Hello there,
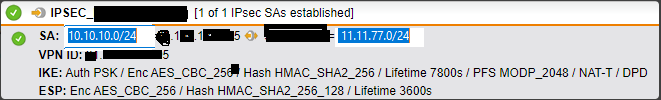
i am quite confused. We've built up a new ipsec tunnel with an external partner. He and we only defined one single network as the "local" network to have access to the external network net (eg. 192.168.66.0). There is only https traffic needed to access the partner network. Unfortunately we see that every single network in our site has access to the partners network with https (But not with other protocols). I've also backtested it. If i remove the network from webfiltering on the sophos then https traffic is blocked by packet filter. So i have my confirmation that it is about the web proxy (webfiltering). It seems as the webfiltering allows access to all network AND natting it as the partners firewall also only allows this one speciif network and not all of our internal networks. Any clues?
This thread was automatically locked due to age.