Hi everyone,
this is not a technical issue but a desparate call for advise.
Our Sophos UTM-firewall (firmware version: 9.816-2) is suffering from a (D)DOS-attack that is going on for several days now. Since our internet-connection only comprises of a 10 MBit SDSL-line that is easily filled up to the max with incoming requests (almost exclusively https-requests targeting our Exchange server which is fortunately protected by the UTM's WAF), the internet connection is clogged up, and we have difficulties with our SIP-trunk which uses the same line and remote workers connecting to a remotedesktopserver by remote-access VPN.
I have my DOS-Flooding protection in IPS set up as depicted in the following screenshot:
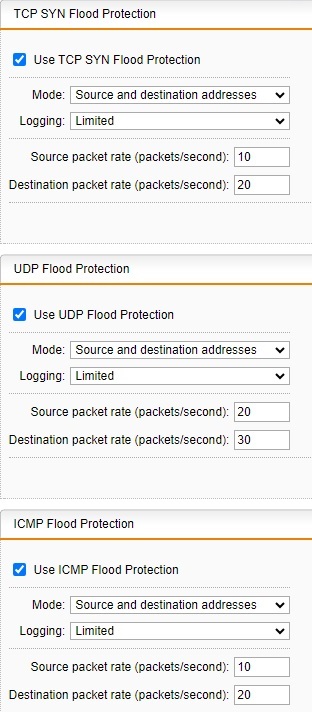
Policy and restart policy are set to "drop silently" and "drop all packets" respectively.
There are of course some exception, but only for our SIP-Trunk and MS Teams.
I also have set up a packet filter rule which is blocking the whole nets (it's only a few providers from which the connections are coming in) from which the connections originate, but still the UTM's external interface is showing spikes of data transmission coming from outside to the firewall, making it look something like this:
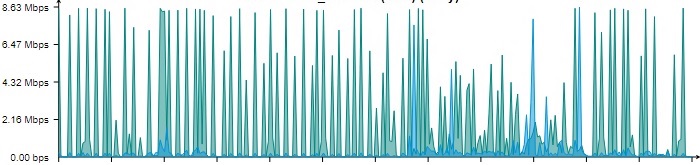
I already contacted the respective ISP's abuse emails, but so far no one dignified me with an answer.
Is there any other way to cope with the external interface being flooded?
Regards
Tobias
This thread was automatically locked due to age.

