Disclaimer: This information is provided as-is without any guarantees. Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
When wireless users do not need to be part of the internal network or administrators do not want to allow them access to the internal network, configuring the Separate Zone wireless network is the best option.
This article describes the steps required to configure the Separate Zone wireless network.
Separate zone (default): The wireless network is handled as a separate network, having an IP address range of its own. Using this option, after adding the wireless network you have to continue your setup as described in the section below (Next Steps for Separate Zone Network).
Note – When switching an existing Separate Zone network to Bridge to AP LAN or Bridge to VLAN, already configured WLAN interfaces on Sophos UTM will be disabled and the interface object will become unassigned. However, you can assign a new hardware interface to the interface object by editing it and thus re-enable it.
Applies to the Following Sophos Products
Sophos UTM
Table of Contents
- Overview
- What to do
- Configure the Separate Zone wireless network
- Configure a new network interface
- Enable DHCP for the wireless clients
- Enable DNS for the wireless clients
- Create a NAT rule to mask the wireless network
- Create one or more packet filter rules to allow traffic from and to the wireless network
- Enable Wireless Protection, configure the Separate Zone interface
- Accept the Pending Access Point request and add the wireless network
- Related Information:
What to do
Next Steps for Separate Zone Networks
When you created a wireless network with the option Separate Zone, a new corresponding virtual hardware interface will be created automatically, e.g., wlan0. To be able to use the wireless network, some further manual configuration steps are required. Proceed as follows:
Configure the Separate Zone wireless network
- On the Wireless Protection > Wireless Networks > Create New Wireless Network. Select client traffic as a Separate Zone.
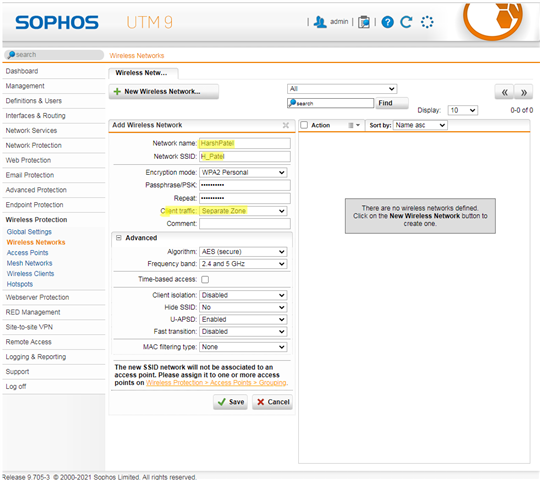
Configure a new network interface
- On the Interfaces & Routing > Interfaces > Interfaces tab create a new interface and select your wireless interface (e.g., wlan0) as hardware. Make sure that type is “Ethernet” and specify the IP address and netmask of your wireless network.
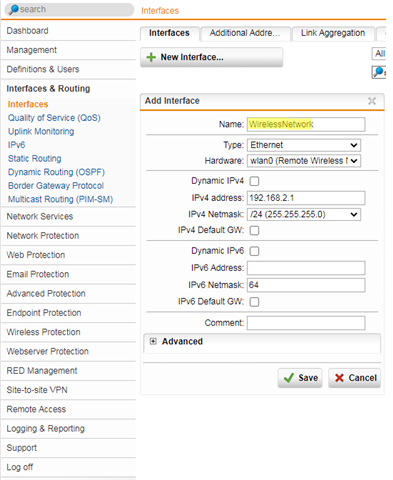
Enable DHCP for the wireless clients
- For your clients to be able to connect to Sophos UTM, they need to be assigned an IP address and a default gateway. Therefore, on the Network Services > DHCP > Servers tab set up a DHCP server for the interface.
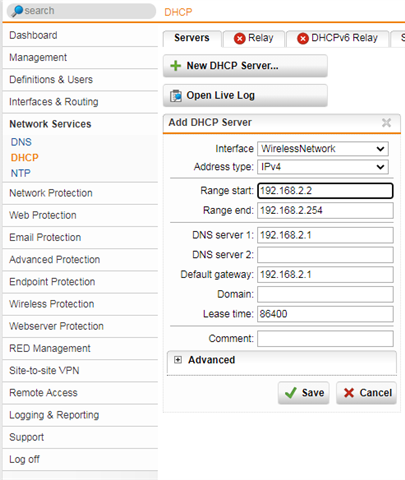
Enable DNS for the wireless clients
- For your clients to be able to resolve DNS names they have to get access to DNS servers. On the Network Services > DNS > Global tab, add the interface to the list of allowed networks.
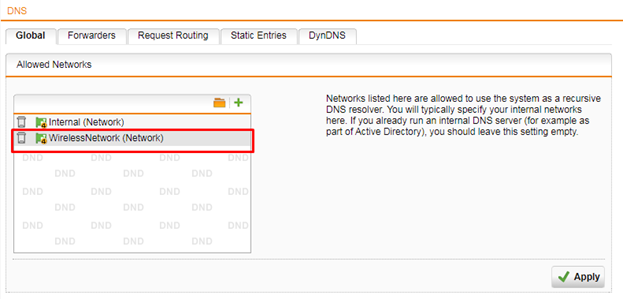
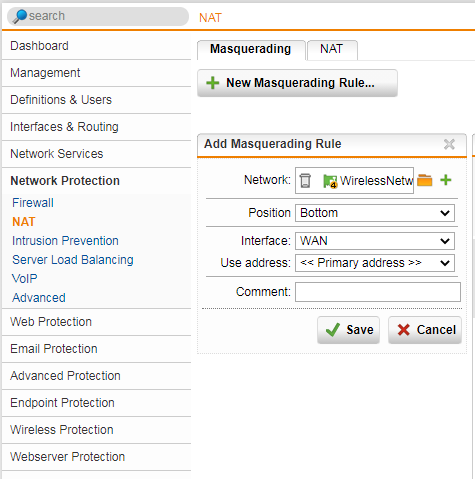
Create a NAT rule to mask the wireless network
- As with any other network you have to translate the wireless network's addresses into the address of the uplink interface. You create the NAT rule on the Network Protection > NAT > Masquerading tab.
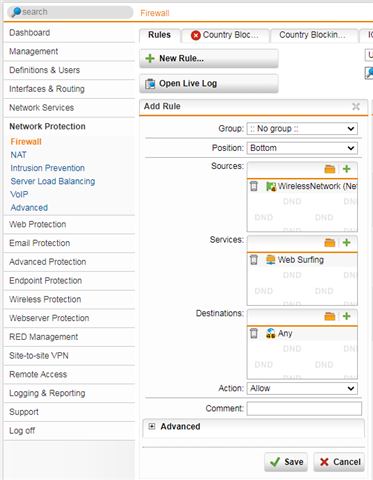
Create one or more packet filter rules to allow traffic from and to the wireless network
- As with any other network you have to create one or more packet filter rules to allow the traffic to pass Sophos UTM, e.g., web surfing traffic. You create packet filter rules on the Network Protection > Firewall > Rules tab
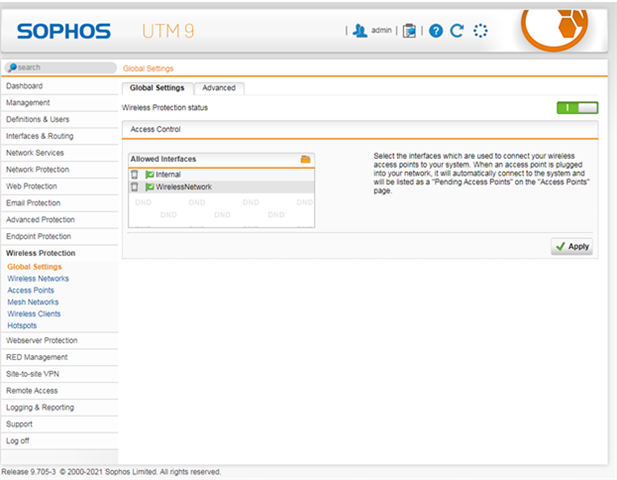
Enable Wireless Protection, configure the Separate Zone interface
- Add wireless interface under Wireless Protection > Global Settings > Access Control.
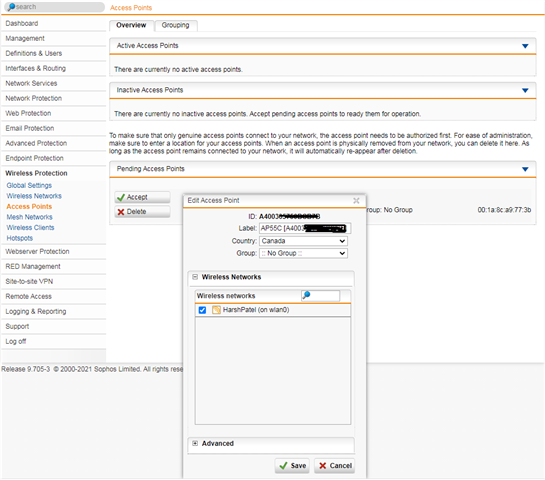
Accept the Pending Access Point request and add the wireless network
- Plug the wireless AP into the switch so it can receive a DHCP address and connect with the UTM. Once connected the AP shows up under the pending access point, Wireless protection > Access Points > Overview tab.
- Click accept and add select the wireless network. The AP will be listed under Active Access Points.
Related Information
- Sophos UTM: How to bridge a Sophos Access Point to the LAN
- Sophos UTM: How to bridge wireless AP to VLAN
- Sophos UTM Administration Guide - Wireless Networks Page 365
.
[edited by: H_Patel at 7:05 PM (GMT -8) on 4 Feb 2021]

