enough to put it back together, Clever enough to hide the extra parts when I'm Done!
Hi Argo
Most of your settings are the same as mine, with the exception of some of the timeout values.
The main difference I can see is in your IPSec policy - Dead Peer Detection. If I understand correctly, with no traffic, this will cause your VPN to disconnect. Maybe try disabling and see if that resolves your problem.
BTW, I feel your pain with Sophos Support - I can't get Radius authentication to work across my VPNs since replacing a Sonicwall with an XG. Response from support has been appalling!
I will try this, although would the disconnect happen after 8 hours or the time on the DPD?
XG & UTM Architect (Systems: XG v18 & UTM 9.7 - Virtual, HW & SW)
Curious enough to take it apart, skilled enough to put it back together, Clever enough to hide the extra parts when I'm Done!
Hello Argo,
the lifetime of Phase I and Phase II keys cannot be the same. The key life for Phase I is recommended to be at least twice as long as for Phase II.
Personally, I use a lifetime 7800 seconds for Phase I and 3600 seconds for Phase II. It is important that the lifetime for Phase II is not an integer multiple of the lifetime for Phase I. In this case, the multiple is 2.166666666666667.
Try these times and I think the IPsec tunnel will be stable and functional.
The setting for Dead Peer Detection has no effect on the stability of the IPsec tunnel in this case.
Regards
alda
well it is still yo-yoing even after changing the DPD setting, I have now changed the key lifetimes to your settings (although this is the first time as they always just work).
at the moment I am willing to try anything as support communication is going downhill
I will keep you updated
XG & UTM Architect (Systems: XG v18 & UTM 9.7 - Virtual, HW & SW)
Curious enough to take it apart, skilled enough to put it back together, Clever enough to hide the extra parts when I'm Done!