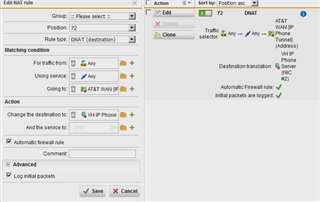
Hello everyone,
So the problem I am experiencing is very strange and I'm not sure what it indicates is happening. I have a single network setup internally that is completely different than any of my other internal networks (192.168.28.0 /24) and what I am trying to do is give that network and the one resource that is using it (a MiCollab phone system server) the ability to be accessed over the internet.
The DNAT I have set up appears to be working because when I try communicating with that server from the outside (using a port scanner or a trace route at the moment) I can see from the firewall logs that the traffic is being processed by the NAT entry. Unfortunately, all traffic that is using that particular DNAT is being tagged as "spoofed packets" and end up getting denied. This "spoofed packet" message is one I've never seen before and I'm not sure why the traffic would be getting identified as such.
As far as I know, the network I chose to setup (192.168.28.0 /24) is not in use anywhere else internally, which is what some other posts suggested checking for regarding the spoofed packet messages, and so since that isn't the case I am at a loss for understanding what is happening and how to correct it.
All other external traffic to all of my other internal networks and servers is working normally as usual. This new network (192.168.28.0 /24) was a recent addition to the configuration and external traffic to it, is the only traffic displaying the problem behavior. Internally, the firewall has no problem communicating with the VLAN on the core switch or with the phone server on the other end (via pings or trace routes).
Anyone have any ideas as to what might be going on? (a sample of the firewall log is pictured below for clarity).
Thanks in advance!
This thread was automatically locked due to age.