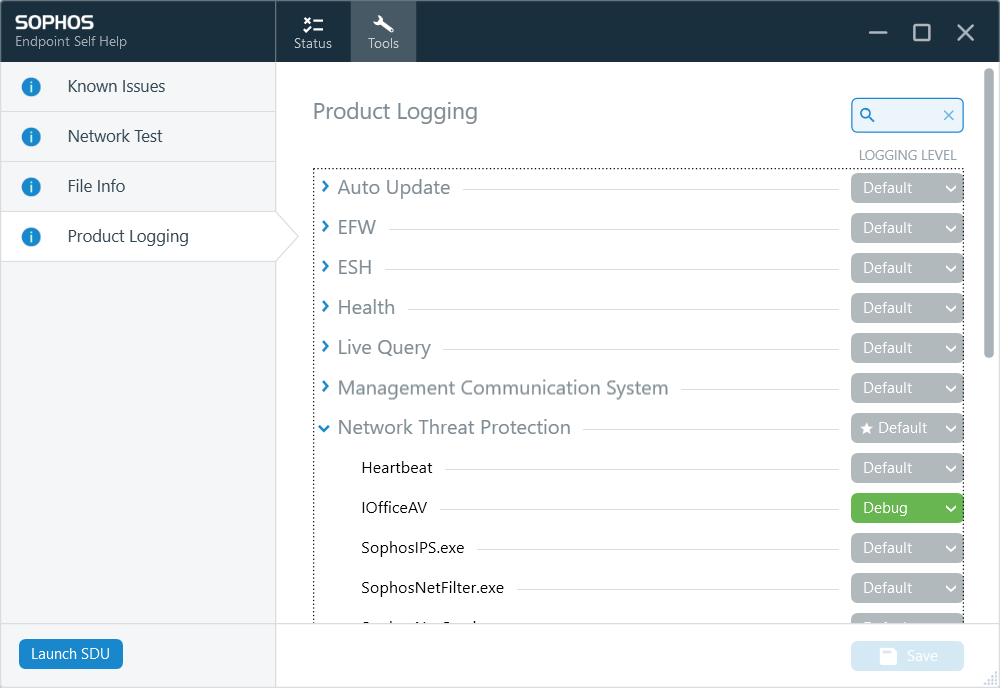
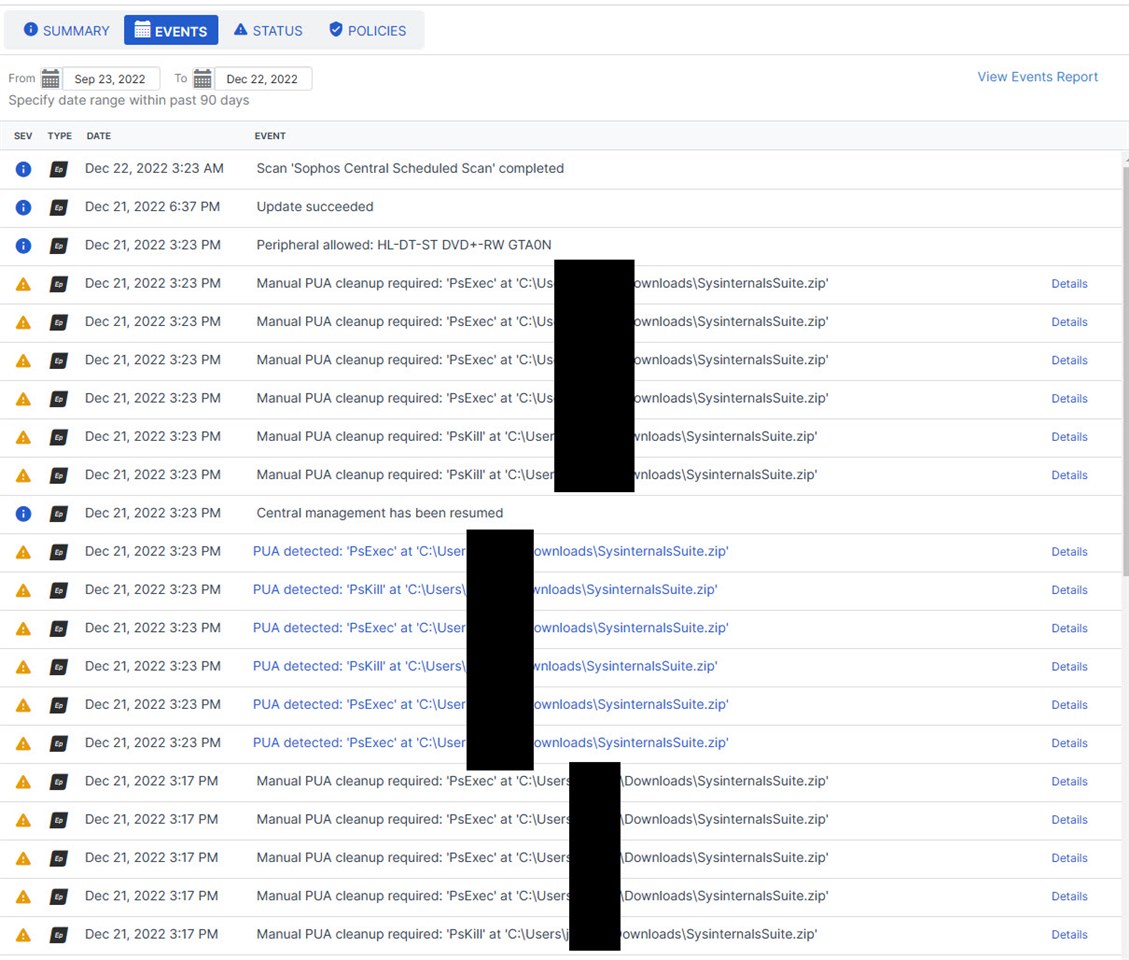
I've whitelisted PSEXEC and I've disabled all the modules for Sophos Endpoint but PSEXEC is still being removed as its recognised as a PUA. I've created a policy to whitelist this app on Central but nothing is applying.
Anyone know how to get around this?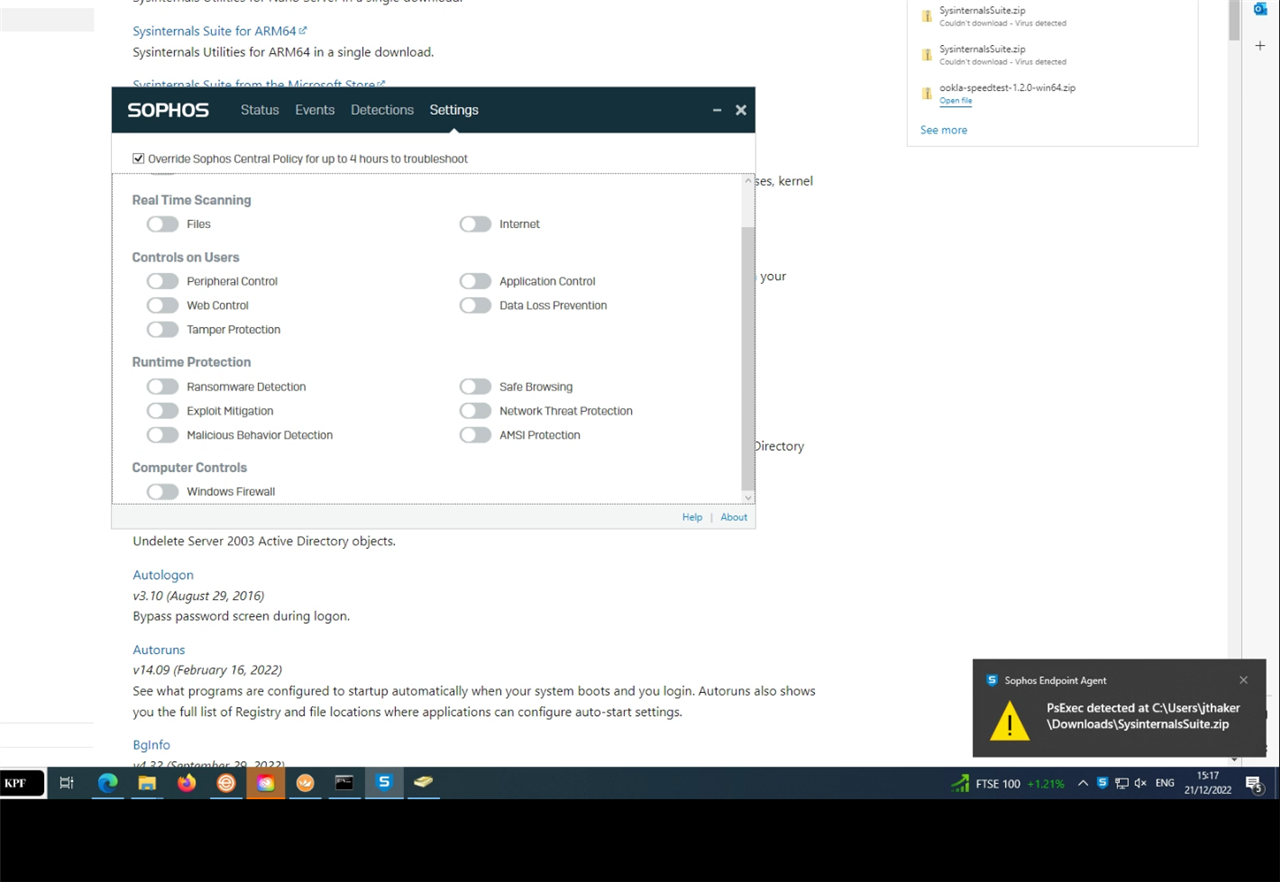
This thread was automatically locked due to age.