Click to view the Japanese version: Intercept X Advanced with EDR のアップデート
With the launch of EDR 4.0 in May, Sophos has introduced significant enhancements to the Endpoint Detection and Response (EDR) offering. A key new EDR component is the Sophos Data Lake which stores critical data from EDR enabled devices and allows Live Discover to query that data even when devices are offline. For example, look back for unusual activity on a device that has been destroyed or taken without authorization. It’s an important part of cybersecurity visibility giving organizations the ability to see their entire environment and quickly drill down to granular areas of interest. Data Lake retention periods are 7 days (EDR) and 30 days (with our new XDR offering). This is in addition to the up-to 90 days of device on-disk data stored that could already be queried by Live Discover.
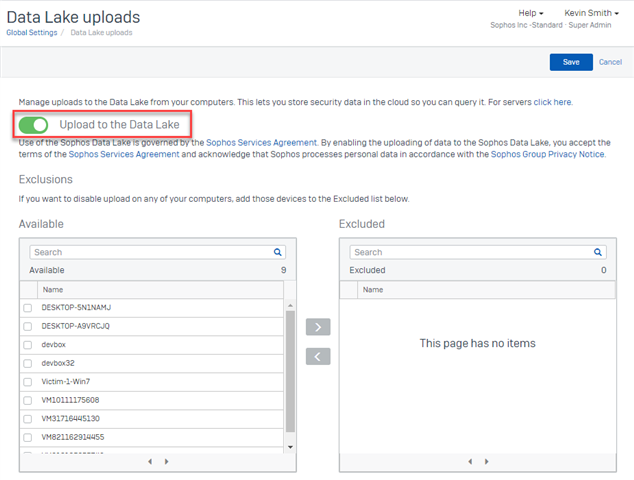
Please note that to query data in the Data Lake you need to enable the uploading of data to the Data Lake. In your Sophos Central console select ‘Global Settings’ then under Endpoint or Server Protection (or both) select the ‘Data Lake uploads’ setting and turn on the 'Upload to the Data Lake' toggle. Once enabled we will perform scheduled hydration queries on for your devices which capture interesting threat hunting related data and send it to the Data Lake. From the settings page you can also exclude specific devices from sending data to the Sophos Data Lake if you wish.
As Sophos continues to enhance Live Discover and its query capabilities with an with an ever expanding set of Sophos provided queries for threat hunting and IT operations and new pivoting functionality to help simplify the investigation process from Live Discover results, a decision has been made to retire the EDRv1 Data Feed which powers the existing Threat Search and Threat Indicators functionality. From July 1st, 2021 these features will be removed from Sophos Central. Below are are details on some new Data Lake queries which provide similar results to those available via Central Threat Search and Threat Indicators functionality.
The Live Discover Query forum on the Sophos Intercept X Community is also a rich source of information and queries created by both Sophos Staff and EDR/XDR customers.
| Query | Description |
| Decode PowerShell commands | The 'Decode PowerShell commands' built in Data Lake query decodes and lists PowerShell commands that are encoded with -encodedcommand |
| Events involving a SHA-256 | The 'Events involving a SHA-256' built in Data Lake query lists information about events that involve a specified SHA-256 hash. |
| Network activity for Sophos Process ID |
This Data Lake query will show network activity for a Sophos process ID that you define and are looking to investigate. The query can be found on the query forum here. |
| Threat Indicators | Similar to the Threat Indicators report in Central, this Data Lake query evaluates the machine learning and reputation scores to provide a list of the most suspect executables observed in the environment with the added benefit that customers can fine tune the query to help expand or reduce the resulting list. The query can be found on the query forum here. |
Scheduling Queries:
Another benefit of using new Data Lake queries is that you can have critical information ready and waiting for you. Queries can be scheduled to run overnight so key data is ready for assessment the next day.
To set up a scheduled query you first need to choose a query by going to the ‘Threat Analysis Center’ and then ‘Live Discover’. When you have selected the Data Lake query you want to run you will see a new option to schedule the query instead of running it immediately. Scheduled queries are currently only available for Sophos Data Lake queries.
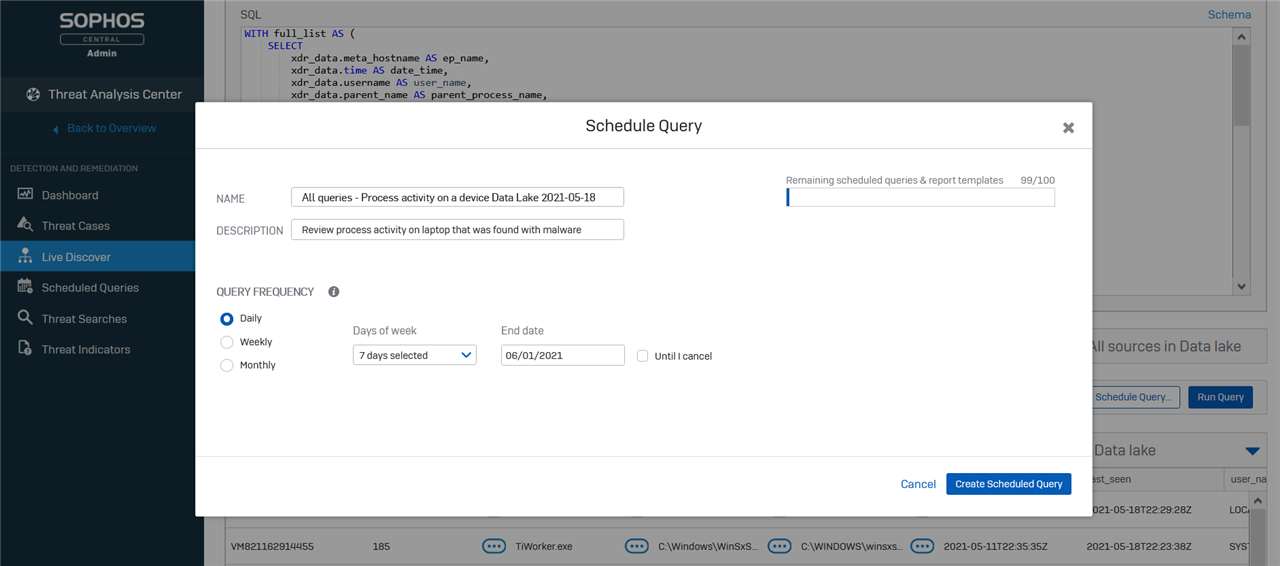
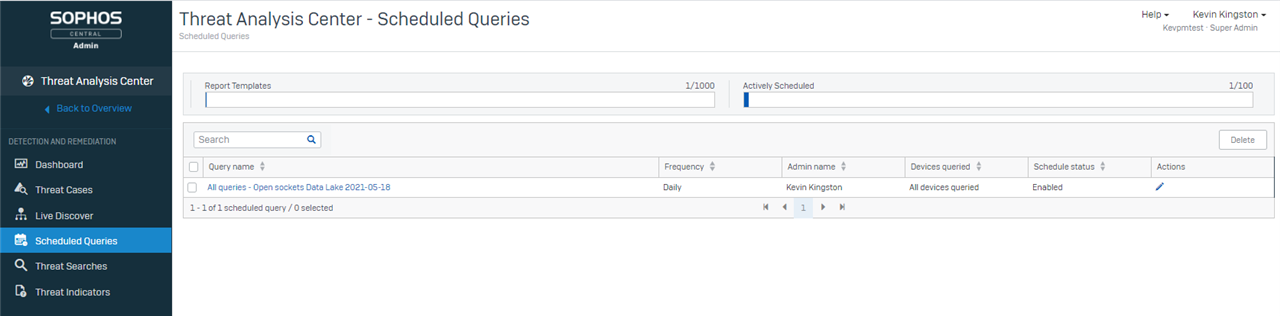
When the query has been successfully scheduled it will appear in your ‘Scheduled Queries’ list.
Intercept X Advanced with EDR のアップデート
5 月に EDR 4.0 をリリースし、ソフォスは Endpoint Detection and Response (EDR) 製品に大幅な機能拡張を導入しました。 新しい主なコンポーネントは Sophos Data Lake で、EDR 対応デバイスからの重要なデータを保存し、オフラインでもデバイス間で Live Discover を実行できるようになります。たとえば、許可なく破壊されたり、取得されたデバイス上での異常なアクティビティを遡って特定します。これはサイバーセキュリティの可視化の重要な要素であり、組織は社内環境全体を確認し、必要な領域を迅速にドリルダウンして確認できます。 Data Lake のデータ保持期間は、EDR は 7日間、 新しく提供される XDR では30日間です。Live Discover では既に最大 90 日間のディスク上に保存されたデバイスデータの保存に対してクエリを実行できますが、これはそれに追加される機能です。
Data Lake でデータのクエリを実行するには、まず Data Lake へのデータのアップロードを有効にする必要があります。 Sophos Central コンソールで「グローバル設定」を選択し、Endpoint Protection または Server Protection (またはその両方)で、「Data Lake へのアップロード」設定を選択し、「Data Lake へのアップロード」のトグルボタンをオンにします。機能を有効にすると、デバイスに対してスケジュール済みのハイドレーションクエリが実行され、脅威ハンティングに関連するデータを収集して Data Lake に送信します。 設定ページから、特定のデバイスを Sophos Data Lake へのデータ送信から除外することもできます。

ソフォスは Live Discover とクエリ機能を強化し続けており、脅威ハンティングのためには拡大を続けるソフォスのクエリセットを使用し、Live Discover の結果から調査プロセスを簡素化するための IT 運用と新しいピボット機能を提供しています。このため、既存の脅威検索および脅威インジケータ機能を強化する EDRv1 データフィードを廃止することを決定しました。 2021年 7月 1日以降、これらの機能は Sophos Central から削除されます。 以下に、Central Threat Search および Threat Indicators 機能で使用できるものと同様の結果を提供する新しい Data Lake クエリの詳細を示します。
Sophos Intercept X Community の Live Discover Query フォーラムは、ソフォスのスタッフと EDR/XDR のお客様の両方が作成した豊富な情報とクエリのソースでもあります。
|
クエリ |
説明 |
|
PowerShell コマンドのデコード |
Data Lake クエリに組み込まれている「PowerShell コマンドのデコード」は、-encodeed コマンドでエンコードされた PowerShell コマンドをデコードして一覧表示します。 |
|
SHA-256 に関連するイベント |
Data Lake クエリに組み込まれた「SHA-256 に関連するイベント」は、指定された SHA-256 ハッシュを含んだイベントに関する情報を一覧表示します。 |
|
Sophos Process ID のネットワークアクティビティ |
この Data Lake クエリは、お客様が定義して調査しようとしている Sophos Process ID のネットワークアクティビティを表示します。 クエリは、こちらのクエリフォーラムにもあります。 |
|
脅威インジケータ |
Central の脅威インジケータレポートと同様に、この Data Lake クエリは、機械学習とレピュテーションスコアを評価して、環境内で最も疑わしい実行可能ファイルのリストを提供します。クエリを調整して、この結果のリストを拡大または縮小することも可能です。 クエリは、こちらのクエリフォーラムにあります。 |
クエリのスケジュール設定:
新しい Data Lake クエリを使用するもう 1 つの利点は、重要な情報を事前に準備して待機させておくことができることです。クエリは夜間に実行するようにスケジュール設定できるため、重要なデータを翌日に評価する準備が整います。
スケジュールされたクエリを設定するには、まず「脅威解析センター」に移動して「Live Discover」を選択してからクエリを選択する必要があります。実行する Data Lake クエリを選択すると、クエリを即座に実行する代わりにスケジュール設定をしておく新しいオプションが表示されます。クエリのスケジュール設定機能は、現在 Sophos Data Lake クエリでのみ使用できます。

クエリが正常にスケジュール設定されると、「スケジュール済みクエリ」リストに表示されます。

