Hello,
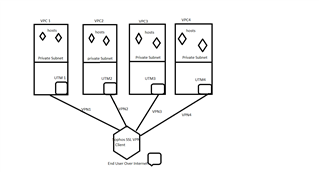
We have multiple accounts/vpcs for AWS and we use UTM as our main entry point to all the VPCs. We have SSL VPN to login to the ec2 instances.
Problem is that we have to disconnect from one vpn to go to other vpn. We are using sophos VPN client. Is there a way to connect to multiple VPNs (in Sophos)
with same Sophos Client. We are using non-overlapping subnets in all the VPC.
Thanks,
This thread was automatically locked due to age.