We are using UTM as our mail gateway, lately, a lot of our users have received spoofing emails that appear from themself.
We use emailspooftest dotcom site to test our mail servers, and it detects the problem was
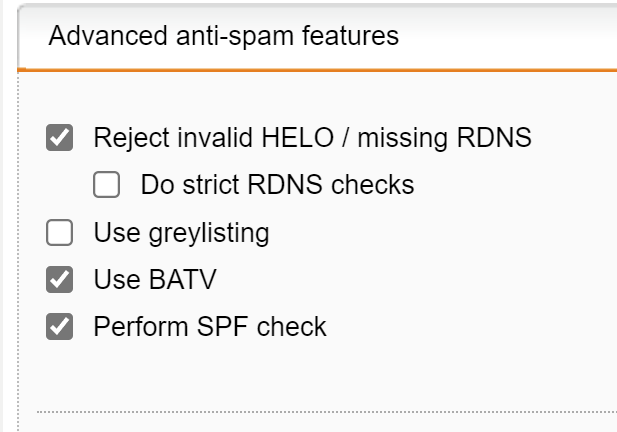
Internal authentication is not enforced.
Fix: On inbound email gateways, only allow specific IP addresses to send mail from internal domains or force an auth challenge for internal domains. This is typically a relay setting.
Could anyone suggest how to fix this problem in Sophos?