Now with the XDR Detections EAP open folks can see all activity that has been classified to MITRE ATT&CK.
The new page is in the Threat Analysis Center and has lots of really great information on what has been observed in your environment.
Currently detections are happening for Windows, Windows Server Linux and MAC OS.
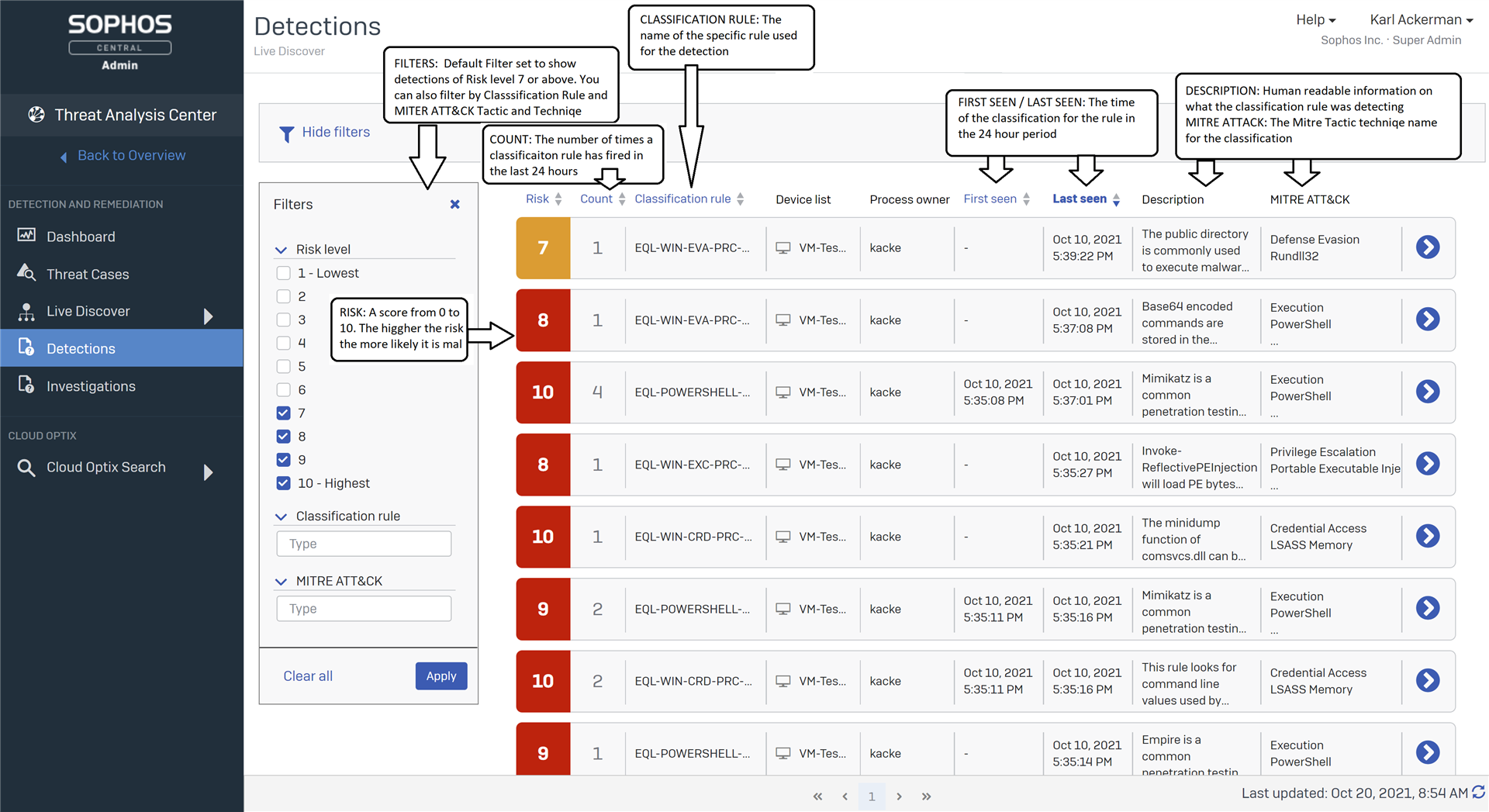
To get more information you can select the Right side chevron to expand a row to see each device and details on the evidence for the classification.
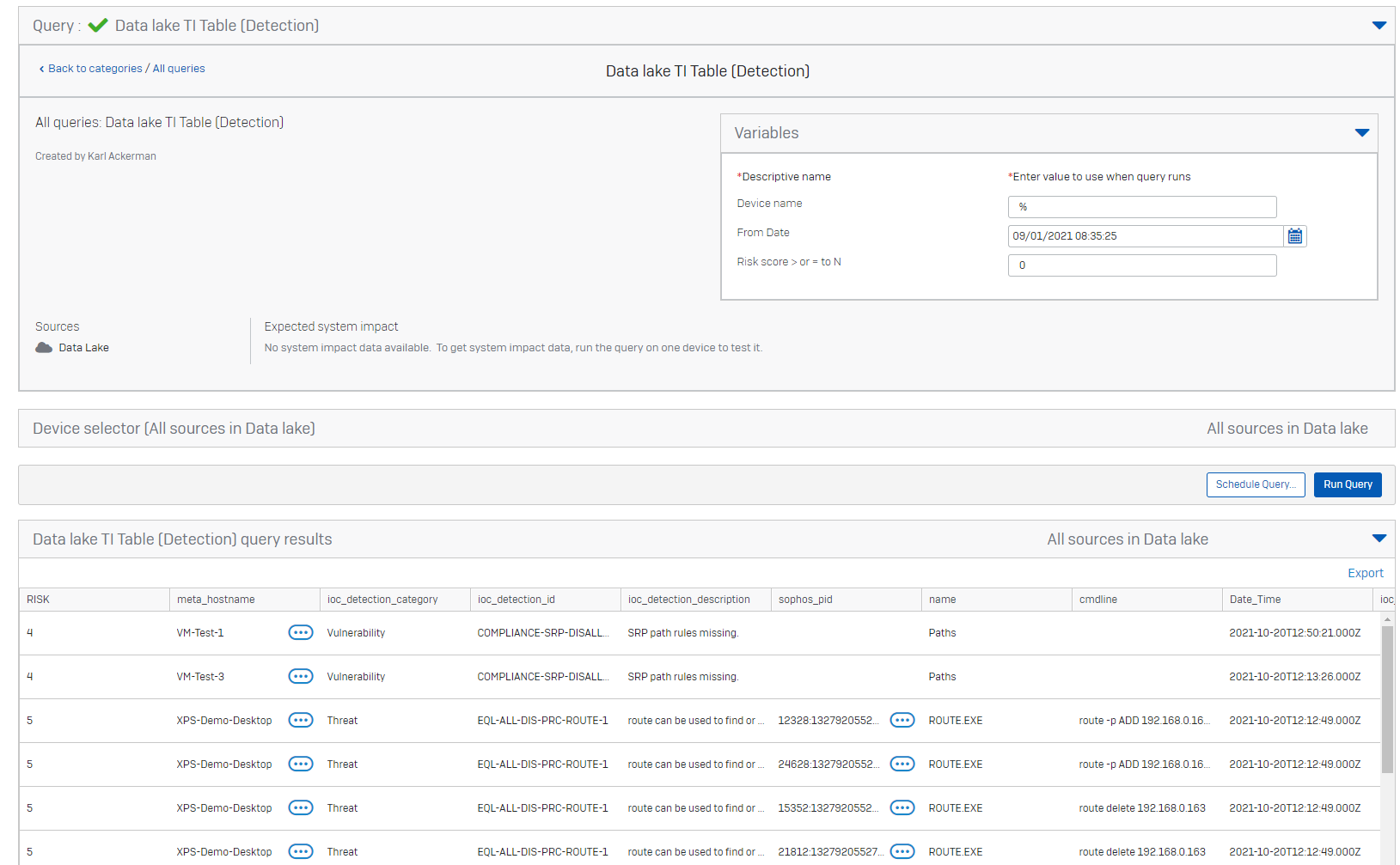
Also if you want you can use the following query to see the raw detection table in the data lake.
-- DetectioN table
-- VARIABLE $$Device name$$ DEVICE NAME
-- VARIABLE $$From Date$$ DATE
-- VARIABLE $$Risk score > or = to N$$ STRING
SELECT DISTINCT
ioc_detection_weight RISK,
meta_hostname,
ioc_detection_category,
ioc_detection_id,
ioc_detection_description,
sophos_pid,
name,
cmdline,
calendar_time Date_Time,
ioc_worker_name,
query_name,
username,
*
FROM xdr_ti_data
WHERE LOWER(meta_hostname) LIKE LOWER('%$$Device name$$%')
AND to_unixtime(calendar_time) > $$From Date$$
AND ioc_detection_weight >= $$Risk score > or = to N$$
ORDER BY calendar_time DESC