ref sophos training ZTNA pages 31 & 32
I am interested in community feedback about the 2 mentioned deployments in the training material:
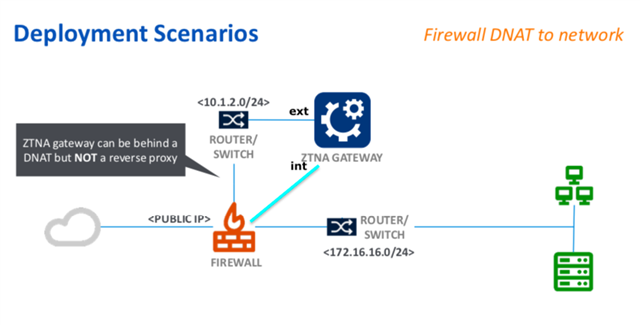
page 31: direct internet connection on gateway external nic --> I feel this should not be recommended as an architecture, the public facing interface should be secured by fw services (ddos, allow only specific inbound ports)
page 32: gateway internal nic --> for me a minimum requirement would be to have this interface also firewalled, allowing only requests from gateway to internal services to pass (dns, http(s) to published web services, ...), who else will protect your internal network in case the ztna gateway gets breached.
so to summarize, I would only recommend following architecture:
This thread was automatically locked due to age.
