Hi I am hoping someone may have come across or can point me in the right direction.
We have configured ZTNA and have been testing with web based SaaS apps and access to SMB shares to a file server on premise.
We have started to experience some issues with accessing the SMB shares as we receive messages with regards to authentication issues with the domain.
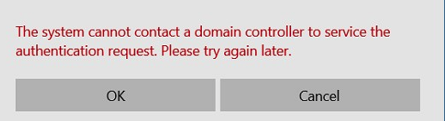
I believe this may be because the devices with the ZTNA agent installed do not have direct line of sight to the domain controllers.
I have added a number of ports via ZTNA to allow communications to the on premise domain controllers however this has not made any difference. I know you also need to allow a port range to the domain controllers however this is currently not possible within ZTNA but have seen on a forum that this is potentially coming Q2 this year.
I am just wondering if anyone else is using ZTNA to access on premise file shares? If so how do you handle authentication with the on premise domain controllers? Also how would you handle logging in if passwords etc need to get reset for a user?
We are using Azure AD as the identity provider.
The devices with ZTNA agent installed are joined to local domain and not Azure AD joined currently.
This thread was automatically locked due to age.


