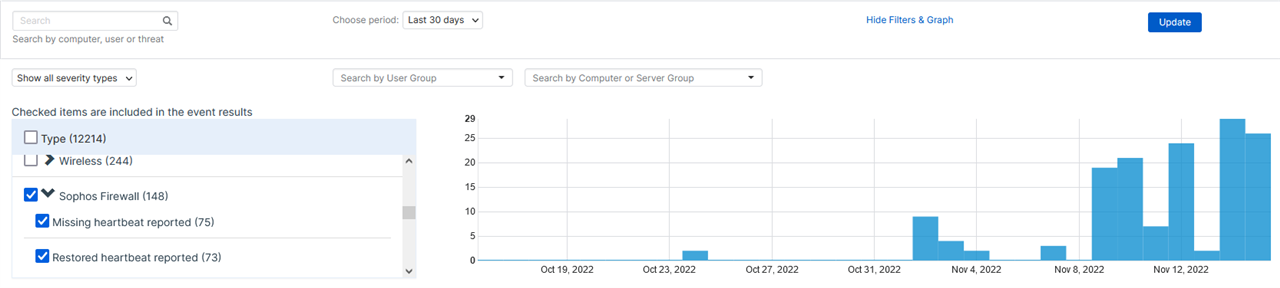
Since November an increasing number of endpoints is reported from Central with "Sophos Firewall SN reported computer not sending heartbeat signals"
We upgraded our HQ XG from 18.5.4 to 19.0.1 on Nov 12th but the issue started already before as you can see from the screenshots.
Before that, we only received this alerts occasionally. Sometimes the message comes multiple times per day for a machine, then a few days no message is created even if the computer is still in use.
What is the issue here?
Central Region is Central Europe
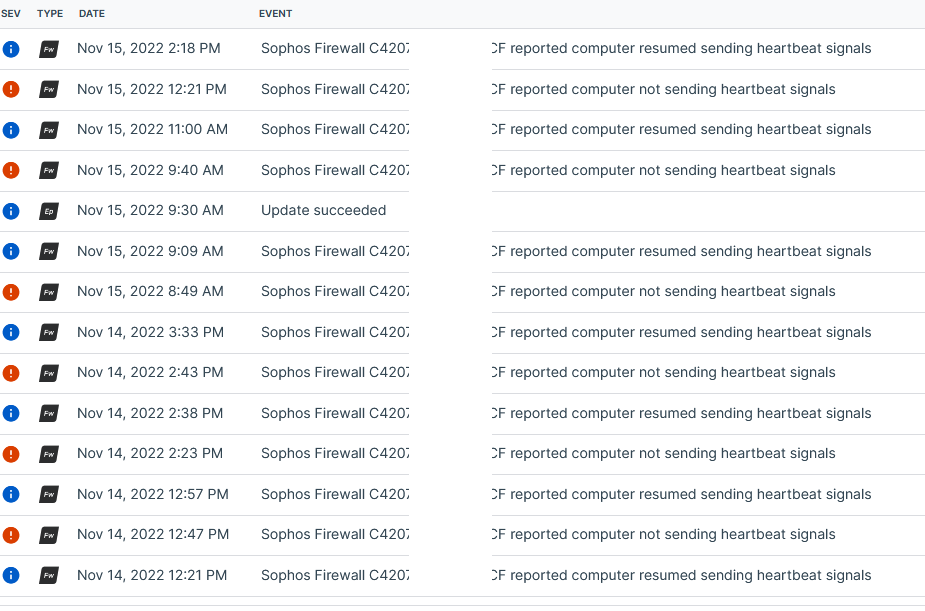
One Computer:
This thread was automatically locked due to age.