Note: Information is posted as-is and the content should be referenced at your own risk.
Overview
In certain scenarios it might be required to gain root access to Sophos UTM without having previously accessed the WebAdmin console. Due to AWS security policy requiring that the root account is disabled for SSH access we will need to work around limitation to get access to the system and enable root access if needed.
This article describes the steps to enable SSH access for root on Sophos UTM instances in AWS.
Note:
- Sophos do not recommend using the root user for logging in to the system or any other operation due to the risks associated with this account.
- The safe alternative is to use the
sudocommand when executing commands that require root privilege as loginuser is part of the sudo-approved users by default.
Applies to the following Sophos products and versions
Sophos UTM v9.412 and above
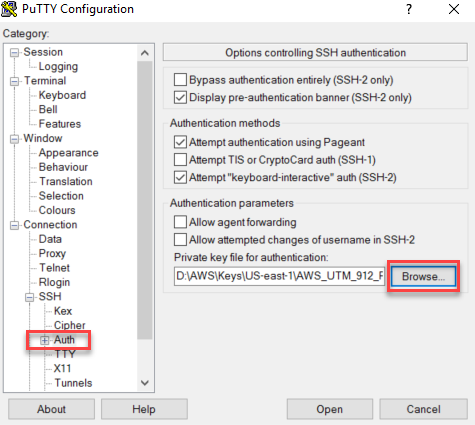
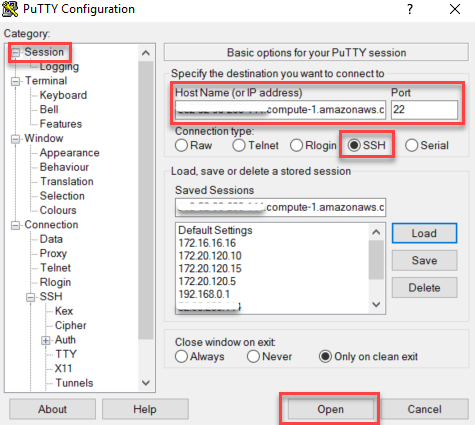
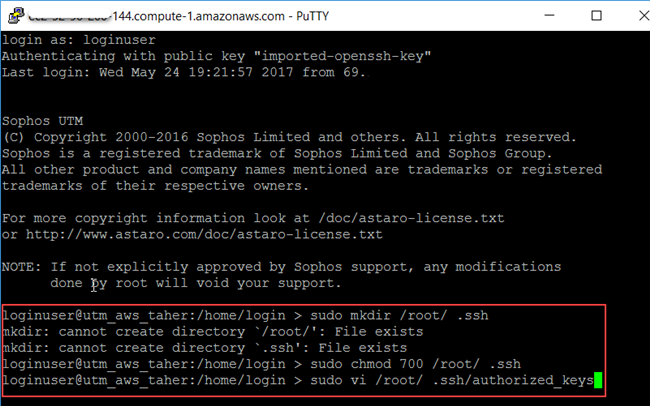
Connecting to Sophos UTM using PuTTY
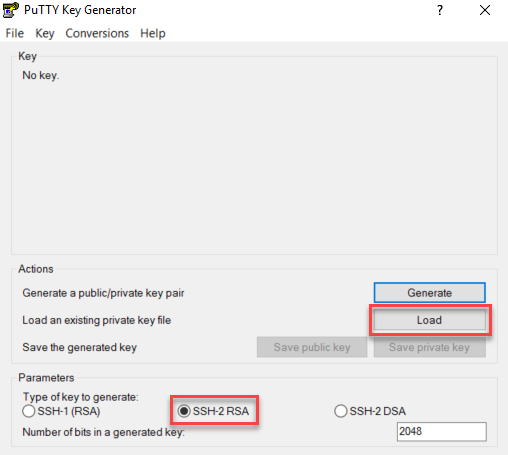
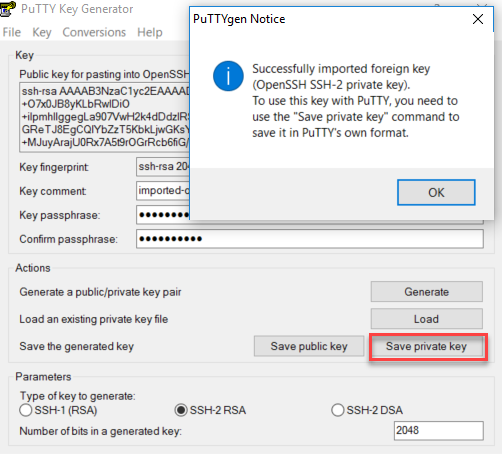
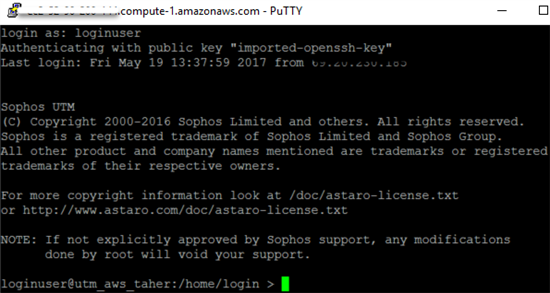
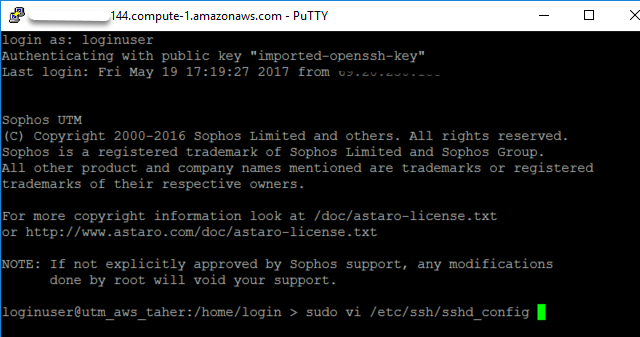
The loginuser user account has access to any UTM system launched on AWS by default. This user can sign in using the private key selected during the UTM’s deployment. Download and install both PuTTY and PuTTYGen from www.putty.org.
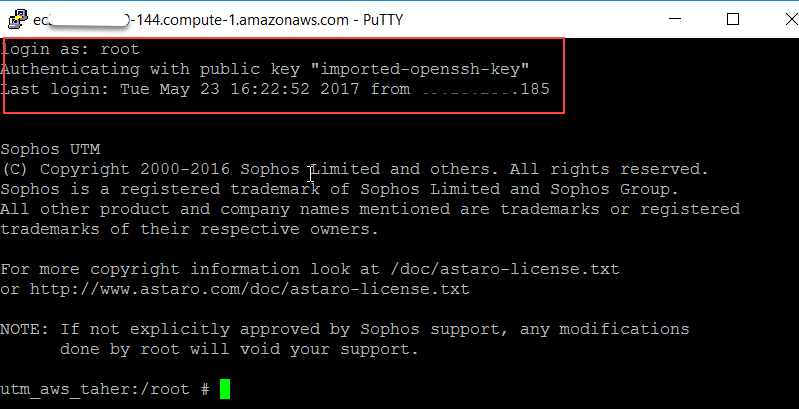
Setting up a password for root
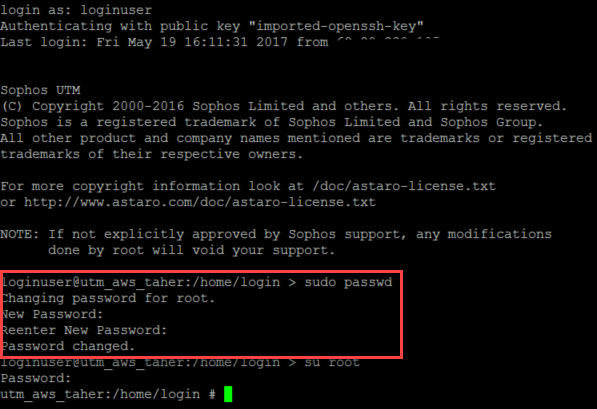
Since root uses a unique randomized password, you will need to modify this password to log in as root.
- Log in to the UTM with loginuser account as described above.
- Enter
sudo passwd root followed by <enter>. - Set and confirm a new password for the root user.
- Optionally confirm the new password by switching to root. Enter
suorsu rootcommand followed by <enter>.
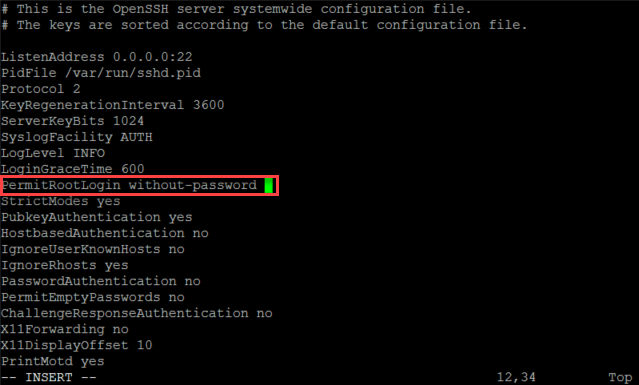
Enabling SSH login for root
If your setup requires direct SSH access to UTM with the root user, you can use one of the following methods to enable it.
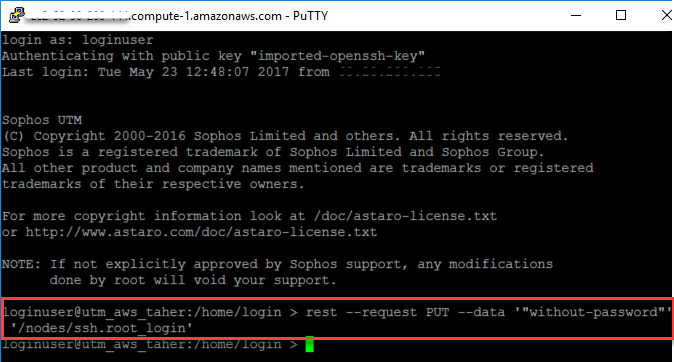
Enabling root access via SSH channel
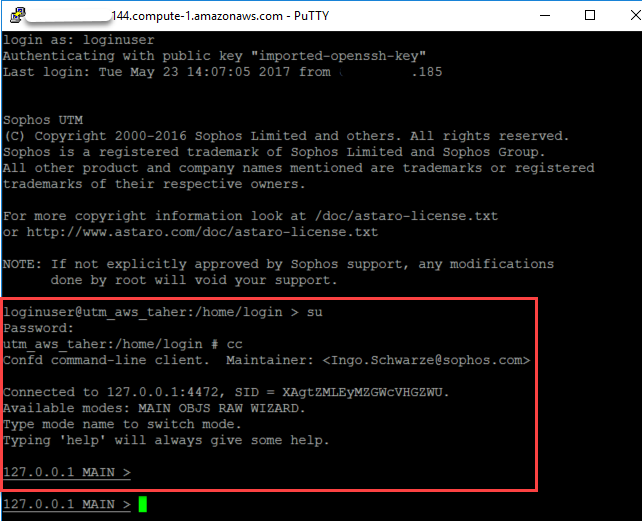
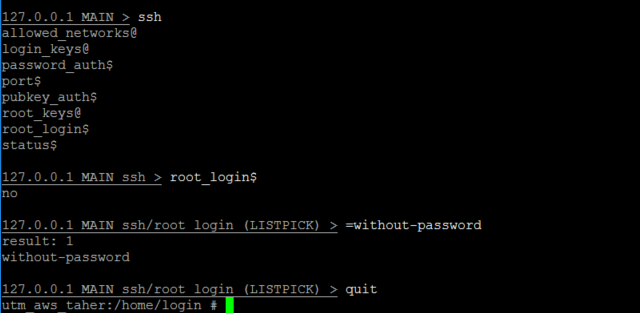
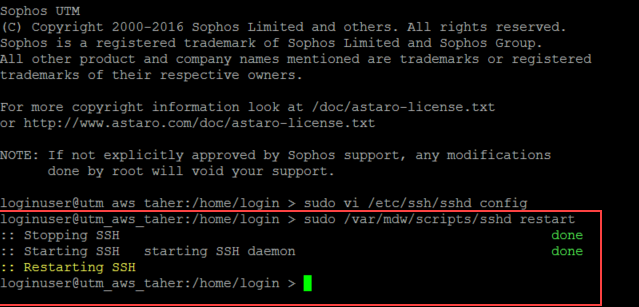
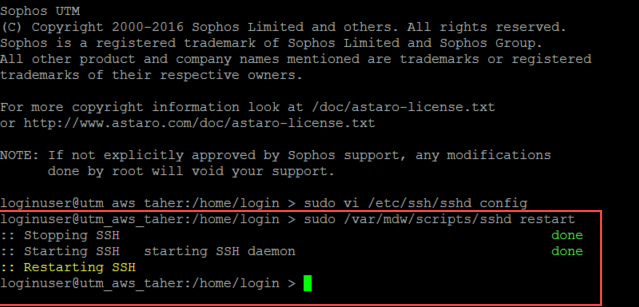
Login to the UTM using the loginuser account and run the following command:
rest --request PUT --data '"without-password"' '/nodes/ssh.root_login'
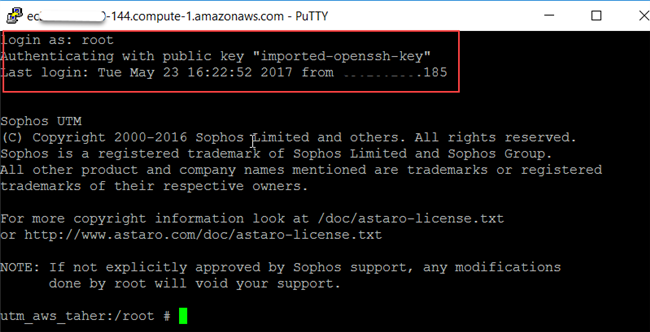
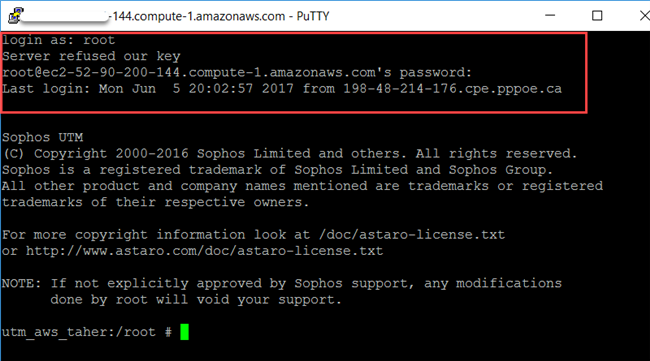
You can now set up a new PuTTY session and login as a root.
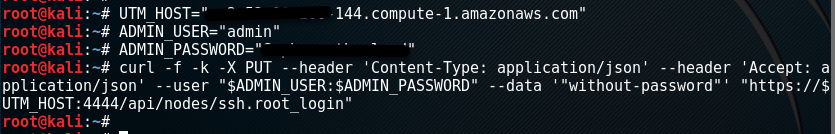
Enabling root access via RESTful API channel
From any remote application supporting RESTful API, run the following commands against your Sophos UTM instance:
UTM_HOST="utm_hostname.example"
ADMIN_USER="admin"
ADMIN_PASSWORD="your_password"
curl -f -X PUT --header 'Content-Type: application/json' --header 'Accept: application/json' --user "$ADMIN_USER:$ADMIN_PASSWORD" --data '"without-password"' "https://$UTM_HOST:4444/api/nodes/ssh.root_login"
You can now set up a new PuTTY session and login as a root.
Enabling root access using the confd client
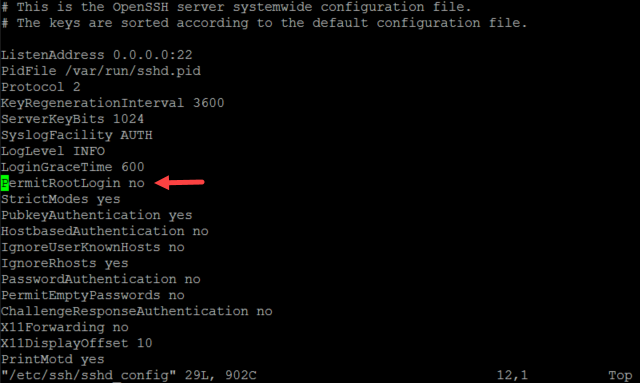
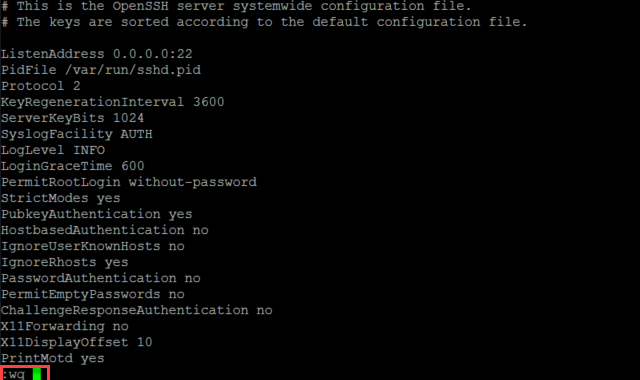
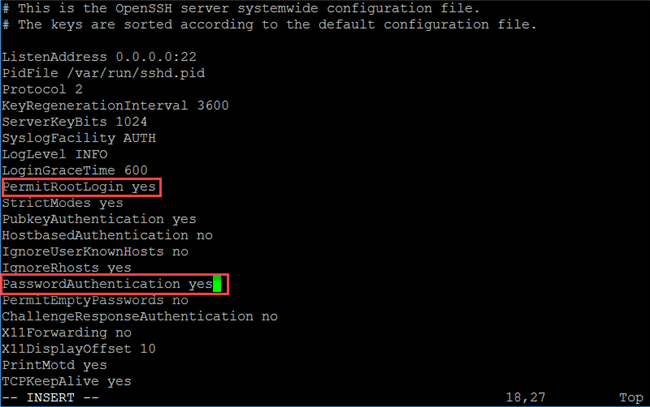
Enabling root access by editing the configuration files
Note:
- Any changes made in WebAdmin under Management > System Settings > Shell Access will erase all the changes made above.