We have now rolled out the Microsoft 365 Data Integration (formerly Office 365) and Investigations into GA.
1. Getting started with Microsoft 365 Data Integration:
All XDR customers who wish to have their MS 365 data ingested into their data lake will now have the ability to do so if they weren’t part of the EAP. Please refer to Karl’s post which has instructions on how to get started - https://community.sophos.com/intercept-x-endpoint/edr-data-lake-eap/b/announcements/posts/ms-365-azure-audit-logs-and-xdr-data-lake
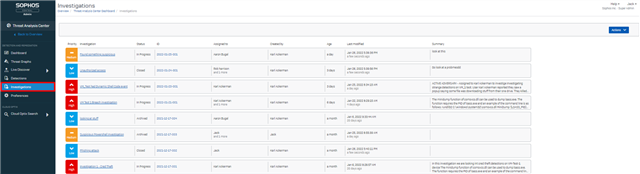
2. Getting started with Investigations:
In addition to Detections, all XDR customers should now see Investigations in their Threat Analysis Center. All features that were previously in EAP have now been brought to GA. Admin users who have access to Detections can now create new investigations and add multiple detections into them. They could assign investigations to other admins and document their notes.
Please refer to https://community.sophos.com/intercept-x-endpoint/b/blog/posts/investigations-eap-now-open for features from the Investigations EAP that are now in GA.
A new Investigations Dashboard will help users quickly dive into any recent investigations that were created. Users will be able to manually create investigations and associate multiple detections.
Features that are being turned on over the next few days:
This community post will be updated once these features have officially been turned on.
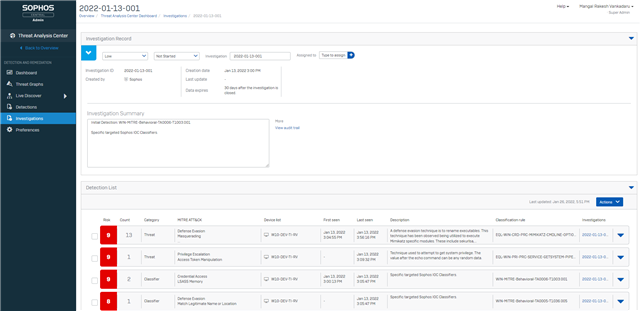
3. Automatic Generation of Investigations and Aggregation of Detections
We are in the process of turning on Auto Investigation Creation which will aggregate high severity detections above a threshold of 6+ into an investigation. It will be automatically triaged using our MTR threat hunting classification rules and detections that affect the same devices. Users won’t have to manually add similar detections into an investigation. This is coming over the course of next week and I will publish another announcement once it is widely available.
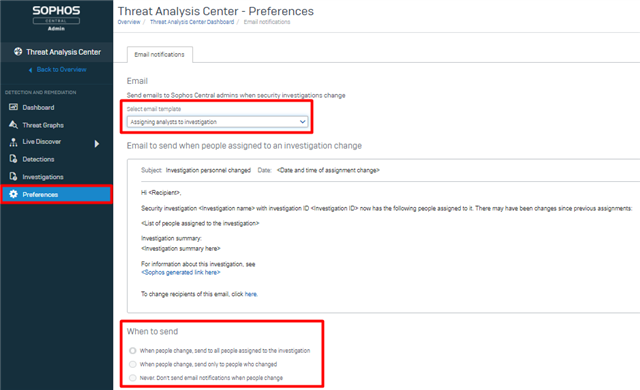
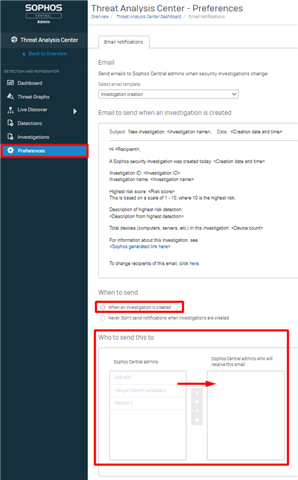
4. Email Notifications for Newly Created and Assigned Investigations
Email Notifications is being turned on and will arrive at the same time as auto generation of investigations. There will be a new Preferences page in the Threat Analysis Center with the option to configure 2 email notification rules.
The first rule is users can opt to select which users should receive email notifications when a new investigation is created either manually or automatically. The email content is specifically configured to have critical summary information about the investigation and a quick access link to it.
The second rule is for email notifications to users who are assigned to an investigations. There are 3 options available: When assignees are added or removed, 1 - all people assigned to the investigation will get a notification, 2 – send only to changed users, 3 – do not send any email notifications (turn this off).