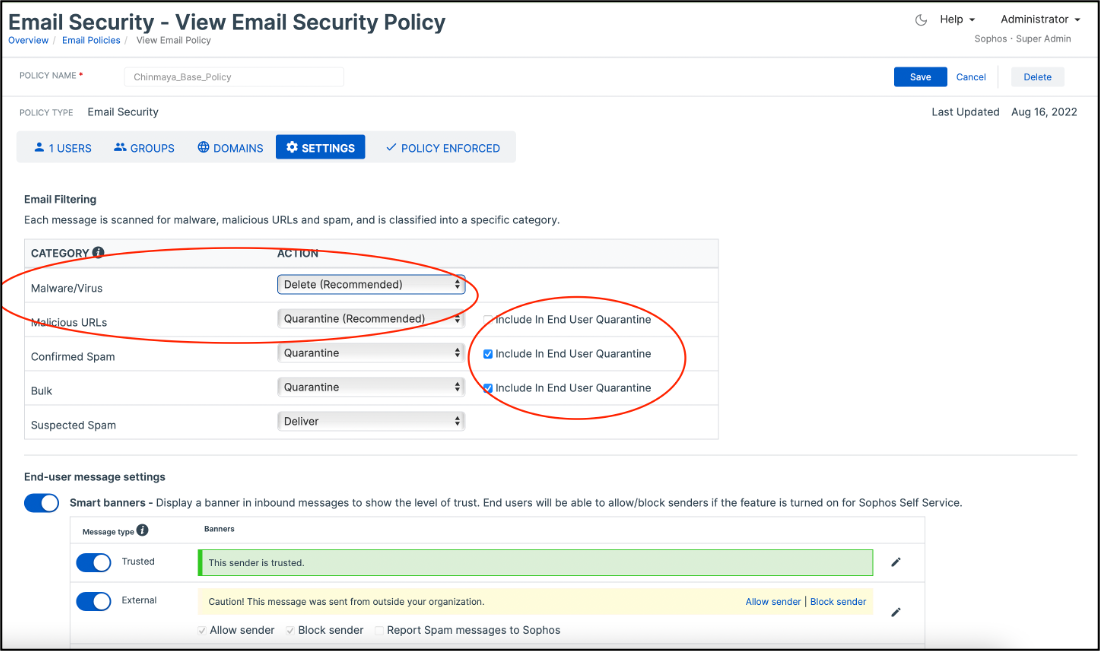
We are happy to announce the release of the policy granularity enhancement, “Enhanced Malware Policy”, which enables Sophos Email admins to configure “Quarantine” action for emails detected as Malware/Virus, Malicious URLs, or the emails detected by Intelix as malicious.
Previously, the malware/virus emails were deleted by Sophos Email without allowing the admins to review those. Also, the emails with malicious URLs were always quarantined, and admins had no option to change this behaviour. With this enhancement, the admins can now configure whether they want to ‘quarantine’ or ‘delete’ malicious emails and take different actions on emails with malicious URLs. Admins can review these malicious emails in the quarantine list, and “release” the emails if they think they have been detected incorrectly.
Additionally, if admins configure the “Quarantine” option for certain types of emails, they will have an additional option to configure if they want these emails to also go to the End User Quarantine List. This option is available for all types of emails except “Malware/Virus”, i.e.,
- Malicious URLs
- Confirmed Spam
- Bulk
- Suspected Spam
- Intelix Malicious
- Intelix Suspicious
- Sender checks (DMARC/SPF/DKIM/Header Anomalies)
- Unscanned Emails
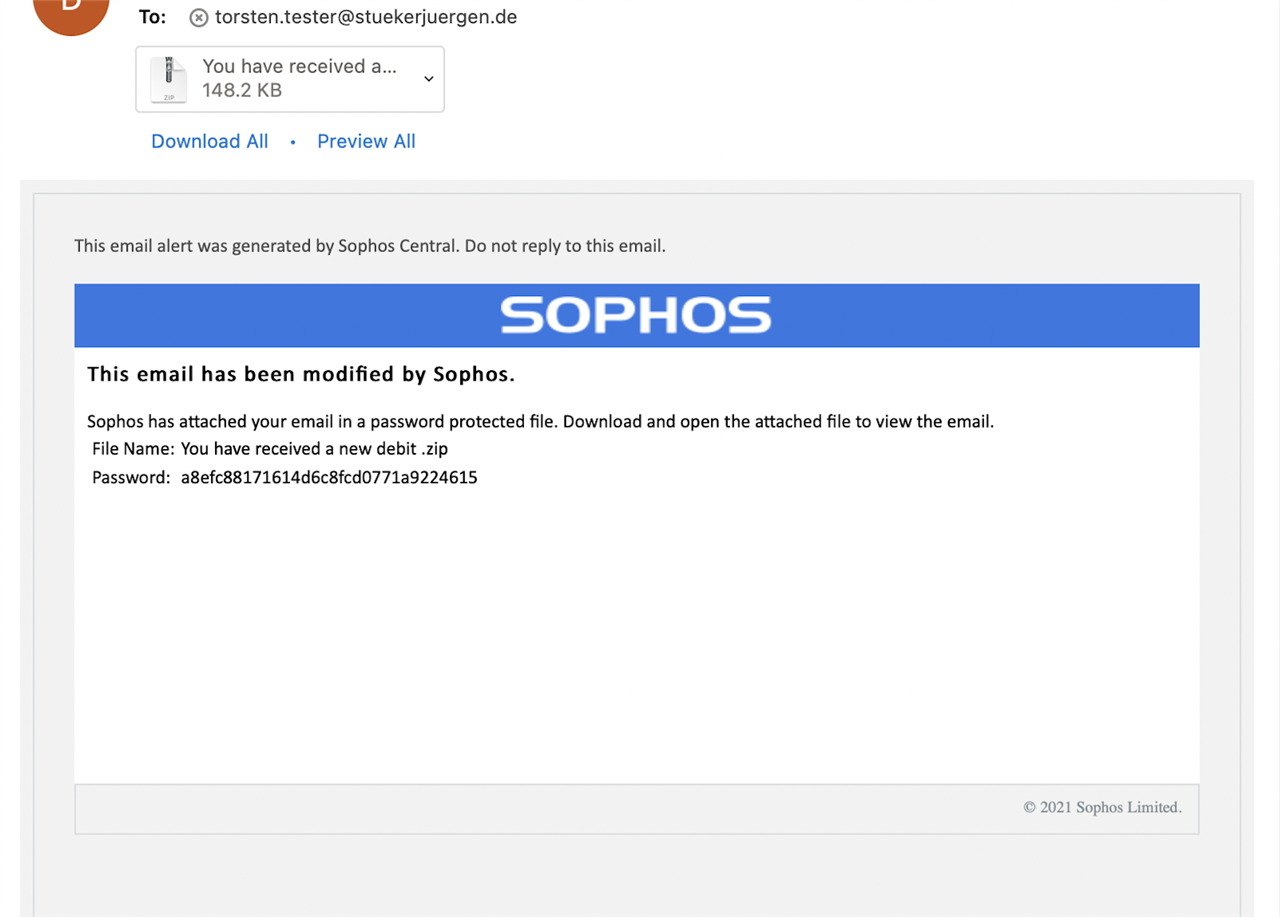
Finally, if an admin releases a quarantined ‘Malware/Virus’ or an ‘Intelix Malicious’ email, they will be given a confirmation message, and an option to submit the email to Sophos Labs as “Not Malicious”.
Also, for security reasons, when such emails are released, the end users will receive a new email with the original malicious email attached as a password-protected zip file. This new email will have the password to open the zip attachment.
The ‘release’ behavior for other types of quarantine emails remains unchanged.