Welcome to my nightmare.
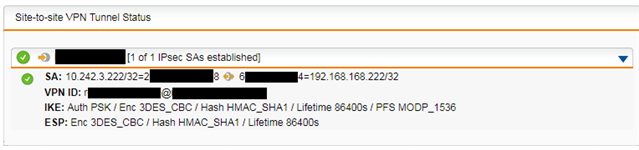
On-site UTM, remote office SonicWall. Before turning on VPN for the entire remote network, I tried to set up just a single host on the same LAN which navigates IPSec phase 1&2 successfully. The connection is up, but no traffic is being exchanged.
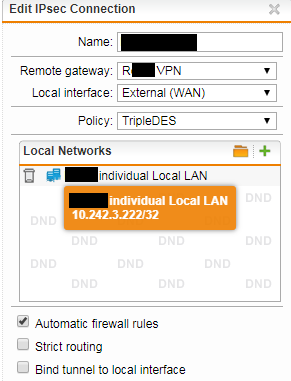
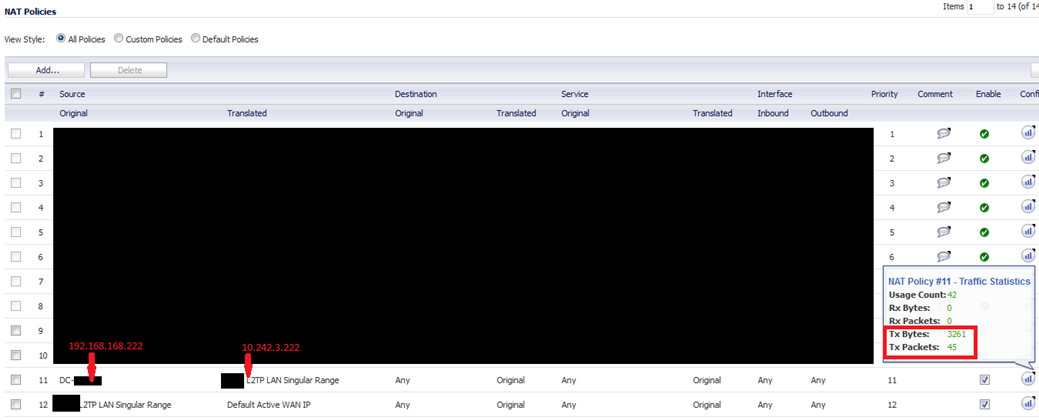
UTM local host is 10.242.3.222
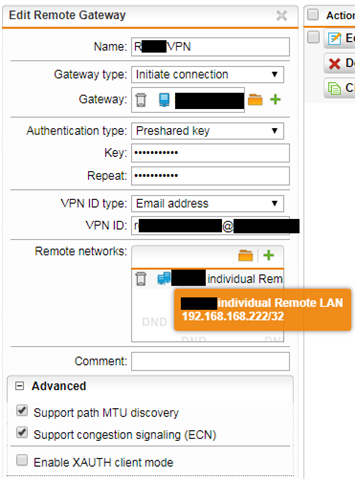
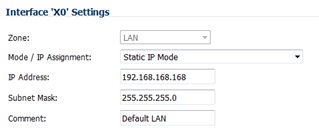
SonicWall local host is 192.168.168.222
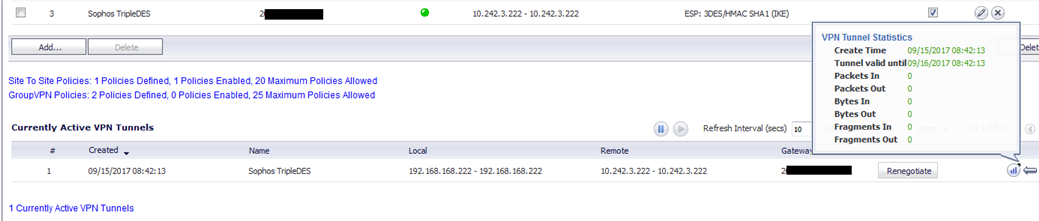
And on the SonicWall:
However I have had it configured at one point to be sending through this gateway where the packets and bytes out increment, though there is no receive traffic back.
EDIT to show NAT configuration:
NAT translation is enabled for both hosts. I have tried manually setting up every NAT and routing configuration I can think of, but no doubt there's something I'm missing since it's connected but can't communicate.
I will keep messing about with the NAT and routing configurations, but does it appear I've at least set up the LAN networks correctly for an individual host? I have to have, because it wouldn't connect otherwise, right?
This thread was automatically locked due to age.