I use Sophos UTM 9 and alongside this I use Arlo Netgear cameras.
Netgear say they only need port 80 and 443 open, and all is fine when Web Filtering Standard Option is turned on. As soon as you switch this to Transparent mode, the playback of Live Streaming (which used Flowplayer and Amazon services) stops working. You can use all other functions, just live playback fails with the onscreen error message that the cameras have gone offline.
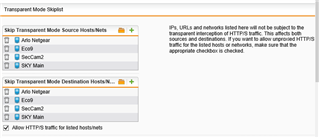
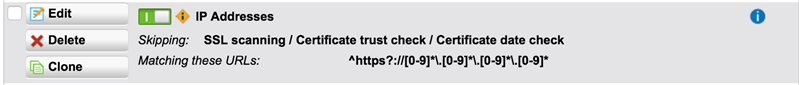
I have tried setting up an exception as follows
^https?://[A-Za-z0-9.-]+\.arlo.netgear\.com
^https?://[A-Za-z0-9.-]+\.arlos3-prod-z1.s3.amazonaws\.com
^https?://[A-Za-z0-9.-]+\.www.w3.org
^https?://[A-Za-z0-9.-]+\.angularjs.org
^https?://[A-Za-z0-9.-]+\.www.google-analytics.com
and also put arlo.netgear\.com and subdomains as a trusted site but nothing seems to work.
The weblog only shows the following
2016:01:05-22:29:27 utm httpproxy[5262]: id="0001" severity="info" sys="SecureWeb" sub="http" name="http access" action="pass" method="CONNECT" srcip="192.168.0.22" dstip="54.231.130.233" user="" ad_domain="" statuscode="200" cached="0" profile="REF_DefaultHTTPProfile (Default Web Filter Profile)" filteraction="REF_DefaultHTTPCFFAction (Default content filter action)" size="203096" request="0xdf99a800" url="arlos3-prod-z1.s3.amazonaws.com/" referer="" error="" authtime="0" dnstime="19444" cattime="0" avscantime="0" fullreqtime="13845978" device="0" auth="0" ua="" exceptions="content,url" application="amazonws" app-id="800"
Any help appreciated
This thread was automatically locked due to age.