Hi,
I already put those as comments below that article https://community.sophos.com/intercept-x-endpoint/early-access-program/b/blog/posts/https-policy-changes
As I'm unsure, if it's gettig read there, I post it her ein the EAP forums again.
I notice 2 issues so far with the new SSL / TLS Scanning of Intercept-X where it is acting as Man-in-the-Middle SSL Scanner.
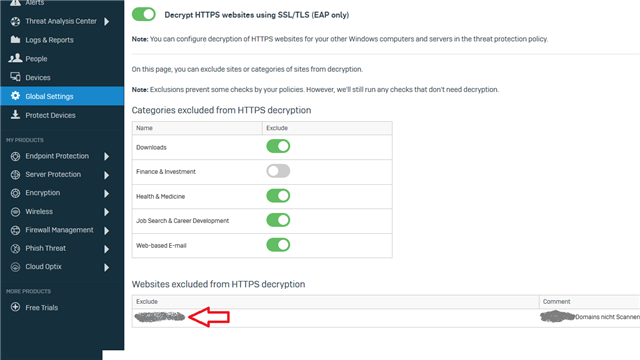
1. I cannot manage my comanies Sophos XG and SG firewalls with firefox using windows store certificates (security.enterprise_roots.enabled true) anymore. Other browsers are working. The firewalls Webadmin is equipped with commercial wildcard certificate for *.owndomain.abc
SEC_ERROR_REUSED_ISSUER_AND_SERIAL
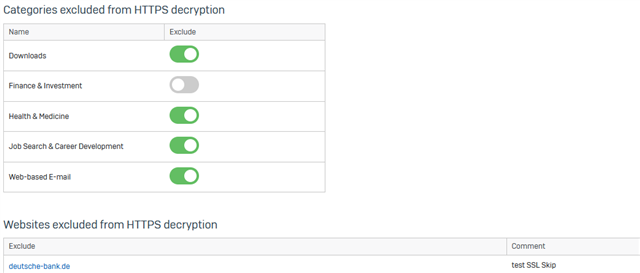
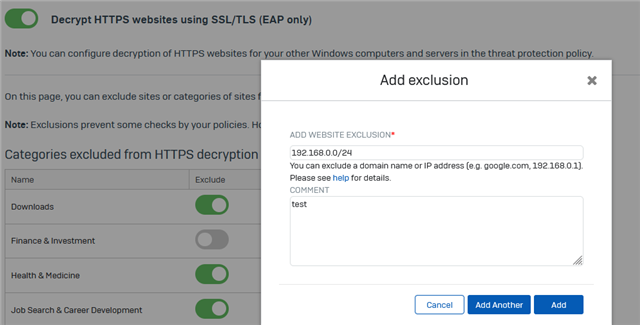
Excluding owndomain.abc as domain in Sophos Central SSL / TLS Settings is a workaround but we do not want it to be excluded.
When loading the firewall management website with IP https://123.123.123.123:4444 the same error appears with firefox.
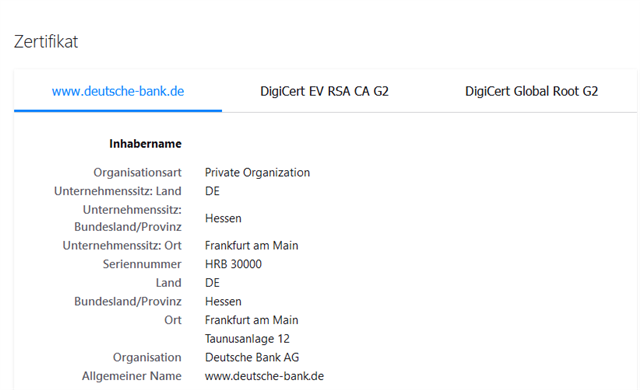
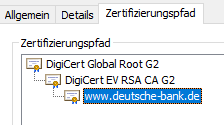
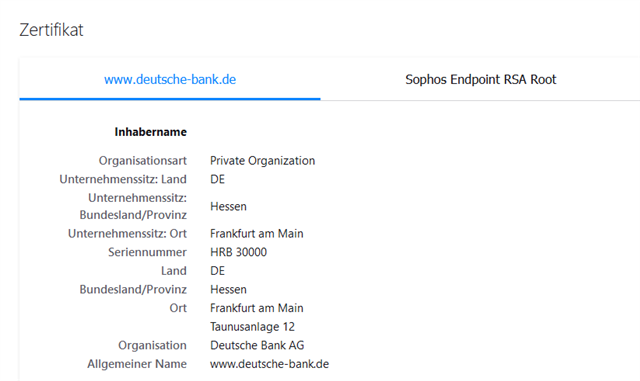
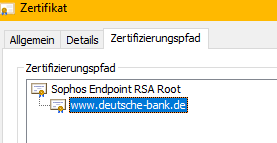
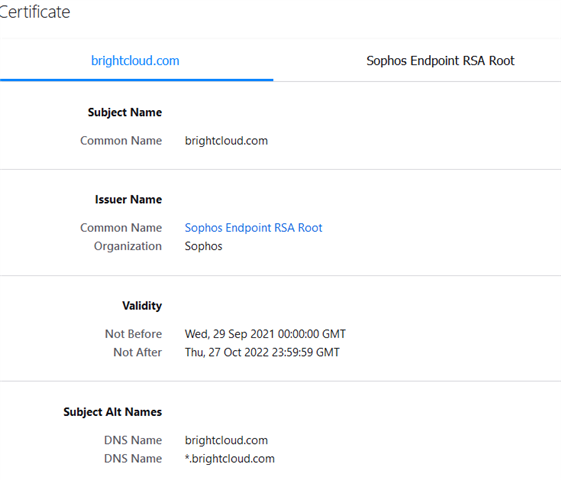
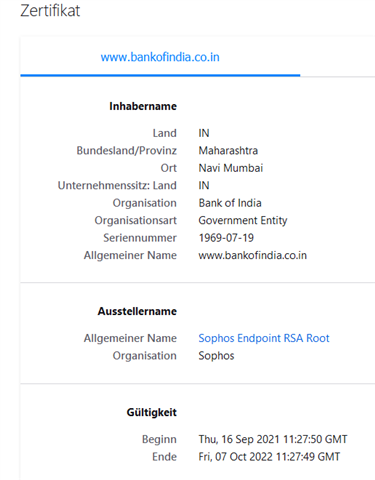
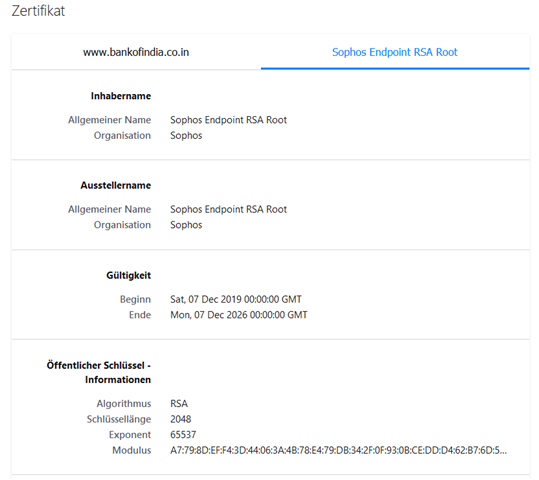
2. Excluding Banking websites is not working - the Endpoint will still break SSL and re-encrypt the page as can be seen by the issueing CA. That's a no-go.
examples:
hsbc.co.uk Categorized URL - Finance/Banking Minimal Risk
bankofindia.co.in Categorized URL - Finance/Banking Minimal Risk
added info about firewall mgmt IP
[bearbeitet von: LHerzog um 2:12 PM (GMT -8) am 7 Dec 2021]