Introduction
Welcome to the Sophos EDR Threat Hunting Framework. This document is intended to guide an experienced threat hunter through the process of initiating a hunt, gathering and enriching data, then taking the required action using Sophos EDR tools (Live Discover, Live Response, and Clean & Block).
At the time of publishing, this guide is focused on the Microsoft Windows Operating Systems, additions for macOS and Linux are coming soon.
Sophos EDR Threat Hunting Foundations
Sophos EDR is a toolset that enables human threat hunters to quickly discover signals, assess the context of those signals and perform the necessary actions to remediate a discovered threat or to refine the threat hunting process to rule out "false positives" in future hunts. The glossary below will familiarize you with the Sophos terminology used throughout this guide.
| Term | Sophos EDR definition | |
|---|---|---|
| Live Discover | Live Discover is the Sophos EDR feature that enables a threat hunter to query and retrieve data from the targeted devices | |
| Live Discover query | A query is a mechanism of defining what data should be retrieved from the targeted devices, Sophos uses the Osquery engine which uses SQLite syntax queries | |
| Osquery | A framework that processes SQL language queries and allows data sets on the device (e.g. Event viewer, registry, system properties) to be seen as database tables for data extraction and filtering. You can view the native Osquery schema at Osquery Schema v4.2.0 | |
| Sophos journals | Sophos forensic journals containing up to 90 days of data of process, file, registry key and network connection data. Sophos has extended Osquery to provide access to these journals as tables that can be queried. You can view the schema of these journals at Live Discover Schema | |
| "Signal" | In this guide, we'll use the word "signal" to describe a discrete item that requires further investigation, e.g. a process that created a file that is considered an Indicator of Compromise (IOC) | |
Examples of possible "signals" discoverable |
Sophos PID | An identifier for a single unique execution of a process |
| Sophos ML score | 1-100, higher is more likely malicious | |
| Sophos local reputation | The SophosLabs reputation of the file as cached on the targeted device | |
| Sophos global reputation | If looked up via Sophos Live Protection, this is the reputation score as classified at the time of lookup by SophosLabs | |
| Sophos PUA score | 1-100, lower is more likely PUA | |
| Live Response | Live Response is the Sophos EDR feature that enables a threat hunter to interact with a targeted device remotely in a SYSTEM/ROOT level command prompt | |
| Device isolation | Device isolation is the Sophos EDR feature that enables a threat hunter to isolate a targeted device from the network, whilst still allowing management communications to Sophos Central and customer defined exclusions for local remote access. You can read more about customer defined exclusions at Device isolation exclusions (Windows) | |
Threat Hunting Process
Sophos threat hunters use the process below when initiating and running through a threat hunt. In this guide, we'll break down each section of this process into the steps in the Sophos EDR toolset which help hunters perform their initial hunts, gather the required contextual data from the targeted devices and 3rd party sources, and take the necessary actions to neutralize a detected threat or refine the hypothesis to reduce "false positive" signal detections.
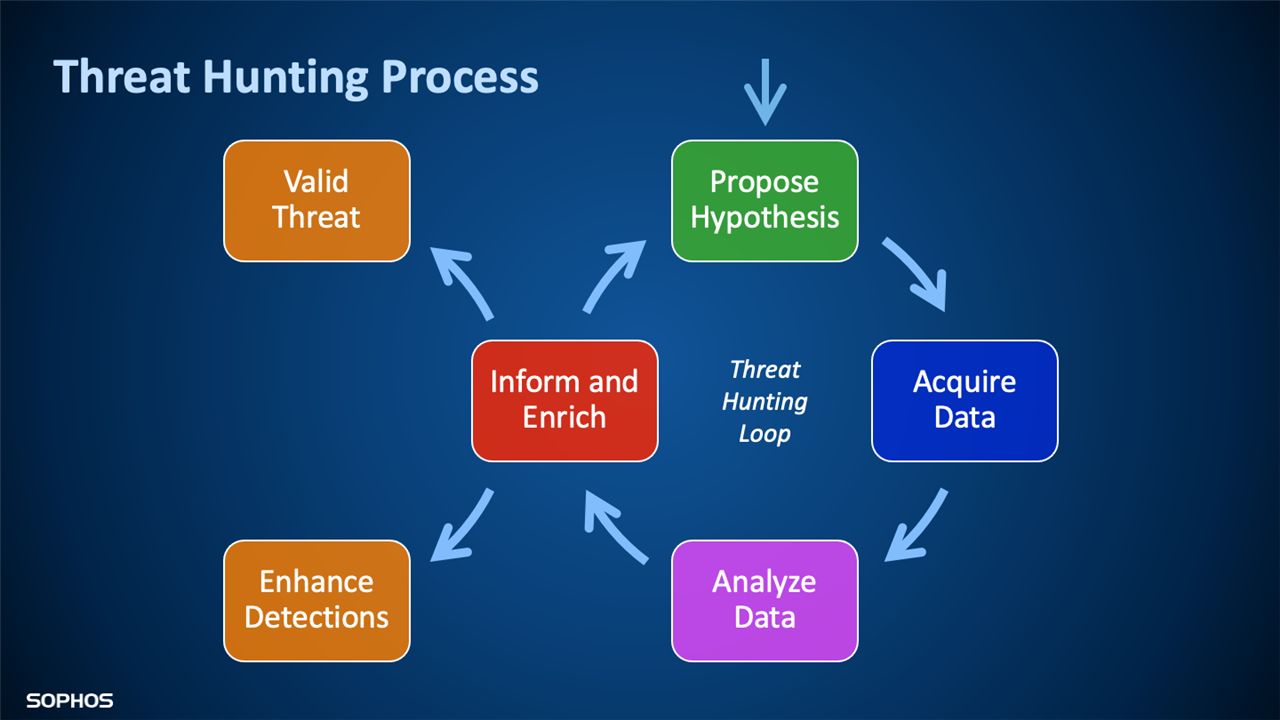
Propose Hypothesis
This section will guide you through defining your threat hunt hypothesis in Sophos EDR. There are 4 types of hypothesis that this guide will cover:
- Identifying the presence of Indicators of Compromise (IoC) - Use Threat Search or Live Discover to identify the presence of IOCs and triage the results using Threat Cases or further Live Discover Queries
- Sophos provided Live Discover queries - Sophos provides a number of pre-built queries for threat hunting and IT hygiene, we'll highlight some of the most useful ones in this section
- EDR Community published queries - Sophos staff, customers and partners publish interesting queries to a curated forum hosted by Sophos
- Defining your own custom query to match your hypothesis - The in-depth data available in the Sophos Journals enables a threat hunter to define their own queries to evaluate and investigate hypotheses
|
Presence of Indicators of Compromise (IoC) via Threat Searches |
|||
|---|---|---|---|
| Searching for a threat | Next steps | ||
|
You can use the Threat Searches section of the Threat Analysis Center to quickly search for one or more file names, SHA-256 file hashes, IP addresses, domains or command lines. Searches find PE files (like applications) with uncertain or bad reputations and network destinations they've connected to. Searches also find activity by admin tools, which can be used maliciously. |
If a Threat Search identifies the presence of an IOC you can create a simple Threat Case to investigate and gather signals for further Live Discover queries in the Aquire & Analyze data section. If you are sure that the searched for PE is malicious and is not being proactively blocked by the Sophos agent, you can "Clean and Block" to remove it from systems and add it to a global block list. |
||
|
Presence of Indicators of Compromise (IoC) via Live Discover |
||||
|---|---|---|---|---|
| Source of IOCs | Query to discover signals | Query input | Query output | Next steps |
| Lists of IOCs in CSV format |
Sophos has published a query that can process a list of IOCs in a CSV format. Visit the link below for the details of the variables needed, and the query itself. Sophos Cybersecurity GitHub page for generic IOC threat hunt query |
SophosLabs publishes IOCs in this format : NOTE: Use the "raw" URL from GitHub, e.g. for Conti Ransomware: https://raw.githubusercontent.com/sophoslabs/IoCs/master/Ransomware-Conti.csv We expect other CSVs using the same format to be properly processed by the same query. |
|
Use the queries in the "Acquire and analyze data" section to investigate any Sophos PIDs, files and/or Registry keys of interest |
| Individual IOCs |
Threat Hunting > Processes matching SHA-256 hashes in the last 30 days |
|
|
|
| Network > IP address activity |
|
|
||
| Files >File access history |
|
|
||
|
Sophos Live Discover is available for automation/bulk processing of queries via the Sophos Central API. Full details are online at the documentation site below: |
||||
|
Leveraging a built-in Live Discover query |
||||
|---|---|---|---|---|
| Behavior identified | Category > Name of query | Query input | Query output | Next steps |
|
Lists all remote authentication attempts (requires Windows event audit logging) |
ATT&CK > Remote Authentication Attempts |
None |
|
Triage any unexpected logins, especially from non-LAN IP ranges |
| Identifies unsigned applications that were run on the device on the last day. Code signing shows this is an authentic binary from the developer and has not been tampered with. (Code signing MITRE ID T1116) | ATT&CK > Unsigned applications that were run | None |
|
Use the process queries in the "Acquire and analyze data" section to investigate any unsigned processes and perform the necessary response actions |
| Lists unquoted paths in the service registry keys. Unquoted paths allow an adversary to place an application in a higher-level directory so that Windows finds that application instead of the intended one. (MITRE category T1034) | ATT&CK > Unquoted paths in the service registry keys | None |
|
Use the registry key queries in the "Acquire and analyze data" section to understand what process generated the key in question and triage other discovered signals as necessary |
| Lists processes that have a Remote Desktop (RDP) connection to an external device |
Network > Devices that have a Remote Desktop connection |
None |
|
Triage any unexpected logins NOTE: The query removes connections on local subnet ranges |
| Lists all processes that scheduled tasks and their details. Requires Windows audit object access logging |
Processes > Processes that scheduled tasks |
|
|
Use the process queries in the "Acquire and analyze data" section to investigate the process that created the scheduled task and triage other discovered signals as necessary |
| NOTE: Sophos regularly adds new generic signal discovery queries, check the "Last modified" column on the list of all queries to see the latest additions | ||||
|
Using a Sophos EDR Community published query + 3rd party queries |
|||
|---|---|---|---|
| Query description and URL | Query input | Query output | Next steps |
|
Sophos curates a collection of community posted queries contributed by Sophos staff, partners and customers. Visit the Live Discover & Response Query Forum at this link to participate! Below are two particularly useful queries for detecting the use of encoded PowerShell and gathering data based on a number of variables. To use these, or any other queries available in the Community, follow these steps to create a custom query:
|
|||
|
Identification of the use of encoded PowerShell commands |
|
|
|
|
Generic search for activity gathering Generic search query at the Sophos Community NOTE: you don't have to fill in every variable Example uses:
|
|
|
|
| NOTE: Sophos Live Discover is built on the foundation of Osquery, an open-source framework. We expect queries written by 3rd parties and using the same Osquery schema to work unmodified in Sophos Live Discover. | |||
|
Creating a custom query for a behaviour not yet covered by a built-in or Community query |
|||
|---|---|---|---|
|
You can create your own custom query using the steps below, these queries are available to all administrators and can contain variables for simple reuse.
In the sections below we'll outline some important things to know about creating your own queries. This isn't an exhaustive list of Osquery / SQLite resources, if you're having problems with a particular query we recommend reaching out to the Live Discover & Response Query Forum for assistance. |
|||
|
Schema |
Review the core Osquery Schema v4.2.0 schema and the extensions added by Sophos to the Live Discover Schema to funny understand the capabilities and the data that's available to retrieve |
||
|
Variables |
Live Discover queries support variables, review the Edit or create a query section of the online documentation for full details. NOTE: Variables names cannot contain the dollar sign ($) character NOTE: Reference variables in your custom query by calling the "Descriptive name" field surrounded by "$$", e.g. for a query with a Descriptive name of "File name" use "$$File name$$" in the query |
||
|
Wildcards & operators |
Live Discover queries support SQLite wildcards and operators, below is a list of the most frequent wildcards and operators you might want to use in a query:
You can read more detailed documentation about SQL As Understood By SQLite online. |
||
|
Query limitations |
Both endpoint/server devices and Sophos Central have guardrails to prevent a query from causing undesired behavior. Below is an extract from the Live Discover Overview article:
|
||
Acquire and Analyze Data
In this step, we acquire more data about the signal identified by our initial query. Throughout this stage, we'll identify further signals which will each need investigating and triaging to generate a complete picture of the series of events before and after the generation of the initial signal. Loop through the appropriate queries for each signal acquired until we fully understand all of the steps leading to the initial presence of the discovered signal, and any subsequent actions taken by or it or adjacent processes or files.
For complex query results, the data can be exported as a CSV file for further analysis or filtering in your preferred tool.
| PROCESS | |||
|---|---|---|---|
| Built-in queries | Query input | Query output | Suggested next steps |
|
Processes > Process details for a Sophos PID |
|
|
|
|
Processes > Process Tree for Sophos PID |
|
|
|
|
Processes > Process activity history |
|
Full details of the subject, action and object field contents are available in the sophos_process_activity table on the Live Discover Schema. |
|
| FILE | |||
|---|---|---|---|
| Built-in queries | Query input | Query output | Suggested next steps |
| Files > File attributes and metadata |
|
|
|
|
Files > File access history |
|
|
|
|
Files > File hashes |
|
|
|
| REGISTRY KEY | |||
|---|---|---|---|
| Built-in queries | Query input | Query output | Suggested next steps |
| Registry > Display registry section |
NOTE: add "/%" to the end of the desired registry key to retrieve the full content |
|
|
| Registry > Processes that modified a registry key |
|
|
|
Device Isolation
As you loop through the data acquisition queries, you might find yourself becoming more convinced that there are potentially harmful activities happening on one or more devices. You can use device isolation at any time to restrict those devices connection to both local and remote networks. Devices will still be able to communicate with Sophos Centra and you can define your own exclusions for local devices to connect remotely to assist in the investigation.
Inform and Enrich
In this section we'll cover the next stage of threat hunting, which is to gather further information about the signals we discovered in the previous loops through the data acquisition queries. Typically we're looking to confirm if other intel sources believe the signal to be malicious or benign, identify if an IP address is hosting a Command and Control server or decode encoded strings discovered in command lines.
NOTE: We recommend using as many data sources as possible before concluding that a detection may be a false positive to avoid any bias from a single source.
Examples of resources that can provide enrichment for discovered signals, please note that some of these resources are 3rd parties and are not affiliated with Sophos, and Sophos has no control over the content you may see on these sites.
|
Service
|
Items that can be looked up |
Items that can be analyzed
|
More info at...
|
|---|---|---|---|
| SophosLabs Intellix |
|
|
Static analysis of PE files is available via Sophos Central. Review the Threat Case examples (Malware detections) documentation for further details. |
| Virus Total |
|
|
VirusTotal was founded in 2004 as a free service that analyzes files and URLs for viruses, worms, trojans and other kinds of malicious content. |
| Shodan |
|
Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc.) connected to the internet using a variety of filters. |
|
| CyberChef |
|
https://gchq.github.io/CyberChef CyberChef provides a simple "recipe" based platform for decoding obfuscated strings typically found in command lines for processes like PowerShell |
|
Act
In this final stage of our threat hunt, we've used threat intel to determine if we need to act to contain a threat, or if we should refine our threat hunt hypothesis or subsequent queries to better remove false-positive signals.
| ACT | ||
|---|---|---|
| Enhance detections to reduce FPs | Valid threat | |
|
You can create copies and then edit any of the built-in queries, and edit manually added queries directly in Sophos Central. Consider adding SQL filters to queries to reduce the number of initial signals identified and increase the likelihood that further signals will not be "false positives". |
Portable Executable |
If you've identified a valid threat in the form of a portable executable, you'll first want to block the file by its SHA-256 hash. Follow the instructions in the documentation for Blocked items. Adding a SHA-256 hash to the blocked items list removes any files matching the hash on all machines, and it proactively blocked on all other machines. If the detection was not in a folder or file which was specified in a Global exclusion or Policy based exclusion, we request that you submit a sample of the file to SophosLabs. If the detection was in a folder or file which was excluded, consider changing or removing the exclusion. |
| IP or URL |
If you've identified a valid threat in the form of a malicious IP address or URL, you'll want to block communications to that item in as many places as possible. You can use Sophos Web Control to block access to a URL, domain, IP address or CIDR range, make sure to create the "site" in Website Management in Global Settings, then add to both Endpoint and Server Web Control policies. You should also block access at your network firewall, proxy server, web gateway etc... |
|
| Other mitigations |
Using Live Response - Live Response is a remote terminal connection enabling the investigator to perform any action that can be carried out via the terminal, this includes launching other shells, such as PowerShell on Windows. NOTE: Live Response is disabled by default, and has separate settings for endpoints and servers. Once enabled for both device types, only Super Admin role administrators can use Live Discover. You can use custom roles to delegate Live Response permissions to non Super Admin roles. Administrators must be logged in using MFA to use Live Response. Documentation is online for the steps to set up and start Live Response and how to add a custom role if needed. |
|
| Compromised account detected - If you've concluded that a user or admin account has been compromised you should disable the account immediately. We recommend requiring MFA for all services that offer it. Follow these steps to check your Sophos Central MFA settings. |
||
Summary
NOTE: If you believe you are under active attack, the Sophos Rapid Response service is available to perform containment and remediation steps.
The Sophos Managed Threat Response service can act as your 24/7 threat hunting and response team and can be added to any Endpoint or Server protection license that's managed in Sophos Central.
Finally, below are some great resources for getting started with Sophos EDR:
| Resource type | Location |
|---|---|
|
Sophos Blog articles related to threat hunting |
|
| Sophos Live Discover technical resources | |
| Sophos EDR threat hunting in action |

