Good morning community and thanks in advance.
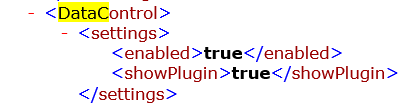
While testing and testing the potential of sophos EndPoint protection, in the Data Loss Prevention section of the enpoint policies, I cloned the base policy and started working with a new cloned policy.
In which I activated "Use rules for data transfers" and added a new rule ("New File Rule, A rule that controls transfer of certain file types or names").
Fill in the basic information, in conditions select "Where the file type matches....
Where the file name matches...
Required
Where the destination is...", in actions "Block transfer".
In conditions I have checked all of them to test.
And in the destination, all the options of "storage".
And in action "Block tranfer".
I finalize the rule, save the changes.
And in the section "Policy Enforced" I activate it.
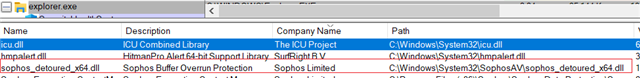
To test it, I connect a USB to my pc and transfer some file, it lets me transfer the file without any problem. In principle this should not be the case.
Can anyone help me where is the problem?
This thread was automatically locked due to age.