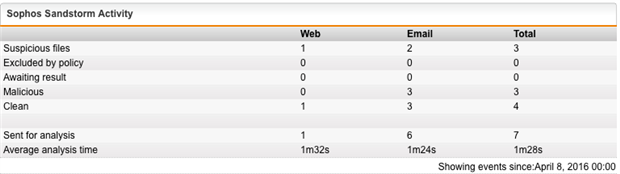
Sandstorm is finding suspicious files, but not sending them for analysis:
| Suspicious files | 1 | 2 | 3 |
| Excluded by policy | 1 | 0 | 1 |
| Awaiting result | 0 | 0 | 0 |
| Malicious | 0 | 0 | 0 |
| Clean | 0 | 0 | 0 |
| Sent for analysis | 0 | 0 | 0 |
| Average analysis time | - | - | - |
The Sandbox Activity tab shows "There is no data to display. This page lists files that have been sent to Sandstorm for analysis."
Have I set up something incorrectly?