Disclaimer: This information is posted as-is and the content should be referenced at your own risk
Special thanks to for authoring this article!
Overview
This article describes the steps to disable the HTTP trace option in the WAF module as it is by default enabled in the UTM. The steps below are needed if there is an issue with PCI compliance which affects Vulnerability CVE-2004-2320 and CVE-2007-3008.
What to do
- Connect to the UTM via SSH as a root user.
- Enter the following commands.
cc
reverse_proxy
trace_enabled$
=0
exit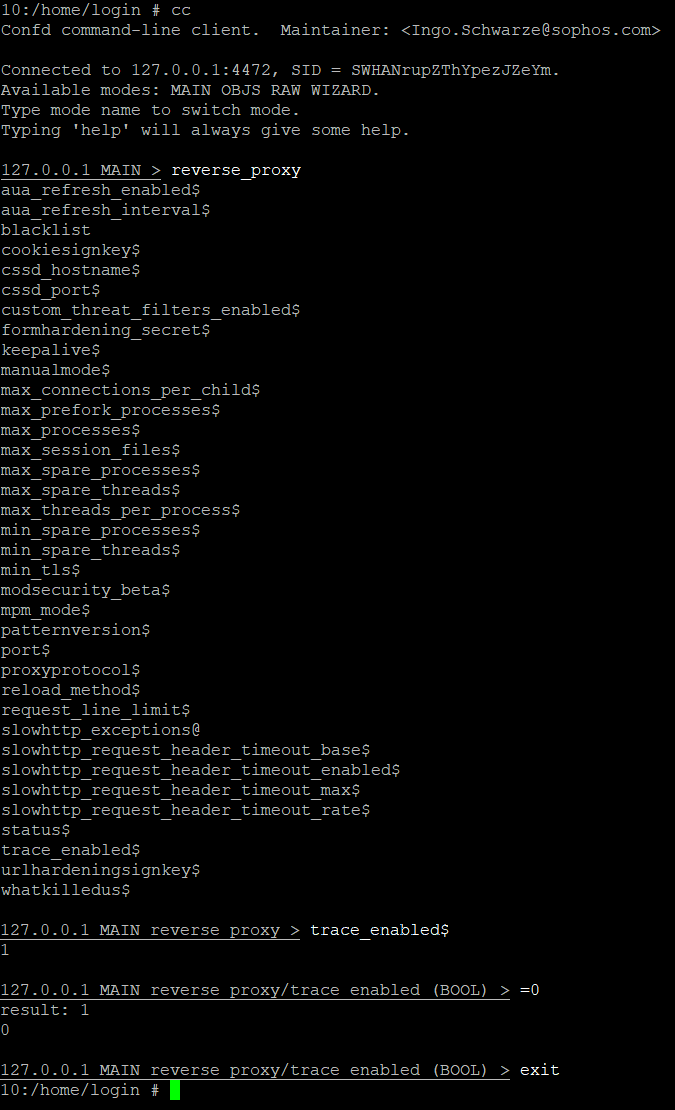
- HTTP trace is now disabled. To enable it, change the command
=0to=1. - Or you can simply enter the following command:
cc set reverse_proxy trace_enabled 1 - To check the status of the HTTP trace option, you should enter the following command: cc get reverse_proxy trace_enabled If the output is 1 it means that HTTP trace option is enabled and if the output is 0 it means that HTTP trace option is disabled. You should get output zero after following the steps mentioned earlier.
Using the above steps, you should be able to disable the HTTP trace in the Reverse proxy module of Sophos UTM. You can always Open a Support Case to contact Sophos Technical Support if you need any assistance.
Reference
https://community.sophos.com/kb/en-us/135031
Have a suggestion for a new video? Please visit our User Assistance forum on the Community to share your idea! https://community.sophos.com/community-chat/f/user-assistance-feedback
