Hello everyone,
I understand there is a way to query for event logs in Live Discovery. From what I see, it may be limited to Windows Logs only i.e Application, Security, Setup, and System event logs. I tried querying an event id, but it pulled from Windows Logs > System instead of Applications and Services Logs.
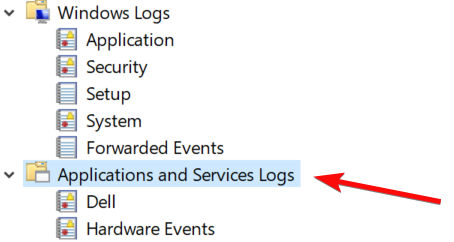
Is it possible to query events under Applications and Services Logs?
Hi iamroot,
Thanks for reaching out to the Sophos Community Forum.
For logs nested under the "Windows Logs" section the following basic query can be used as a starting point. The value you provide for "channel" will specify which logs you wish to query from.
SELECT datetime,computer_name,data FROM windows_eventlog WHERE eventid=#### AND channel='Application'
Regarding the Applications and Services logs, I was not able to locate a similar way to query this data. If you’re looking for data from specific sections such as "Powershell Events" or "Hardware Events" these are available.
Could you elaborate on which specific sections you're looking to query?
For reference, you can find more information on the tables you can access on the following pages.
- Sophos Schema
- OsQuery Schema

Here is an example:
SELECT
datetime,
JSON_EXTRACT(data, '$.EventData.TargetName') as TargetName,
JSON_EXTRACT(data, '$.EventData.UserName') as UserName,
JSON_EXTRACT(data, '$.EventData.DomainName') as DomainName,
JSON_EXTRACT(data, '$.EventData.CallerPID') as CallerPID,
JSON_EXTRACT(data, '$.EventData.ProcessName') as ProcessName,
JSON_EXTRACT(data, '$.EventData.ClientLUID') as ClientLUID,
JSON_EXTRACT(data, '$.EventData.ClientUserName') as ClientUserName,
JSON_EXTRACT(data, '$.EventData.ClientDomainName') as ClientDomainName,
JSON_EXTRACT(data, '$.EventData.MechanismOID') as MechanismOID
FROM
sophos_windows_events where source = 'Microsoft-Windows-NTLM/Operational'
and eventid = 8001
Hopefully you can change this