I'm delighted to share details of enhancements to Sophos Endpoint Adaptive Attack Protection.
What is Adaptive Attack Protection?
One of Sophos Endpoint’s critical protection components is Adaptive Attack Protection. When a “hands-on-keyboard” attack is detected, Adaptive Attack Protection dynamically enables heightened defenses. In this elevated mode of protection, actions that are usually benign but commonly abused by attackers are blocked outright. This buys time for admins to eject the attacker from their environment and restore devices to clean health.
Adaptive Attack Protection is available to all Sophos Endpoint customers, and is enabled by default in Endpoint and Server Threat Protection policies in Sophos Central.
Greater protection, more control, additional visibility
We’re introducing new capabilities to provide stronger customer protection and admin experience. The new functionality is available now.
- Greater protection. Customers now have the option to apply specific Adaptive Attack Protection blocking rules persistently via new policy settings in their Sophos Central cloud-based management console.
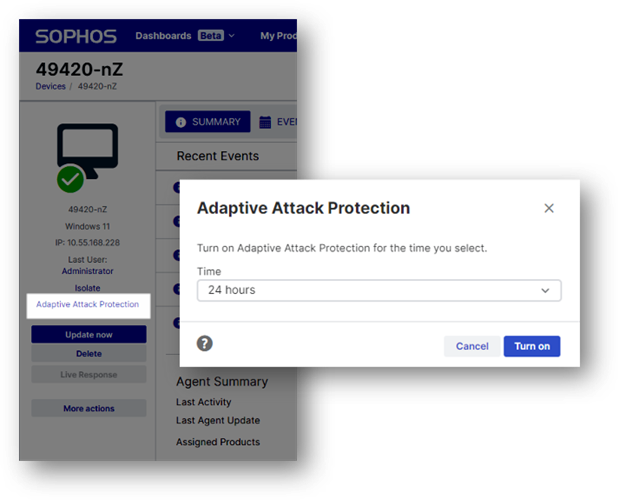
- More control. Customers can now manually activate (and deactivate) Adaptive Attack Protection on a device to apply more aggressive protection while investigating suspicious activity - ideal for scenarios where fully isolating the device from the network may cause significant operational disruption to the organization. You can also extend the time that Adaptive Attack Protection is activated on a device to give more time to complete an investigation.
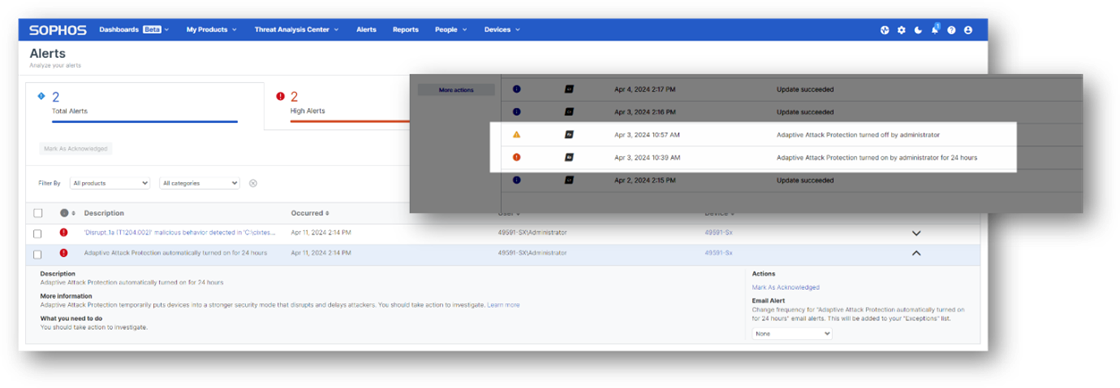
- Increased visibility. New Adaptive Attack Protection events and alerts notify you when a device is under attack and urge responders to take action to neutralize the threat.
New Safe Mode Protection
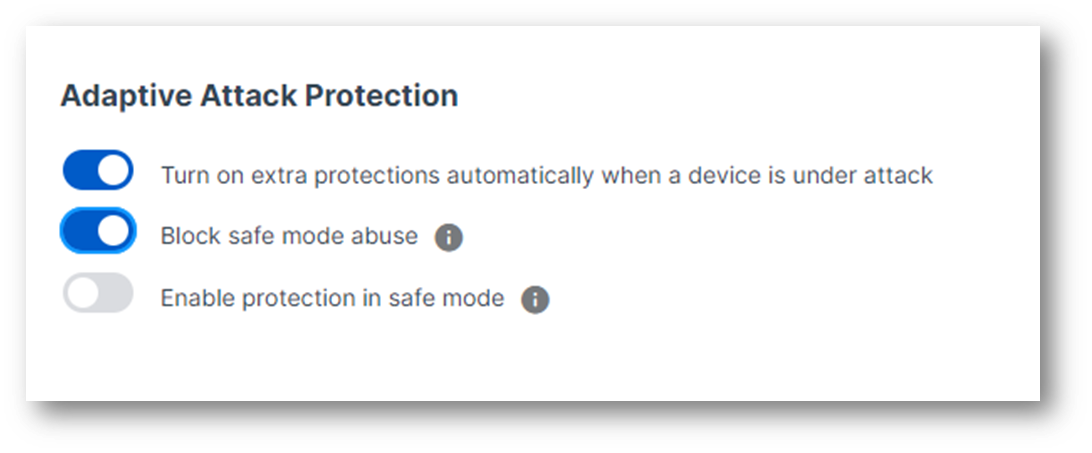
When adversaries fail to break through runtime protection layers on an endpoint, they often attempt to restart the device in safe mode, where security software is not present or minimal. Sophos Endpoint now protects against adversary abuse of safe mode with two new capabilities:
- Block safe mode abuse: A new Adaptive Attack Protection persistent policy rule is now available that prevents adversaries from programmatically restarting devices into Safe Mode.
- Enable protection in safe mode: Sophos Endpoint protection capabilities, including CryptoGuard anti-ransomware technology and AI-powered malware protection, can now be enabled on devices running in Safe Mode.
More details
This new functionality is available now for all Sophos Endpoint customers. Please see the below links for more details.
- Sophos Central admin guide: Adaptive Attack Protection
- Knowledgebase article: Adaptive Attack Protection
- Knowledgebase article: Block safe mode abuse
- Video Summary: Sophos Adaptive Attack Protection
