Disclaimer: The content is published as-is, without any expectation of official support or guarantees. Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
This article contains steps to create a web application firewall to allow traffic through Exchange 2016.
Important:
Officially, web application firewall (WAF) does not support Microsoft Exchange versions later than 2013. An update of Apache to a new version in our Sophos UTM 9.7 MR9 release renders it incompatible with the non-standard protocol that Microsoft uses in many of its latest products. Should you need to continue using WAF with Microsoft Exchange, see Sophos UTM: WAF not working - [proxy_http:error] read less bytes of request body than expected.
Certain infrastructure rules are the core of the WAF ModSecurity operation. You should not disable them without possibly affecting other rules built upon them. If an infrastructure rule is added to the Skip Filter Rules list, you make yourself vulnerable to other possible attacks.
The following sections are covered:
- Creating a real webserver
- Creating firewall profiles
- Creating virtual webservers
- Creating exceptions
Product and Environment
Sophos UTM 9
Prerequisite
- Microsoft Exchange 2016 must be properly configured and working.
- Configure DNS to direct traffic to the external IP address of Sophos UTM for
mail.domain.comandautodiscover.domain.comif you are using default settings. - A wildcard or SAN certificate with hostnames
mail.domain.comandautodiscover.domain.commust be uploaded to Sophos UTM so WAF can handle SSL connections to Exchange.
Creating web application firewall for Exchange 2016
Creating a real webserver
- Click +New Real Webserver in Webserver Protection > Real Webservers.
- Enter the following details as shown below:
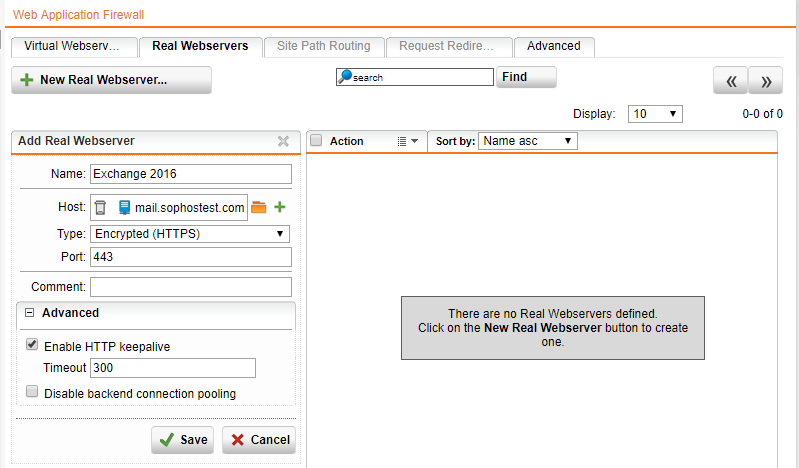
- Click Save.
Creating firewall profiles
- Click +New Firewall Profile in Webserver Protection > Firewall Profiles.
- Create the following profiles and details as shown in the examples below:
Exchange 2016 Autodiscover profile
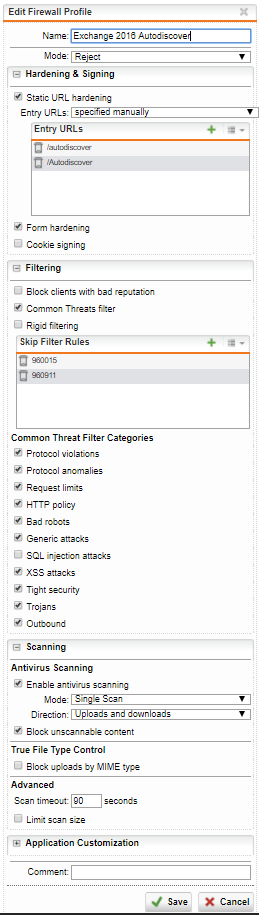
Entry URLs
/autodiscover/Autodiscover
Skip Filter Rules
960911960015
Exchange 2016 Autodiscover profile
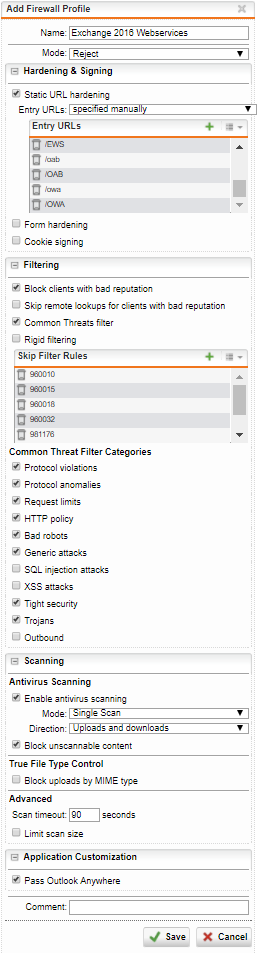
Entry URLs
//ecp/ECP/rpc/RPC/mapi/MAPI/Microsoft-Server-ActiveSync/ews/EWS/oab/OAB/owa/OWA
Skip Filter Rules
960010960015960018960032981176981203981204
Note: When saving these profiles, consider the warning for turning off some of the Skip Filter Rules.
The list of skipped filter rules contains the following required infrastructure rules: 981176, 981203, 981204. Disabling a required infrastructure rule can lead to attacks not being blocked by the Web Application Firewall.
Creating virtual webservers
- Click +New Virtual Webserver in Webserver Protection > Web Application Firewall > Virtual Webservers.
- Create the following virtual webservers and enter the details as shown in the examples below:
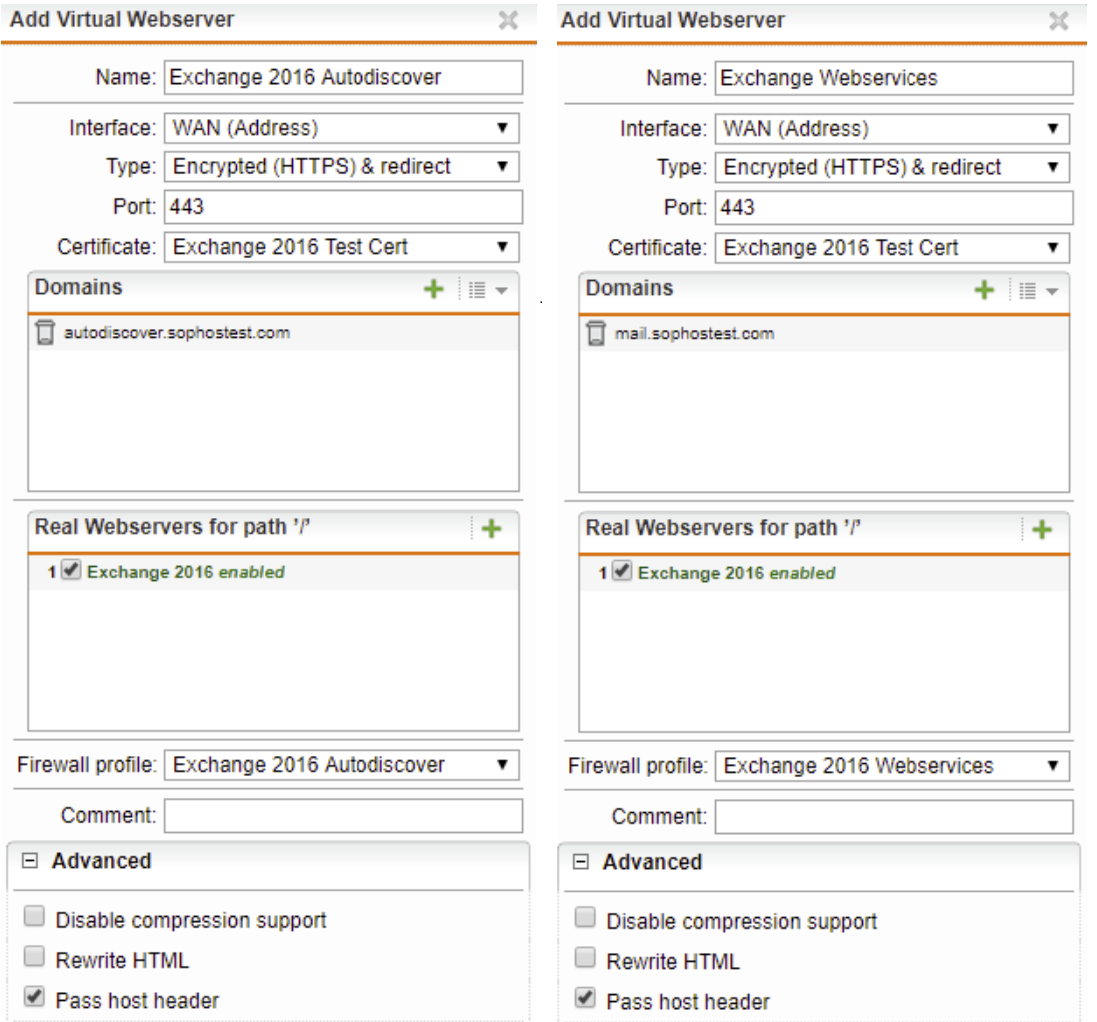
Creating exceptions
Certain exceptions need to be created for Exchange 2016 to function behind WAF.
- Click +New Exception List in Webserver Protection > Firewall Profiles > Exceptions.
- Create the following exceptions and details as shown in the examples below:
Autodiscover exceptions
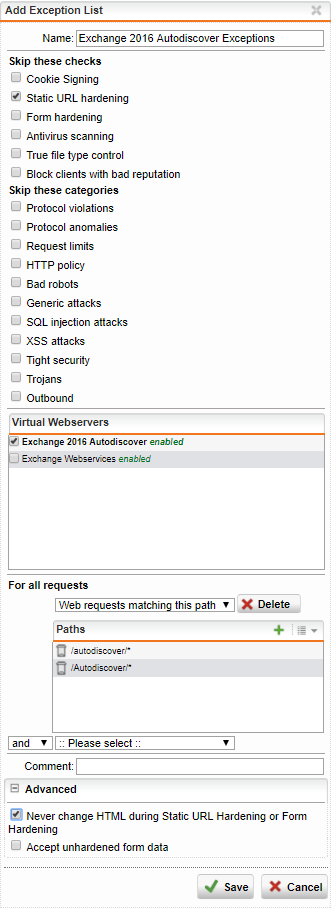
Paths
- /autodiscover/*
- /Autodiscover/*
Webservices exceptions
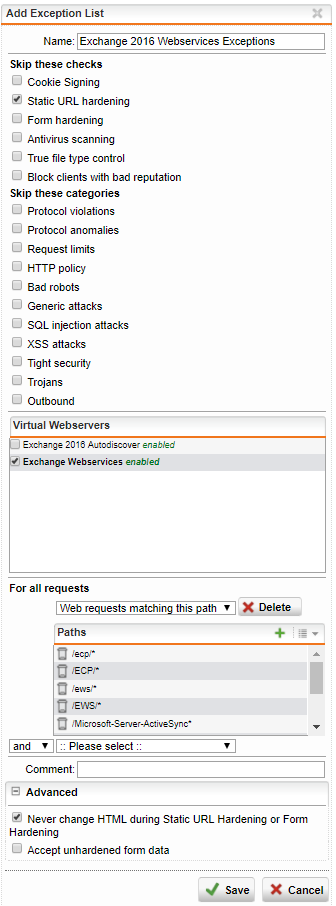
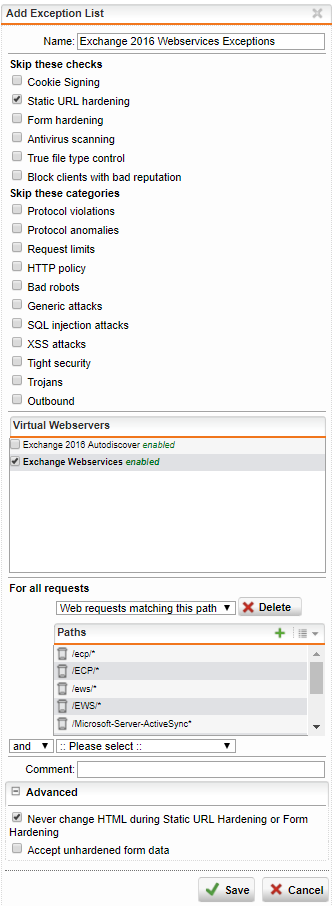
Paths
/ecp/*/ECP/*/ews/*/EWS/*/Microsoft-Server-ActiveSync*/oab/*/OAB/*/owa/*/OWA/*
OWA exceptions
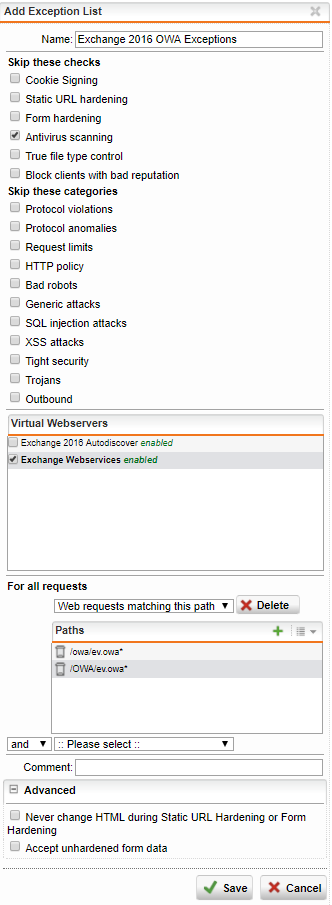
Paths
/owa/ev.owa*/OWA/ev.owa*
Outlook Anywhere exceptions
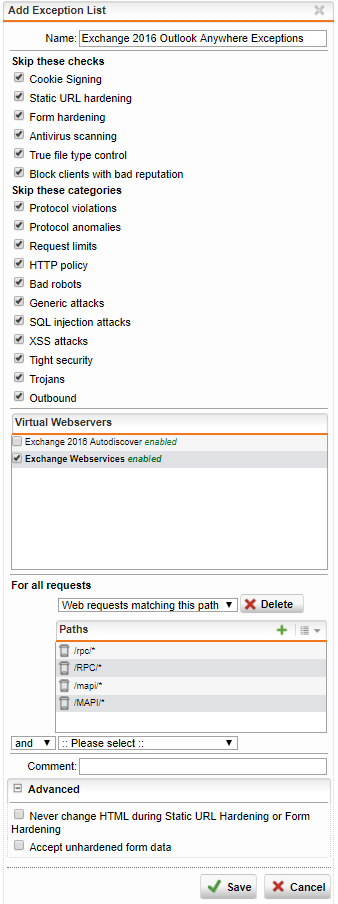
Paths
/rpc/*/RPC/*/mapi/*/MAPI/*
Related information
Sophos UTM: Configure and troubleshoot Web Application Firewall
Sign up for the Sophos Support Notification Service to receive proactive SMS alerts for Sophos products and Sophos Central services.
Missing period in the Disclaimer section.
[edited by: Dennis Huagan at 6:01 AM (GMT -7) on 15 Sep 2023]

