Hi,
I have one question:
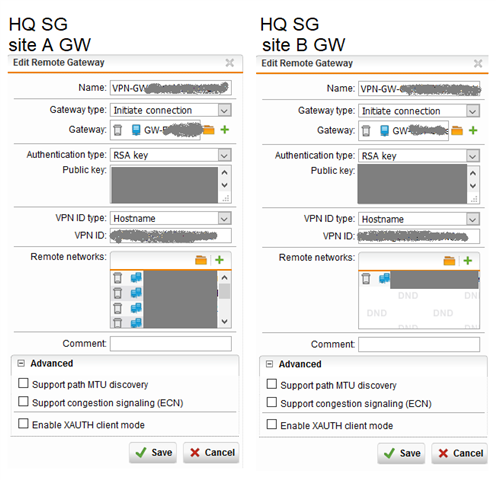
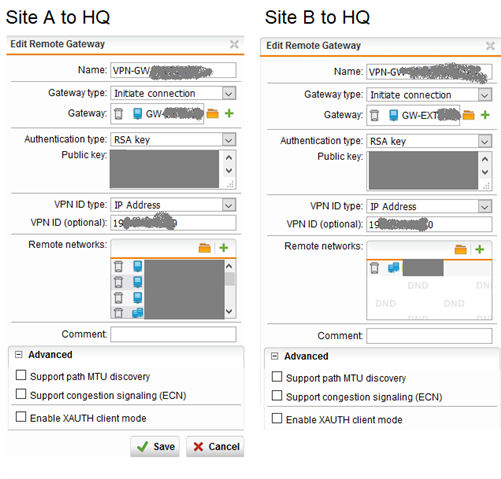
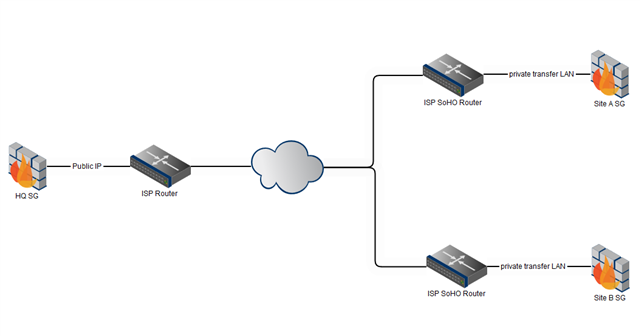
a SG 430 9.705-3 is connected to multiple other SGs via IPSec.
Today I just put in a new Network in the tunnel config of lets say HQ to Site A
The tunnel came up again but was extremely unstable - high packet loss - in fact unuseable.
On the HQ SG I looked in IPSec log for Site A and found nothing suspicious.
Then I noticed massive log flooding for site B and from the beginning of the change of site A over 900.000 - nearly a million (!) of log events like this were logged within 25 minutes:
Logs HQ to site B:
2020:11:13-17:36:45 HQ-SG-1 pluto[8732]: packet from site-B-gateway-IP:4500: length of ISAKMP Message is smaller than minimum 2020:11:13-17:36:45 HQ-SG-1 pluto[8732]: packet from site-B-gateway-IP:4500: sending notification PAYLOAD_MALFORMED to site-B-gateway-IP:4500 2020:11:13-17:36:45 HQ-SG-1 pluto[8732]: packet from site-B-gateway-IP:4500: length of ISAKMP Message is smaller than minimum 2020:11:13-17:36:45 HQ-SG-1 pluto[8732]: packet from site-B-gateway-IP:4500: sending notification PAYLOAD_MALFORMED to site-B-gateway-IP:4500 2020:11:13-17:36:45 HQ-SG-1 pluto[8732]: packet from site-B-gateway-IP:4500: length of ISAKMP Message is smaller than minimum 2020:11:13-17:36:45 HQ-SG-1 pluto[8732]: packet from site-B-gateway-IP:4500: sending notification PAYLOAD_MALFORMED to site-B-gateway-IP:4500 2020:11:13-17:36:45 HQ-SG-1 pluto[8732]: packet from site-B-gateway-IP:4500: length of ISAKMP Message is smaller than minimum 2020:11:13-17:36:45 HQ-SG-1 pluto[8732]: packet from site-B-gateway-IP:4500: sending notification PAYLOAD_MALFORMED to site-B-gateway-IP:4500 2020:11:13-17:36:45 HQ-SG-1 pluto[8732]: packet from site-B-gateway-IP:4500: length of ISAKMP Message is smaller than minimum 2020:11:13-17:36:45 HQ-SG-1 pluto[8732]: packet from site-B-gateway-IP:4500: sending notification PAYLOAD_MALFORMED to site-B-gateway-IP:4500
The problem is, that this logs belong to VPN HQ to site B, not HQ to site A where I made the changes.
Then on HQ SG I disabled the tunnel HQ to site B and site A came back to life again.
Then I reactivated site B and it came back online fine and A and B remained OK and the logs entries did not come back.
Logs site B to HQ:
2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: ISAKMP version of ISAKMP Message has an unknown value: 0 2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: sending notification INVALID_MAJOR_VERSION to HQ-SG-gateway-IP:500 2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: ISAKMP version of ISAKMP Message has an unknown value: 0 2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: sending notification INVALID_MAJOR_VERSION to HQ-SG-gateway-IP:500 2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: ISAKMP version of ISAKMP Message has an unknown value: 0 2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: sending notification INVALID_MAJOR_VERSION to HQ-SG-gateway-IP:500 2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: ISAKMP version of ISAKMP Message has an unknown value: 0 2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: sending notification INVALID_MAJOR_VERSION to HQ-SG-gateway-IP:500 2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: ISAKMP version of ISAKMP Message has an unknown value: 0 2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: sending notification INVALID_MAJOR_VERSION to HQ-SG-gateway-IP:500 2020:11:13-17:36:45 site-b-1 pluto[7109]: packet from HQ-SG-gateway-IP:500: ISAKMP version of ISAKMP Message has an unknown value: 0
I've noticed it now for the second time.
What does this logs mean?
ISAKMP version of ISAKMP Message has an unknown value
sending notification INVALID_MAJOR_VERSION
length of ISAKMP Message is smaller than minimum
sending notification PAYLOAD_MALFORMED
This thread was automatically locked due to age.