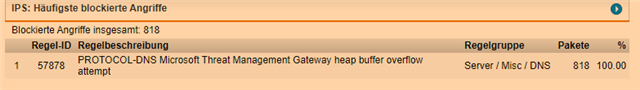
Am I the only one plagued by this. 500 alerts in a couple of hours over a 10 year old vulnerability.
rule now set to drop and notify off. It is not one awsdns server. It looks to be all of them.
Details about the intrusion alert:
Message........: PROTOCOL-DNS Microsoft Threat Management Gateway heap buffer overflow attempt
Details........: https://www.snort.org/search?query=57878
Time...........: 2021-07-17 11:47:19
Packet dropped.: no
Priority.......: high
Classification.: Attempted User Privilege Gain
IP protocol....: 17 (UDP)
Source IP address: 205.251.192.220 (ns-220.awsdns-27.com)
This thread was automatically locked due to age.