Hi,
I've got a small home network consisting of UTM9 running on a CI323 connected to an Archer C7 router running OpenWRT, and I'm trying to add a guest Wifi, but I'm struggling with isolating the VLANs. Broadly, the setup is this:
UTM:
- Eth1: WAN
- Eth0: VLAN 2 (Trusted) - DHCP: X.X.21.XX
- VLAN 6 (Guest) - DHCP: X.X.22.XX
Router:
- VLAN 2 (Trusted): 2x SSID and all physical network ports
- VLAN 6 (Guest): 1x SSID
- VLANs are trunked via the WAN port with firewall rules isolating them from each other
At the moment the VLANs are working, I get to the right DHCP server (and therefore end up in the right subnet) depending on the connection I use to get to the router, and both VLANs can get to the external internet. The problem is that I can reach web servers between the VLANs, both by ping and HTTP. So far I'm pretty sure the UTM is the culprit, as when connected to the trusted VLAN a traceroute shows no hops via the UTM, whereas when connected to the guest VLAN the traceroute shows an additional hop via the guest VLAN IP of the UTM.
EDIT: Also, when I turn the UTM off, I can't get between VLANs, and SSH doesn't cross even when the UTM is on, which makes me even more sure it's the UTM.
So far, based on searches of the forum, I have:
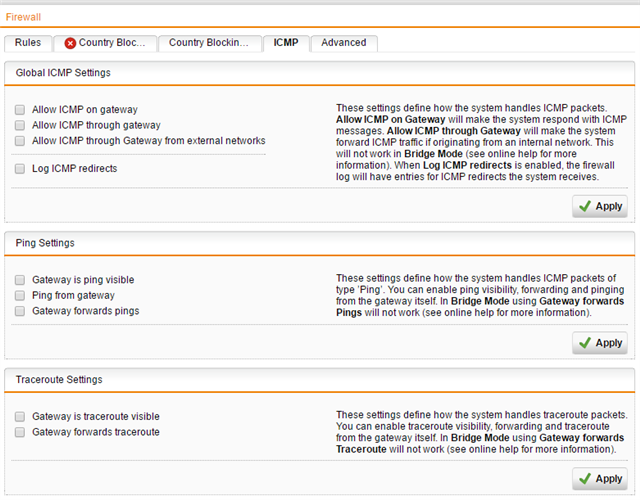
- Disabled "Allow ICMP through gateway", "Gateway forwards pings" and "Gateway forwards traceroute"
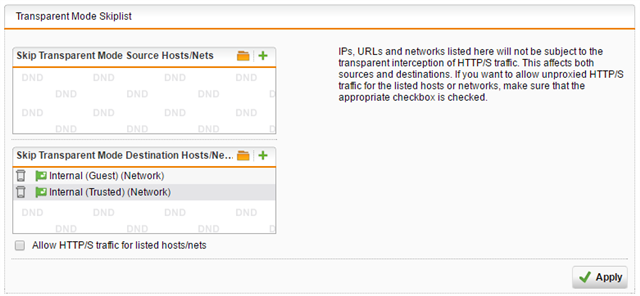
- Added both VLANs to the destination section of the Transparent Mode Skiplist and unchecked "Allow HTTP/S traffic for listed hosts/nets"
- Made sure I haven't got any firewall rules that could be letting things through, including replacing "Any" with "Internet IPV4" where relevant
At this point I'm not sure how to proceed, so any suggestions would be greatly appreciated!
Thanks,
Jamie
This thread was automatically locked due to age.