Hi there,
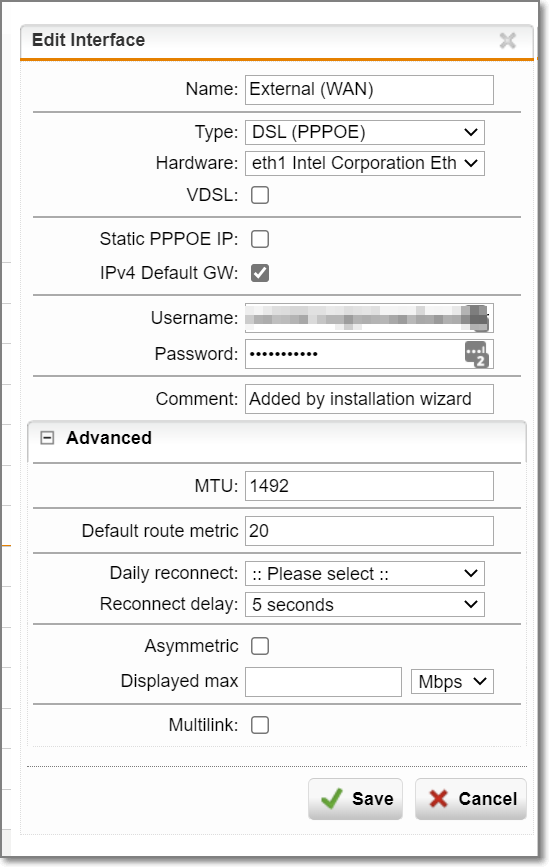
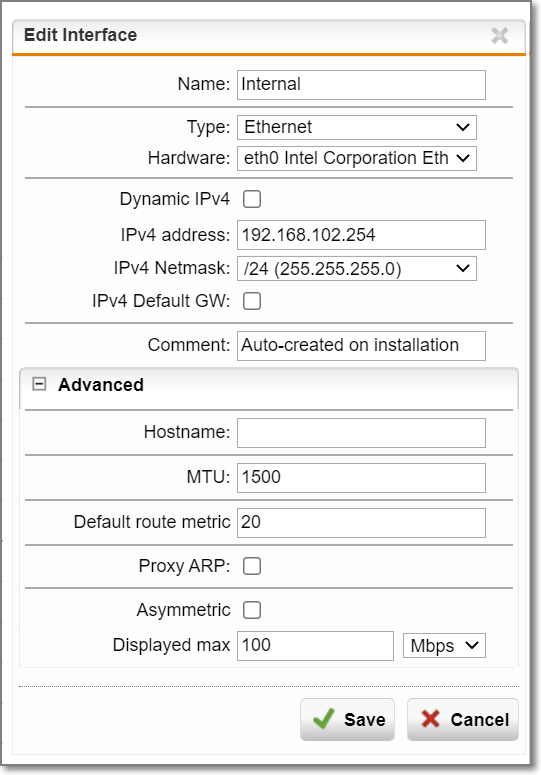
I have a Sophos SG125 UTM and until now it has had 2 interfaces configured - eth0 Internal LAN (192.168.102.X/24) & eth1 WAN (PPPoE)
I haven't had any need for open external ports up to this point.
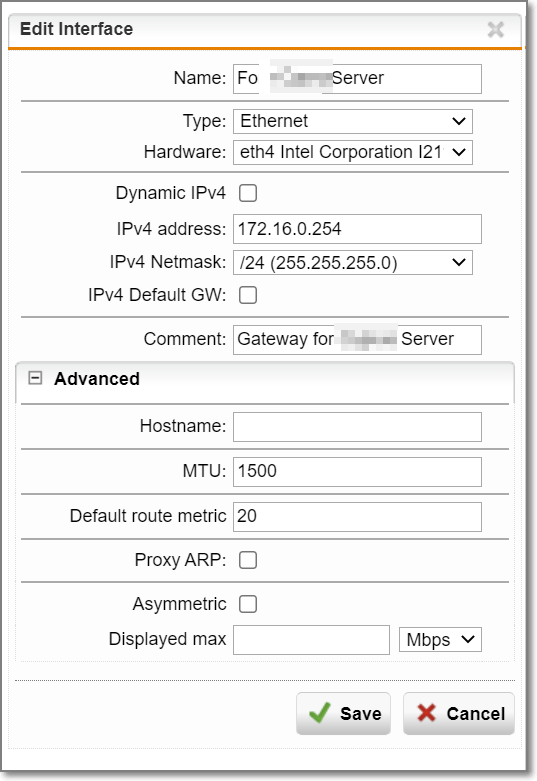
I have now added a VM on to our Hyper-V server and allocated a physical NIC to a dedicated Virtual Switch for this server. This physical NIC is directly connected to eth4 on the SG125. eth4 is configured with the IP address 172.16.0.254/24 and the new VM is configured with the IP address 172.16.0.1/24.
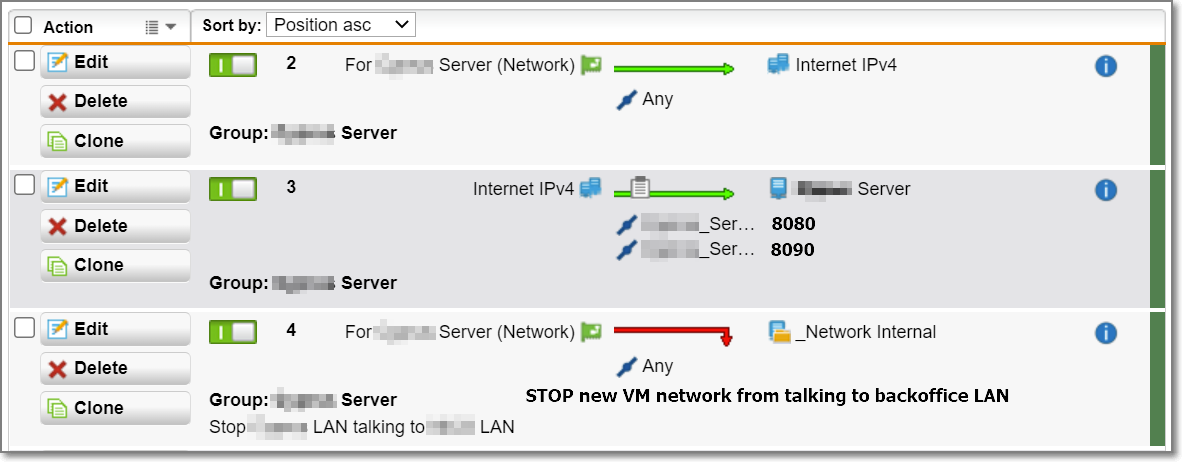
Internet browsing & Teamviewer etc is working fine on the new VM but I have to open 2x TCP ports (8080 & 8090) on the SG125 for this server. I have created firewall rules in the usual manner but the firewall is dropping all traffic on TCP 8080 & 8090.
Firewall rules are in
Network Protection > Firewall > New Rule >
Source: ANY
Services: Defined TCP 8080 & 8090
Destination: Definition for new Server
Action: Allow
Is there something else I have to do?
Many thanks in advance for any help offered.
Paul.
This thread was automatically locked due to age.