With NDR you will automatically have detections and for those with a severity of 6 or higher an investigation record will be created and the administrator will be notified.
To assist with how to perform an investigation we are developing investigation playbooks and will be publishing the procedure to our online documentation.
Below is a sample of one of the playbooks under development.
Please comment and provide input on how you would like the playbooks to be presented and used in the product for investigations.
Investigation Triggers:
- Network detection identified as potentially involving a Domain Generation Algorithm
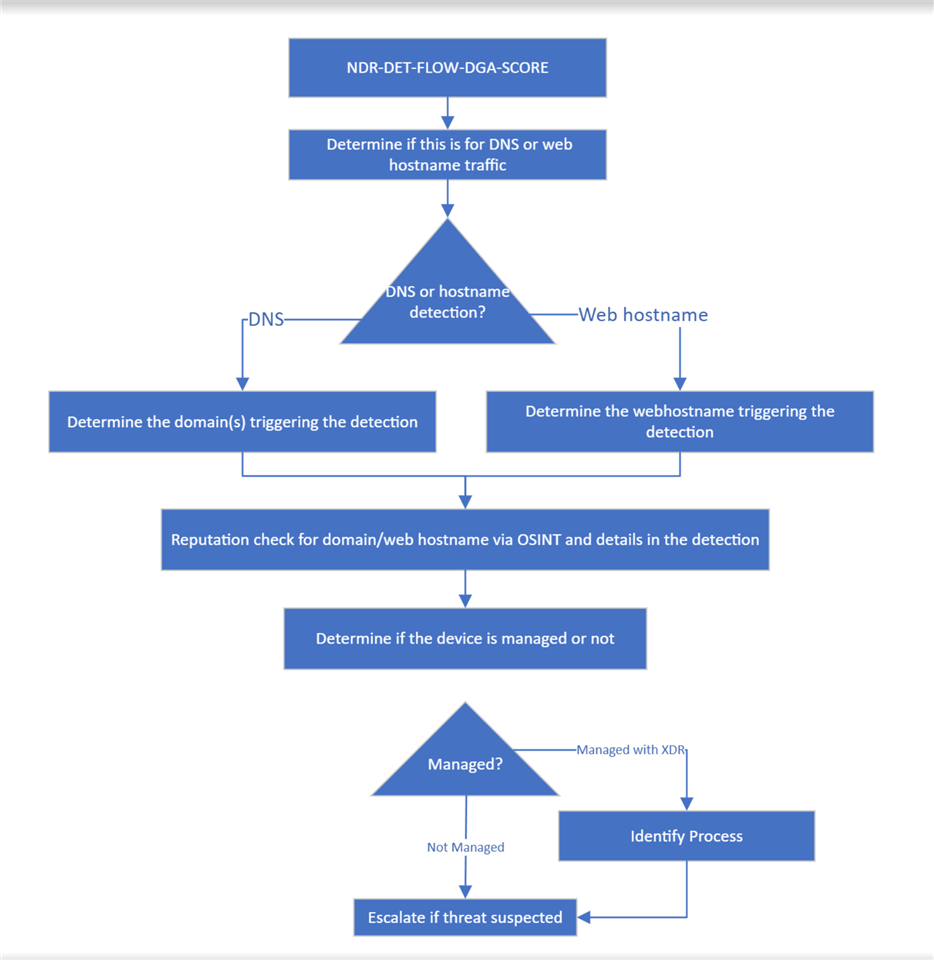
Investigation Steps:
-
Determine if the detection involved DNS queries or direct communications to a hostname:
- Review the detection summary to identify if it involved DNS traffic (UDP/53) or direct communications (e.g. HTTP/HTTPS)
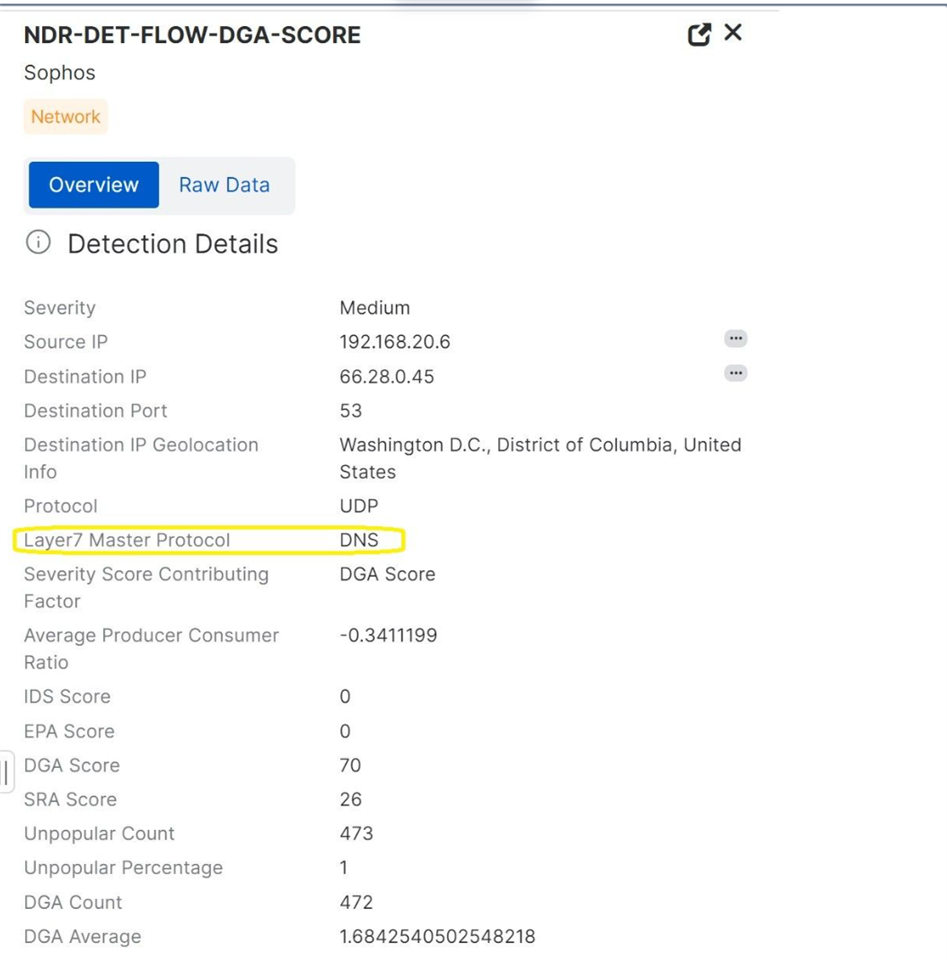
-
If DNS traffic, identify the suspicious domains:
- Query network data to extract the full domain names that triggered the detection
Use the canned query (NDR Detection Details - DGA DNS lookup)
- Query network data to extract the full domain names that triggered the detection
-
If direct hostname communications, identify the hostname:
- Query network data to extract the hostname that was contacted
Use the canned query (NDR Detection Details - DGA Webhostname)
- Query network data to extract the hostname that was contacted
-
Check reputation of identified domains/hostnames:
- Search online reputation databases (e.g. VirusTotal) for any information on the domains/hostnames
- Attempt to visit the domains/hostnames to observe any malicious content (use a safe sandbox environment)
-
Determine if the device is managed or unmanaged:
- Search device management tools to see if the source IP is from a managed asset
- Query network data to gather additional context about the source IP (hostname, MAC address, etc.)
Use the canned query (NDR Managed device correlation between NDR and XDR data)
- The query will provide a list of ALL NDR and XDR data for the device)
-
If a managed asset, identify the process making the connections:
- For DNS traffic, query endpoint DNS logs to pinpoint the process
- For direct communications, check active network connections
-
Based on findings, determine if the activity is malicious and take appropriate response actions (block IPs, isolate host, reimagine host, etc.)

