We’re delighted to announce the launch of Central Device Encryption 2.0 for Windows. Among the great new functionality is secure document sharing – enabling users to encrypt Outlook attachments and files before sharing them with internal or external colleagues. Admin enhancements include the ability to prompt for a BitLocker password reset, along with greater visibility into device encryption types. Read on for more details!
Please note, these features are Windows only.
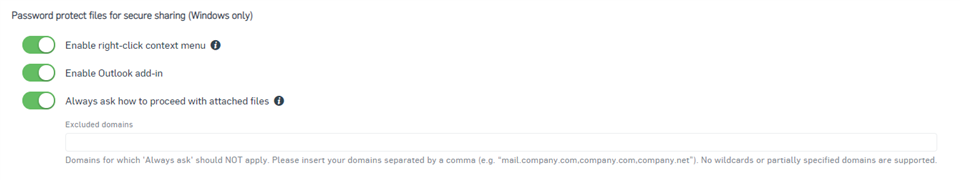
Secure document sharing
With a few clicks, users can create a password-protected file. Encrypted files can only be opened by a recipient with the correct password, they simply need a web browser and valid password to access the documents. Furthermore, a new Outlook add-in enables users to encrypt email attachments before sharing them with internal or external colleagues, safe in the knowledge they remain secure.
Trigger BitLocker password reset
Prompt users to change BitLocker passwords on a regular basis. Admins select the desired reset frequency and receive alerts for users who choose to repeatedly postpone the password change. An immediate password reset prompt can also be sent to specific devices.
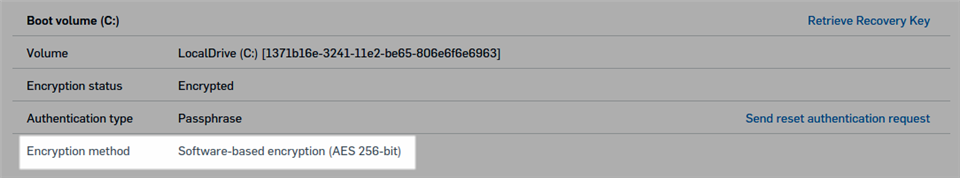
Enhanced reporting
Sophos Central now provides details of encryption type, either software-based or hardware-based, along with the algorithm used. For example, admins can see that a device’s hard drive has been encrypted using software-based AES 256-bit encryption.
Software-based encryption
Sophos Central Device Encryption will now apply software-based encryption by default, even if devices support hardware-based encryption. Note that existing devices, already encrypted with hardware based encryption, will not be affected.