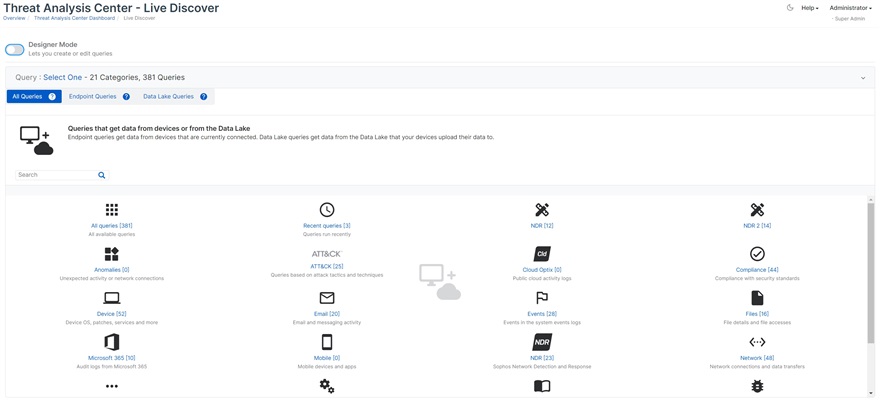
NDR Live Discover Category and a set of 23 reports are now available for all NDR customers.
This update allows you to explore the NDR data and flow based detections.
Video:
https://vimeo.com/manage/videos/831535844
From the Central Threat Analysis Center select Live Discover and the NDR Query Category for a list of available reports.
Sophos provided queries
| Name | Description | Sources |
| NDR - Card view for FLOW based detections | Retrieve information about flow-based detections, including context and importance of the data, by analyzing the detection record. | Data Lake |
| NDR - Condensed Detections View | Extract key attributes from detections and provide a single row per flow record in the detection, with filters on Message Identifier and Sensor ID. | Data Lake |
| NDR - Devices connecting to suspect threat IPs | List source IPs communicating with suspect destination IPs, filtered by source and destination IPs and optional sensor ID. | Data Lake |
| NDR - Devices generating most network traffic | Top 100 talkers on a network by identifying the private IP address of the machine, total bytes sent or received by that IP, and the producer-consumer ratio (PCR) payload, which indicates if the traffic is mainly upload or download. | Data Lake |
| NDR - Devices generating most network traffic (BARS) | Top 100 talkers on a network by identifying the private IP address of the machine, total bytes sent or received by that IP, and the producer-consumer ratio (PCR) payload, which indicates if the traffic is mainly upload or download. | Data Lake |
| NDR - Devices with suspect threat intelligence hits | Source IPs that communicated with a suspect external IP (dest_ip). The result includes sensor ID, severity, threat intelligence, and message identifier. Input variables are source IP, destination IP, and sensor ID. | Data Lake |
| NDR - MAC IP correlation | Retrieves the correlation between source Mac, IP, and hostname information using MDNS and NetBIOS. The query includes a filter for the sensor ID and the variables: Source IP, Source MAC Address, Web hostname, and meta hostname. It also joins with XDR data to retrieve additional endpoint information. | Data Lake |
| NDR - Mac IP Hostname Correlation | Source Mac IP and Hostname Correlation based on MDNS and NetBIOS. NOTE: This includes hostname information extracted from the flow data where available. If no web_hostname was identified it will not be in the list. | Data Lake |
| NDR - Managed and Unmanaged device count | Count devices observed by MAC address. Provides managed and unmanaged device count with filters for Sensor ID, IP Address, and MAC Address. | Data Lake |
| NDR - Number of Monitored Hosts | Number of private, public, and unknown hosts being monitored by NDR. The results can be filtered by category and sensor ID. | Data Lake |
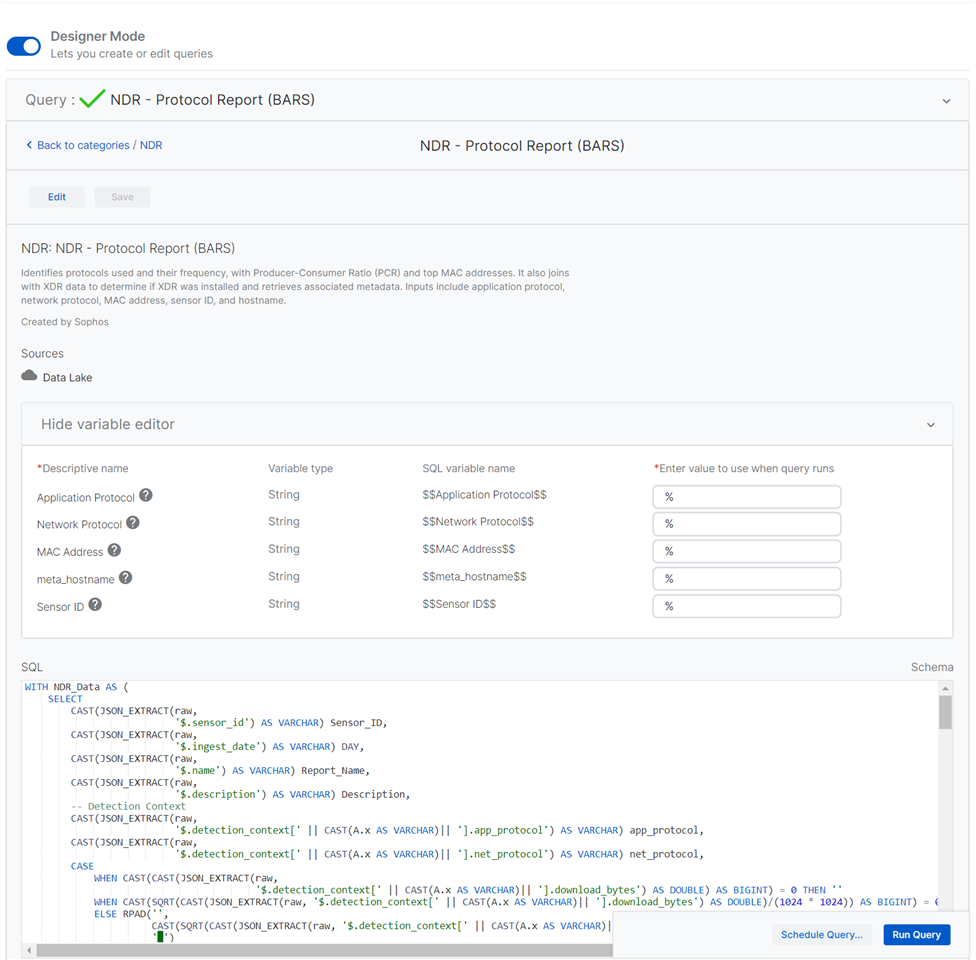
| NDR - Protocol Report | Identifies protocols used and their frequency, with Producer-Consumer Ratio (PCR) and top MAC addresses. It also joins with XDR data to determine if XDR was installed and retrieves associated metadata. Inputs include application protocol, network protocol, MAC address, sensor ID, and hostname. | Data Lake |
| NDR - Protocol Report (BARS) | Identifies protocols used and their frequency, with Producer-Consumer Ratio (PCR) and top MAC addresses. It also joins with XDR data to determine if XDR was installed and retrieves associated metadata. Inputs include application protocol, network protocol, MAC address, sensor ID, and hostname. | Data Lake |
| NDR - Raw record data | Extracts and displays raw data for NDR Detection or Report records from a Data Lake, allowing for easier creation of advanced queries. | Data Lake |
| NDR - Report count | Count of the available NDR reports by day and type, with filters for report name, type, and sensor ID. | Data Lake |
| NDR - Sensor ID and Version | Lists the Sophos NDR Sensor ID and version by day. | Data Lake |
| NDR - Suspect web server enumeration (Discovery) | Identify webserver scanning or web crawling by detecting known bad user agents and comparing requested web pages against a common enumeration wordlist. The severity score ranges from 0 to 9 based on the number of matches found. Inputs are the source IP, destination IP, and sensor ID. | Data Lake |
| NDR - Table view for FLOW based detections | Table view for flow detections with device info. Filters by sensor ID and message ID. Includes risk details, detection context, IDS detection info, DGA and ML family detection. | Data Lake |
| NDR - Table view Protocol use | Identifies the protocols used and their frequency. | Data Lake |
| NDR - Top 10 hosts for each protocol seen | Top 10 hosts for each protocol seen on a network, along with their IP and MAC addresses, total bytes transferred, and device details. Filter results based on application protocol, IP and MAC addresses, hostname, and sensor ID. | Data Lake |
| NDR - Top 100 most trafficked domains | Top 100 most trafficked domains by traffic volume. Filter by destination IP address, domain name, and sensor ID. | Data Lake |
| NDR - Top 100 most trafficked domains (BARS) | Top 100 most trafficked domains by traffic volume. Filter by destination IP address, domain name, and sensor ID. | Data Lake |
| NDR - Top Clusters | Identifies clusters with the highest traffic in bytes. A cluster is a group of flows sharing the same src_ip, dest_ip, dest_port, protocol, app_protocol. | Data Lake |
| NDR - Top Clusters (BARS) | Identifies clusters with the highest traffic in bytes. A cluster is a group of flows sharing the same src_ip, dest_ip, dest_port, protocol, app_protocol. | Data Lake |
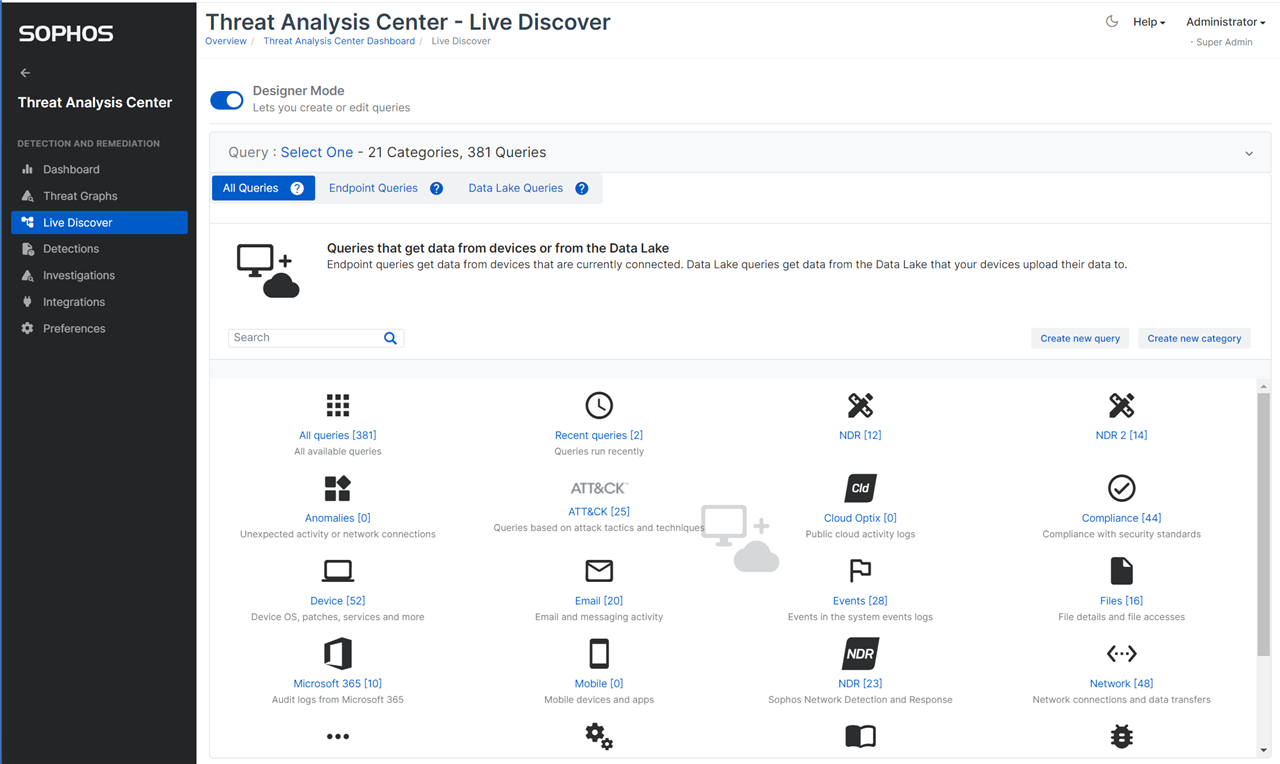
Using variables
Most of the queries allow for variables to be used so you can get the report for a specific NDR senor, protocol, source IP, destination IP and other useful filters.
Note that with SQL queries a '%' is a wildcard, so in the example below we are searching for any protocol, mac address, hostname...
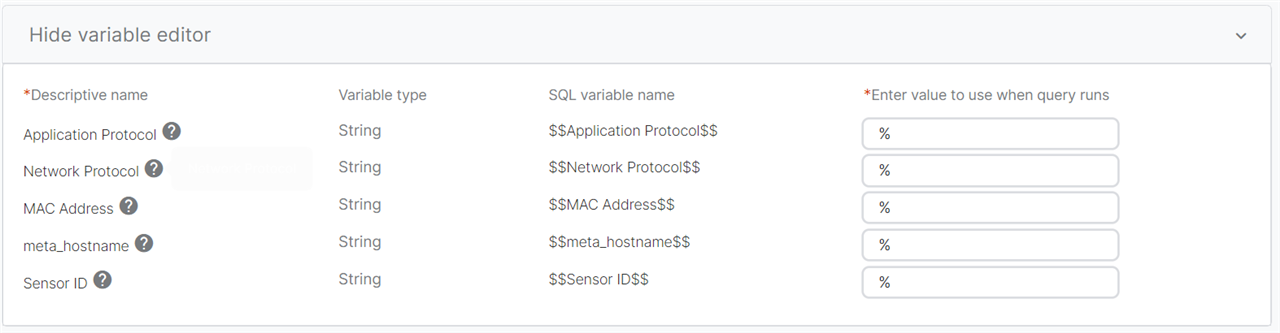
Reporting period and scheduled reports
You can control the date range of the report when running the query, simply select one of the pre-set date range filters, or set a start and end time using the custom range option.
To schedule a report to run regularly you can select the schedule option. The scheduled query will use the variables and time range you selected.
Creating your own reports from NDR Data
The easiest way to create your own report is to modify one of the existing queries and then save it with a new name.
First enter 'Designer mode' on the top left of a selected query then make some edits. You can not over write the Sophos queries.
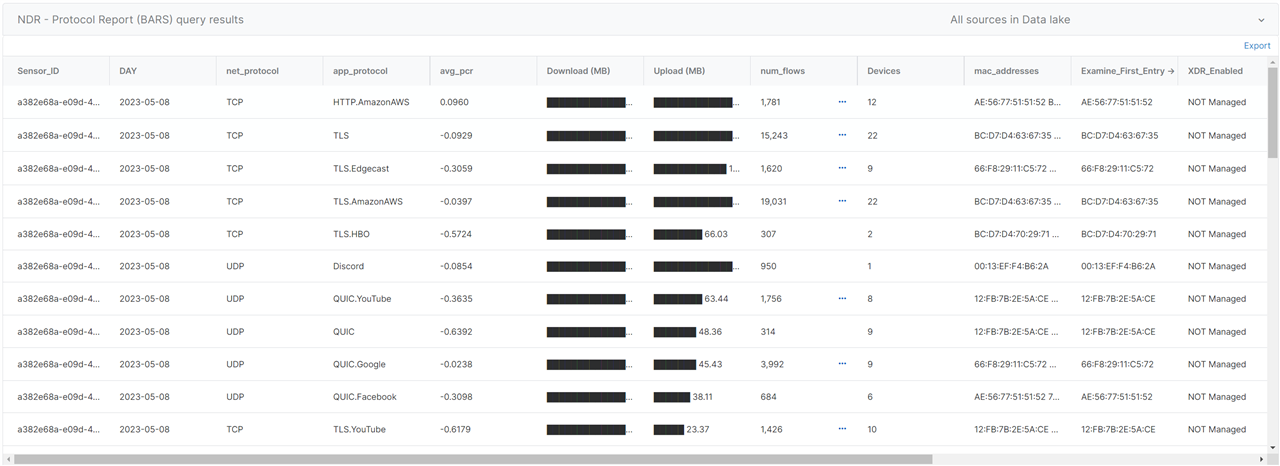
Example output of the NDR - Protocol Report (BARS)
How to get support?
For questions on how to run the queries, Sophos Support can be of assistance. If you need some help with specific NDR Queries, please leave a comment or start a discussion thread here. During the EAP, you can also reach us by emailing MDREarlyAccessProgram@sophos.com
Thanks Karl