What’s new
We have released several enhancements in admin quarantine. We have also enhanced policies in Sophos Email to support cloning of any policy.
Watch the video attached at end of this post to familiarize yourself with the enhancements.
Applies to the following Sophos products
Sophos Email
Admin Quarantine
Strip or Reattach email attachments
You can strip one or more attachments from a quarantined email before you release a copy of the email. If a rule in Data Control policy is applied on an email to strip its attachment, then the original email is saved in the quarantined and a copy of the email without the stripped attachment is delivered to the recipient. You can reattach the attachment to the email in quarantine by clicking on the link as shown in the screenshot below and then release it.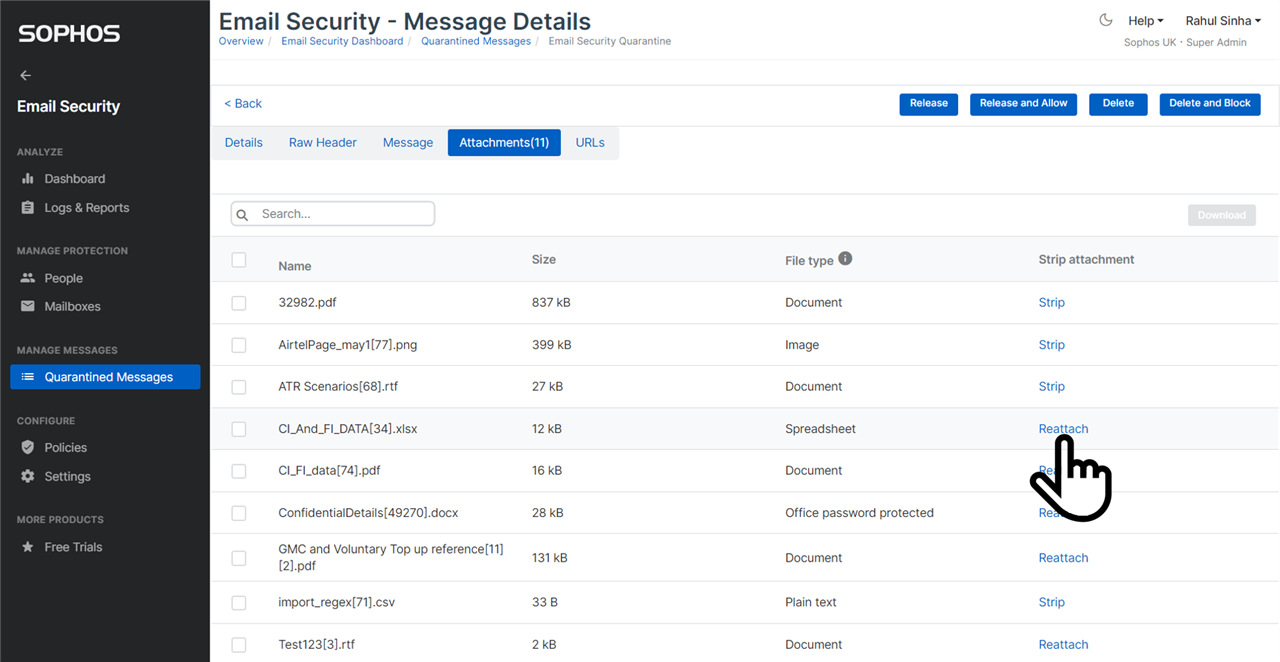 The original email is retained in the quarantine, till it is released with all its attachments attached. Note, every email is retained in admin quarantine for 30 days only.
The original email is retained in the quarantine, till it is released with all its attachments attached. Note, every email is retained in admin quarantine for 30 days only.
Download attachments
You can now download one or more attachments of a quarantined email, as shown in the screenshot below.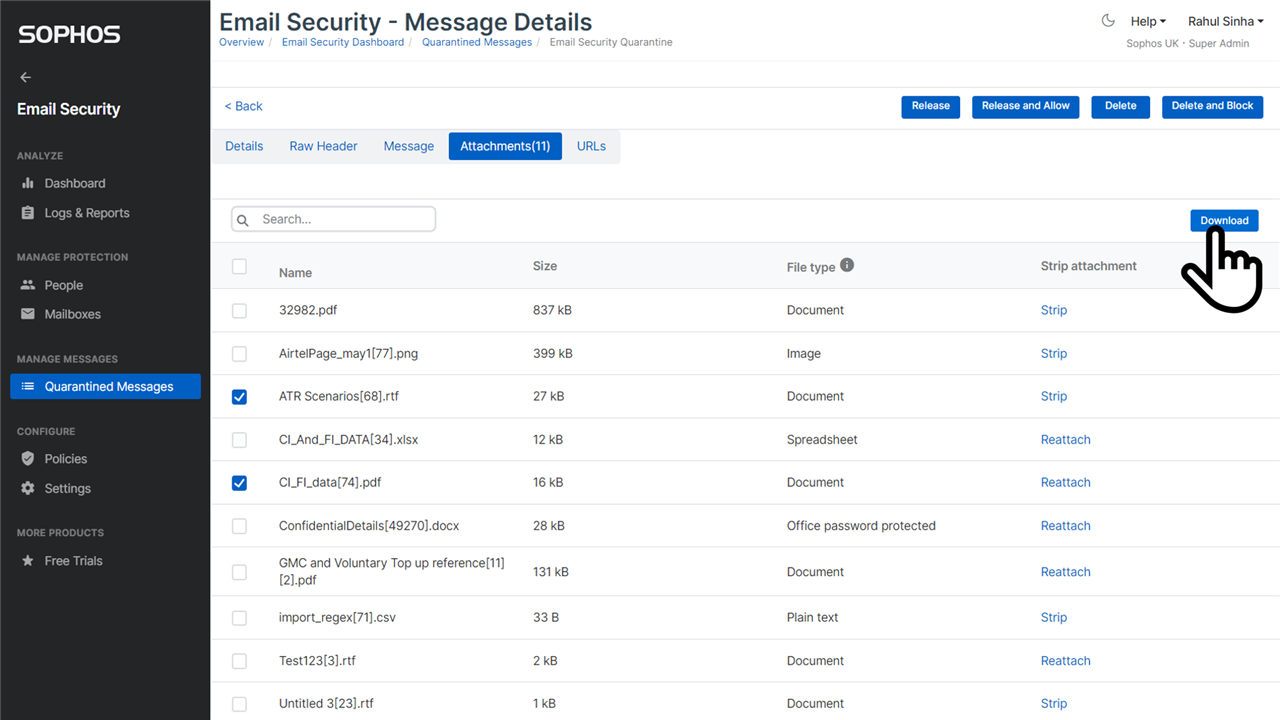
Scan quarantined email with Intelix
You can submit a quarantined email for Intelix scan, by clicking on the button shown in the screenshot below.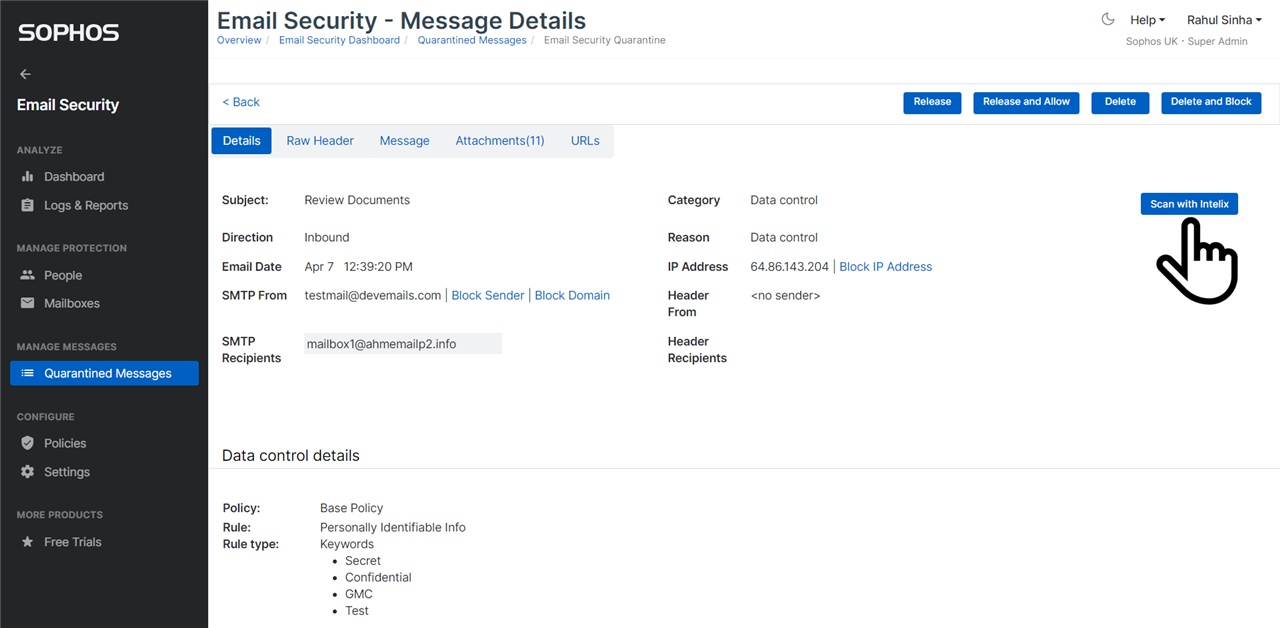
After you’ve submitted the email for Intelix scan, you can view Intelix scan report, by clicking on the link shown in the screenshot below.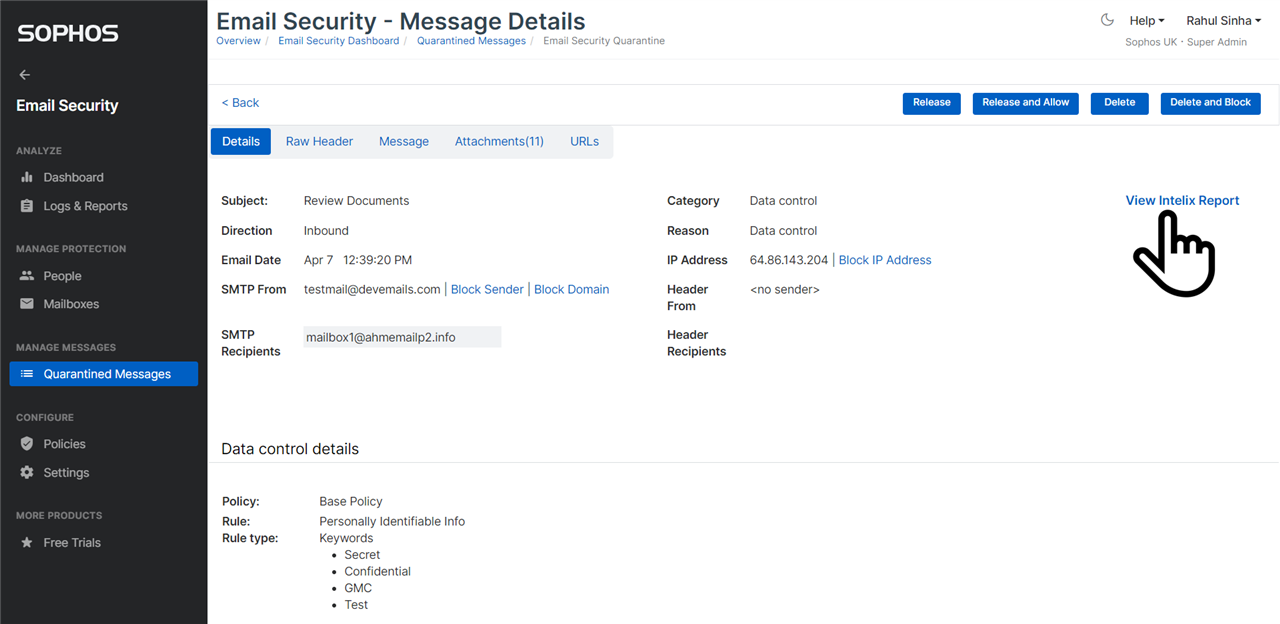 Also, if an email was already scanned by Intelix before it was quarantined, then you can navigate to the report by clicking on the link.
Also, if an email was already scanned by Intelix before it was quarantined, then you can navigate to the report by clicking on the link.
Clone policy
You can clone a Sophos Email policy by clicking on the button highlighted in the screenshot below. When you clone a policy, the new policy created is added just above the policy being cloned. By default, the cloned policy is set to not be enforced to prevent it from being applied accidentally. You should modify the cloned policy to suit your needs, before you enforce it.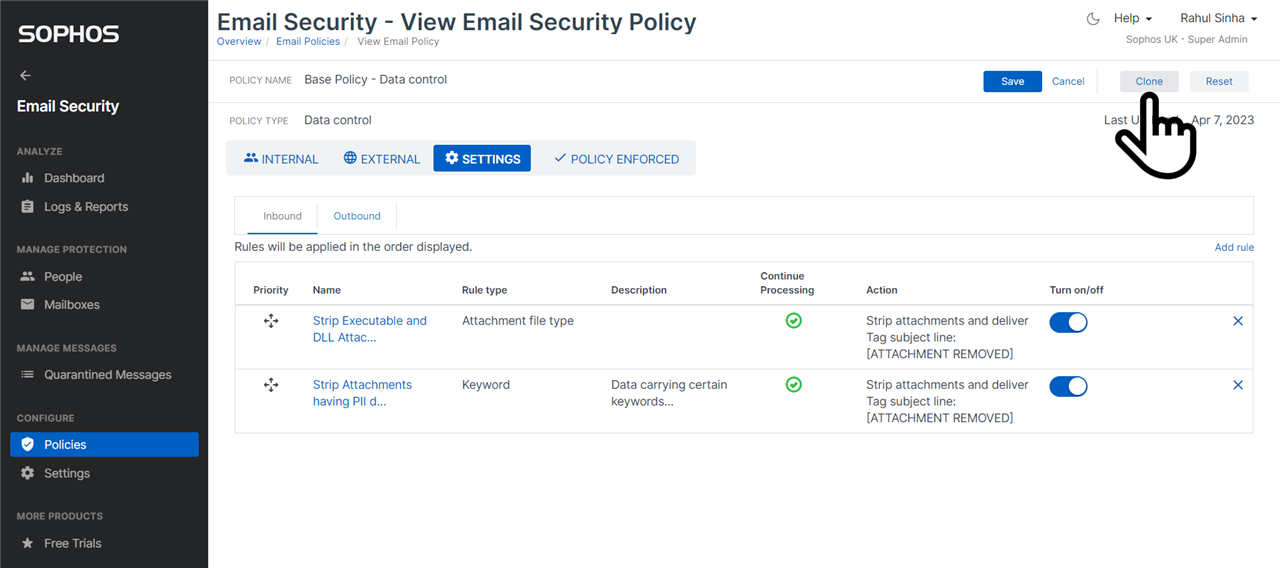 Note: When you clone the base policy, no user, no group, and no domain is selected in the cloned policy. You must select the users, groups, or domains in the cloned policy before you enforce it.
Note: When you clone the base policy, no user, no group, and no domain is selected in the cloned policy. You must select the users, groups, or domains in the cloned policy before you enforce it.
Watch the demo video


