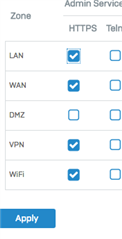
I have set up a iPsec VPN between 2 sites (Site A 192.168.99.x, Site B 192.168.1.x)
The VPN works fine and I can access servers on SITE B from SITE A via RDP connections using local IP's
However If I try to access the XG device at SITE B (https://192.168.1.3:4444) from SITE A it will not connect. - I have also found other connections on SITE B are also not found including the Sophos Firewall Manger device (hardware). I can ping these device with no problem from SITE A -> SITE B - very strange ?
Running ( XG210 (SFOS 17.1.1 MR-1) )
This thread was automatically locked due to age.