Hello everyone,
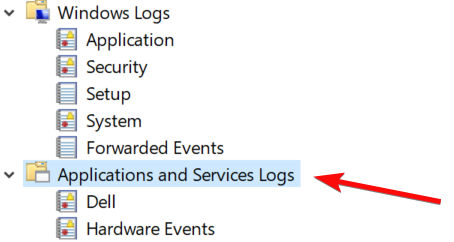
I understand there is a way to query for event logs in Live Discovery. From what I see, it may be limited to Windows Logs only i.e Application, Security, Setup, and System event logs. I tried querying an event id, but it pulled from Windows Logs > System instead of Applications and Services Logs.
Is it possible to query events under Applications and Services Logs?
This thread was automatically locked due to age.



