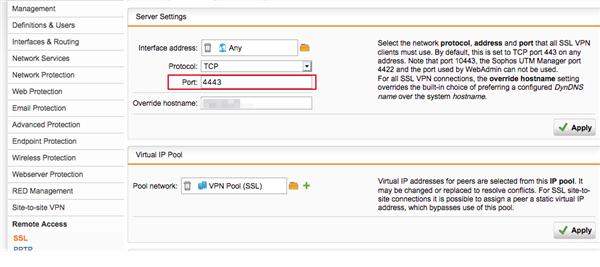
Hello
I have the following problem: if I try to connect from our internal network behind a UTM-9 to a foreign UTM-9 (or other firewall) via VPN, the connection fails with the following error:
Wed Apr 24 14:34:48 2019 TCP: connect to [AF_INET]212.xx.xxx.xxx.xxx:4443 failed, will try again in 5 seconds: The system tried to assign a drive with SUBST to a directory located on a drive mapped with JOIN.
Here is a small diagram of what I'm trying to achieve:

Does anyone know what settings I need to adjust?
Kind regards
Didier
Didier
Translated with www.DeepL.com/Translator
This thread was automatically locked due to age.