Good afternoon,
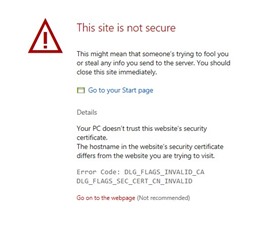
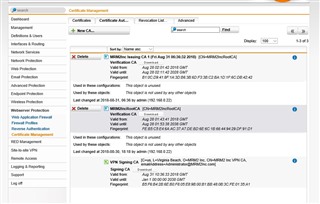
Recently I had to redo the certificates for Exchange 2013. I got the certificate from the Exchange Server and then uploaded it to the UTM. I also had user certificates that were expired, so I went to regenerate them and they still showed as expired. I then removed the user certificates leaving the local x.509 and the exchange certificate. Since then I have been getting DLG_Flags_Invalid_CA. DLG_Flags_Sec_Cert_CN_Invalid. If I check the user profiles the CA is in the trusted root of the User and Computer certificates for each machine. So I shouldn't be getting CA invalid. Though if I look at Certificate Authorities Tab in Sophos UTM, the Root CA and Issuing CA show as "This object is unused." and "This object is not used by any other objects." That I ended up doing something wrong is not a new thought to me, but I am unsure of how to fix it. Would appreciate any thoughts.
Thanks,
Mike
This thread was automatically locked due to age.