I have a pretty basic L2TP over IPSEC VPN server running on my UTM and it constantly requires re-adjustment to work ...
I can always connect to it from a Windows 10 computer, but connecting from an iOS device only works when the iOS device is on the same LAN as the UTM.
I have other L2TP over IPSEC servers (made by Ubiquty, etc.) that never have any issues when connection from iOS devices ...
(I believe this has started to happen after iOS 14.5 but I might be wrong, as I might've just tested from my LAN instead of going through WAN)
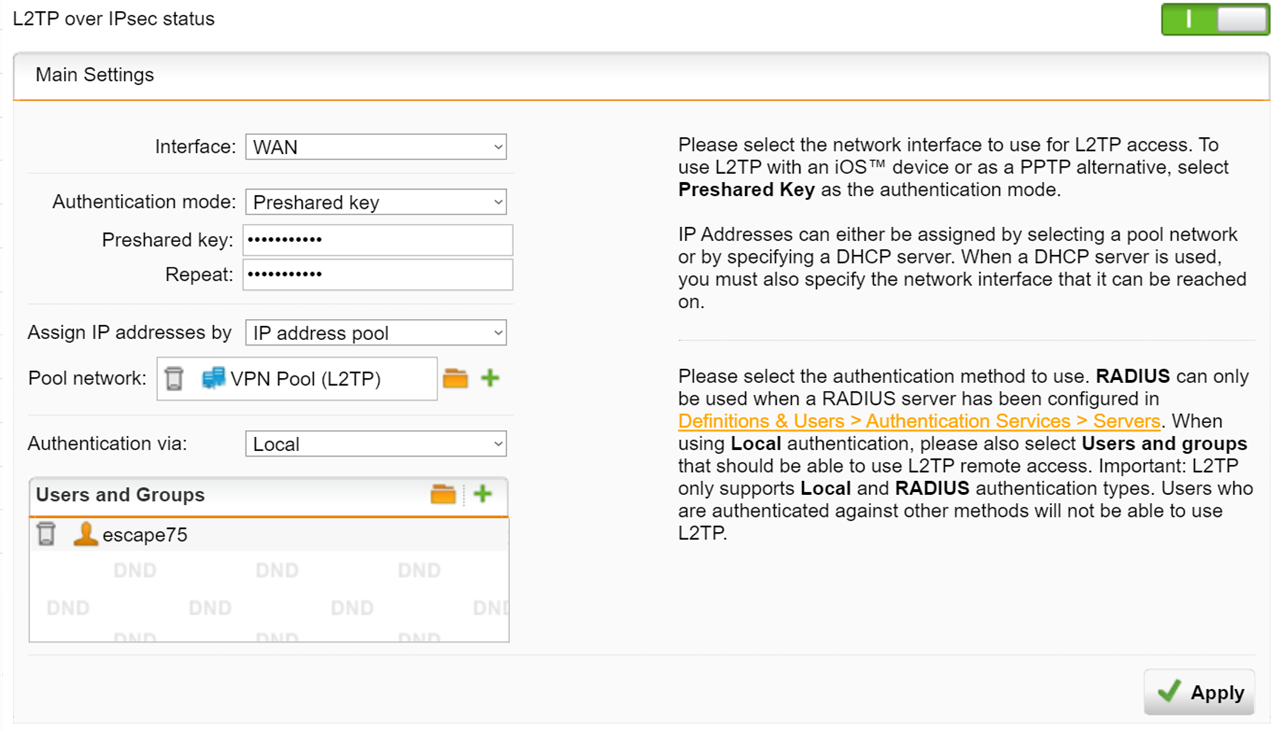
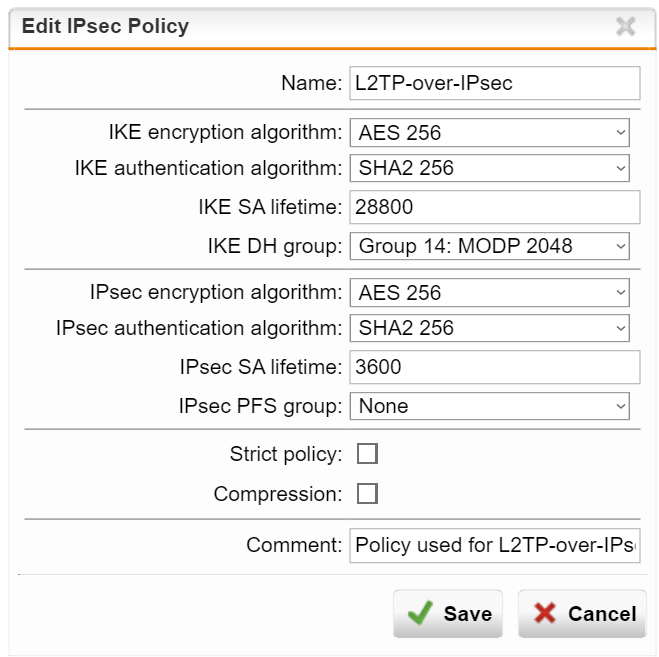
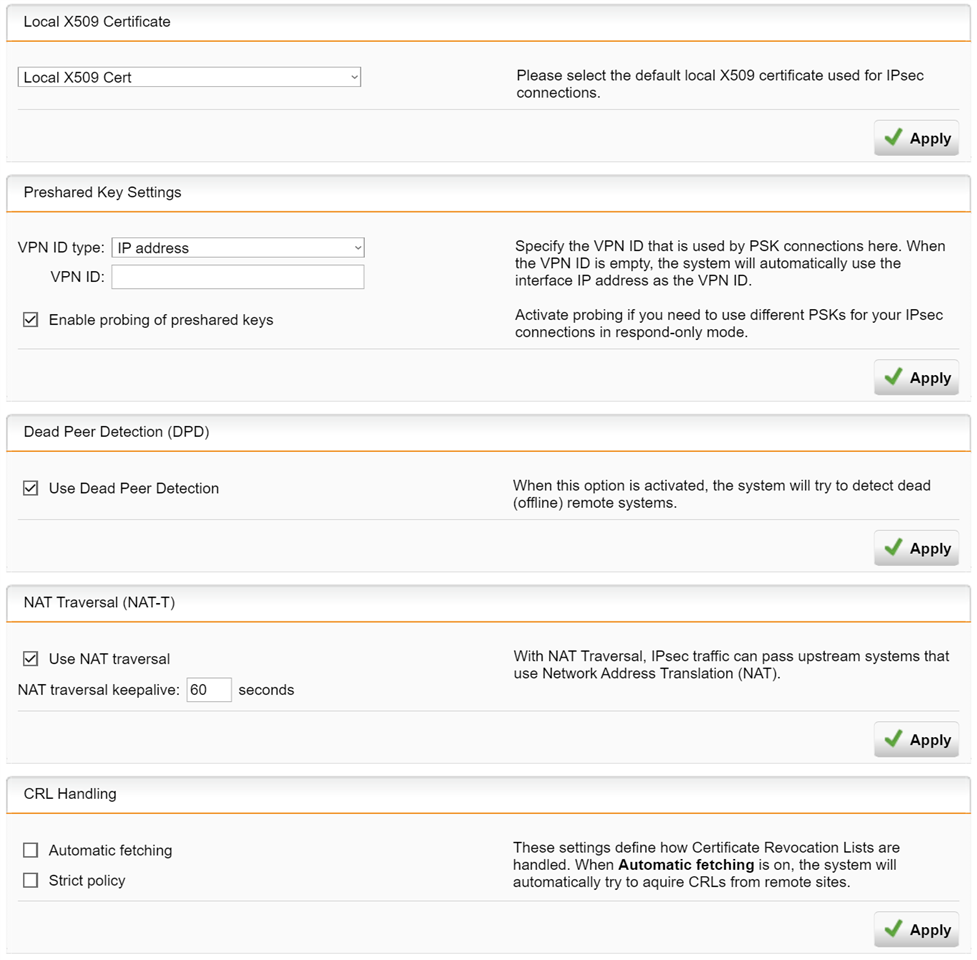
I can't think of anything else to try, I've played with the policy settings quite a bit ...
This thread was automatically locked due to age.


