NDR Sensor v1.8.0-2352: New Features and Enhancements
We are excited to announce the release of NDR Sensor v1.8.0-2352, which brings powerful new capabilities in asset identification and enhanced security detection.
Availability: This update was released Oct 17 to all Sophos NDR Customers.
Below is an overview of the key updates:
Asset Identification by Manufacturer
With this update, the NDR Sensor now includes an auto-updated registry of MAC address information. This enhancement allows the sensor to automatically identify the manufacturers of devices on your private network. In cases where devices are using randomly generated MAC addresses, the sensor will recognize and label these as such. Manufacturer information is now added to every context record for network flows and is available in a summary report for easy access.
A new DDE Statistics report (NDR-DET-DDE-MFGASSETIDENTIFICATION) is generated every 24 hours and is categorized as a Severity 0 Detection (INFORMATIONAL) in the detections view within the central platform.
To query manufacturer data from the data lake, you can use the following SQL example, which provides a count of each manufacturer, a list, and the number of MAC addresses:
SELECT sensor_id Sensor_ID, ingest_date DAY, ioc_unix_time, CAST(JSON_EXTRACT(raw,'$.name') AS VARCHAR) Report_Name, CAST(JSON_EXTRACT(raw,'$.description') AS VARCHAR) Description, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].vendor') AS VARCHAR) Vendor, SPLIT(JSON_EXTRACT_SCALAR(raw,'$.detection_context['||CAST(A.X AS VARCHAR)||'].macs'),',') Mac_List, CARDINALITY(SPLIT(JSON_EXTRACT_SCALAR(raw,'$.detection_context['||CAST(A.X AS VARCHAR)||'].macs'),',')) Mac_Count FROM mdr_ioc_all, UNNEST(SEQUENCE(0,JSON_ARRAY_LENGTH(JSON_EXTRACT(raw,'$.detection_context'))-1)) AS A(x) WHERE ioc_worker_id = 'worker_ndr' AND ioc_detection_id = 'NDR-DET-DDE-MFGASSETIDENTIFICATION'
Asset Identification by Operating System
The NDR Sensor now performs intermittent port scans to identify the operating systems of devices on the private network. Over time, the sensor learns and records the OS information, which is then included in detection context records. This data is also available in a summary report for administrators.
A new DDE Statistics report (NDR-DET-DDE-OSASSETIDENTIFICATION) is generated every 24 hours, also as a Severity 0 Detection (INFORMATIONAL).
To query operating system data from the data lake, you can use the following SQL example:
SELECT sensor_id Sensor_ID, ingest_date DAY, ioc_unix_time, CAST(JSON_EXTRACT(raw,'$.name') AS VARCHAR) Report_Name, CAST(JSON_EXTRACT(raw,'$.description') AS VARCHAR) Description, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].os') AS VARCHAR) Operating_System, SPLIT(JSON_EXTRACT_SCALAR(raw,'$.detection_context['||CAST(A.X AS VARCHAR)||'].ips'),',') IP_List, CARDINALITY(SPLIT(JSON_EXTRACT_SCALAR(raw,'$.detection_context['||CAST(A.X AS VARCHAR)||'].ips'),',')) IP_Count FROM mdr_ioc_all, UNNEST(SEQUENCE(0,JSON_ARRAY_LENGTH(JSON_EXTRACT(raw,'$.detection_context'))-1)) AS A(x) WHERE ioc_worker_id = 'worker_ndr' AND ioc_detection_id = 'NDR-DET-DDE-OSASSETIDENTIFICATION'
Encrypted Payload Analytics (EPA) 2.0 Model
The EPA 2.0 model has been enhanced to account for Maximum Transmission Unit (MTU) settings. MTU size controls on clients and servers can influence packet sizes, which previously impacted model accuracy. The updated model compensates for these variations, improving detection accuracy for malware family variations. Additionally, the model has been retrained using recent malware, while still retaining data on older malware families for potential re-emergence.
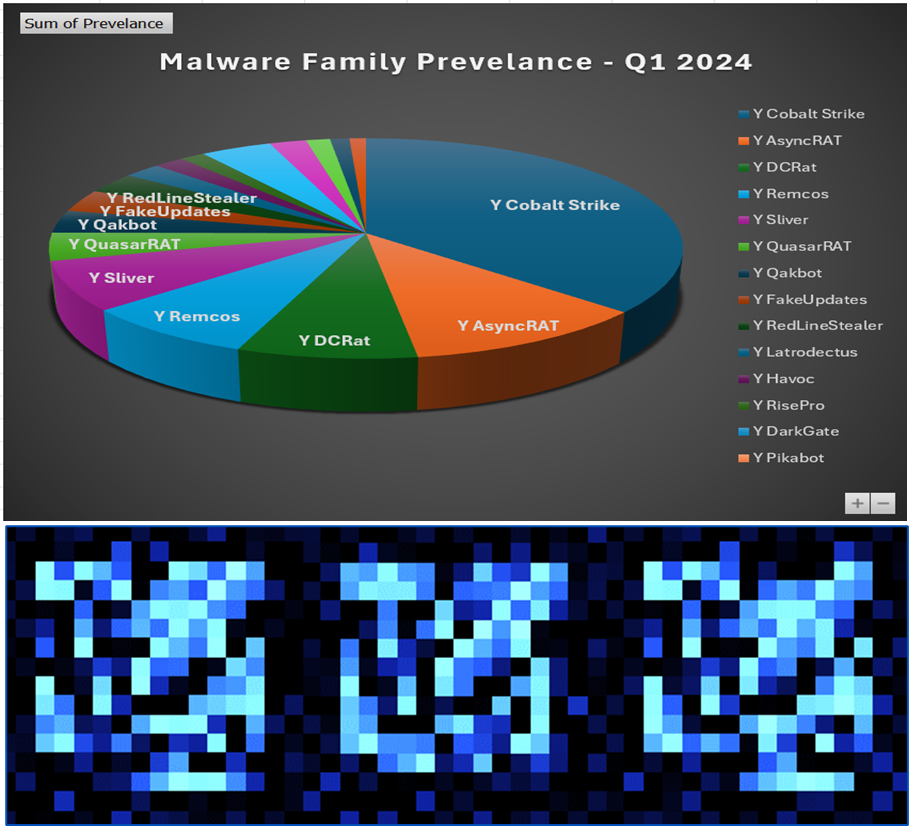
New Statistical-Based Detections
Basic Port Scan Detection
This detection is triggered when the NDR Sensor observes a source IP scanning 1,000 or more ports on a destination IP. The detection appears in the list as NDR-DET-DDE-BASICPORTSCAN with a Severity 0 rating (INFORMATIONAL).
The report is run each hour and only sent to central if port scanning activity was observed.
To view this data, you can access it via Live Discover and the detection page’s flyout, or run the following SQL query:
SELECT sensor_id Sensor_ID, ingest_date DAY, ioc_unix_time, CAST(JSON_EXTRACT(raw,'$.name') AS VARCHAR) Report_Name, CAST(JSON_EXTRACT(raw,'$.description') AS VARCHAR) Description, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].src_ip') AS VARCHAR) Source_IP, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].dest_ip') AS VARCHAR) Destination_IP, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].dest_port_count') AS VARCHAR) Count_of_ports_scanned FROM mdr_ioc_all, UNNEST(SEQUENCE(0,JSON_ARRAY_LENGTH(JSON_EXTRACT(raw,'$.detection_context'))-1)) AS A(x) WHERE ioc_worker_id = 'worker_ndr' AND ioc_detection_id = 'NDR-DET-DDE-BASICPORTSCAN'
SSH Brute Force Detection
The SSH Brute Force detection is triggered when the NDR Sensor observes 15 or more connection attempts to port 22 (SSH) from a single source IP. Like the port scan detection, this is categorized as a Severity 0 Detection (INFORMATIONAL) under NDR-DET-DDE-SSHBRUTEFORCE.
The report is run each hour and only sent to central if potential SSH Brute Force activity was observed.
You can explore this detection using Live Discover or the flyout, or run the following SQL query:
SELECT sensor_id Sensor_ID, ingest_date DAY, ioc_unix_time, CAST(JSON_EXTRACT(raw,'$.name') AS VARCHAR) Report_Name, CAST(JSON_EXTRACT(raw,'$.description') AS VARCHAR) Description, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].src_ip') AS VARCHAR) Source_IP, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].src_mac') AS VARCHAR) Source_MAC, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].dest_ip') AS VARCHAR) Destination_IP, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].dest_port') AS VARCHAR) Destination_Port, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].dest_mac') AS VARCHAR) Destination_MAC, CAST(JSON_EXTRACT(raw,'$.detection_context['||CAST(A.X AS VARCHAR) ||'].num_attempts_in_minute') AS VARCHAR) Attempts_in_one_minute, ioc_severity FROM mdr_ioc_all, UNNEST(SEQUENCE(0,JSON_ARRAY_LENGTH(JSON_EXTRACT(raw,'$.detection_context'))-1)) AS A(x) WHERE ioc_worker_id = 'worker_ndr' AND ioc_detection_id = 'NDR-DET-DDE-SSHBRUTEFORCE'

