Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended read describes a certain user situation and troubleshooting suggestions if the SSL VPN Client download from the User Portal is incorrectly presented as a 0-byte download.
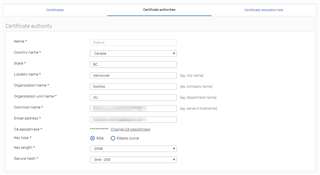
Ensure the default/custom CA details are properly configured
- Is a custom CA being used?
- If so, does the issue occur if the default self-signed certificate is used instead?
If using the default self-signed certificate resolves the issue, verify the custom CA is properly assembled (proper signing CA, and so on.)
User Certificate Generation is failing
To regenerate an individual user's SSL VPN certificate, you’ll have to go to the Sophos Firewall GUI and delete their user certificate (Certificates > Certificates)
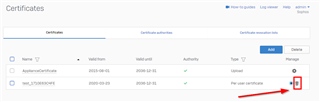
- Their user certificate will be regenerated the next time they sign into the Sophos Firewall User Portal and download their SSL VPN Configuration.
If you’re still experiencing issues, you can regenerate the Default CA by navigating to Certificates > Certificate Authorities.
This will force the regeneration of all SSL VPN user certificates and restart the SSL VPN service.
If these actions are performed, affected users must re-download their SSL VPN installation file to utilize the new certificate.
Check the /tmp partition on the device
- Reference this Document Guide to access the device’s advanced shell:
Go to the /tmp partition and investigate if the following SSL VPN files are present
# cd tmp# cd /content/sslvpn# ls- Confirm if the following SSL VPN files are present in /content/sslvpn:
rw-rr- 1 1000 100 413 Apr 24 2015 client-config-template.ovpnrw-rr- 1 1000 100 111.1K Jun 17 19:35 ssl-vpn-config-installer.exerw-rr- 1 1000 100 1.4M Jun 17 19:35 ssl-vpn-client-installer.exerw-rr- 1 1000 100 72 Jun 17 19:49 U2DVERSION
If files aren’t present, try to manually update patterns for the SSL VPN Module
- If patterns fail to update, don't hesitate to get in touch with Sophos Support
Check if the /tmp partition is full
- #
df –h 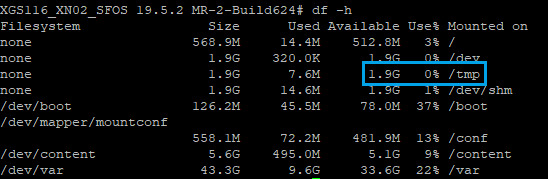
- If full, please contact Sophos Support for further assistance.
Update the device’s patterns
- Try performing a manual pattern update
- Backup & firmware > Pattern Updates > “Update Pattern”
- If patterns fail to update, contact Sophos Support
Revamped RR
[edited by: Erick Jan at 9:27 AM (GMT -7) on 17 Sep 2024]